
Ivanti is the gift that keeps on giving to cyber-attackers, taking three of the top ten spots in Qualys’ list of most exploited vulnerabilities.
The exploit hit parade came in the security vendor’s 2024 Midyear Threat Landscape Review, which also showed that in the first half of the year, the “annual count of reported Common Vulnerabilities and Exposures (CVEs) rose by about 30%, from 17,114 in 2023 to 22,254 in 2024.”
Of these, just 0.91% were “weaponised”. Of the 204 weaponised CVEs, only a quarter (54) made it onto CISA’s KEV list, while just six were exploited by ransomware.
Which might seem reassuring, if it wasn’t already clear how cataclysmic an effect just one exploited vulnerability can have.
See also: 1 Citrix bug alone triggered 13 “nationally significant” UK cybersecurity incidents
And, the figures showed, there was a 10% increase in the weaponisation of old CVEs, highlighting just how long a tail cyber-attackers have to play with.
The security firm said the increase in CVEs “reflects rising software complexity and the broader use of technology, necessitating advanced and dynamic vulnerability management strategies to mitigate evolving cybersecurity threats.”
At the same time, the small number of vulns that are weaponized illustrates how “it's crucial to prioritize actively exploited vulnerabilities, leverage threat intelligence, and regularly schedule scans to detect new vulnerabilities.”
Moreover, the firm said, “a select group of vulnerabilities have emerged as particularly prevalent targets for cyberattacks. These vulnerabilities highlight trending attack vectors and underline the urgent need for robust defensive strategies.”
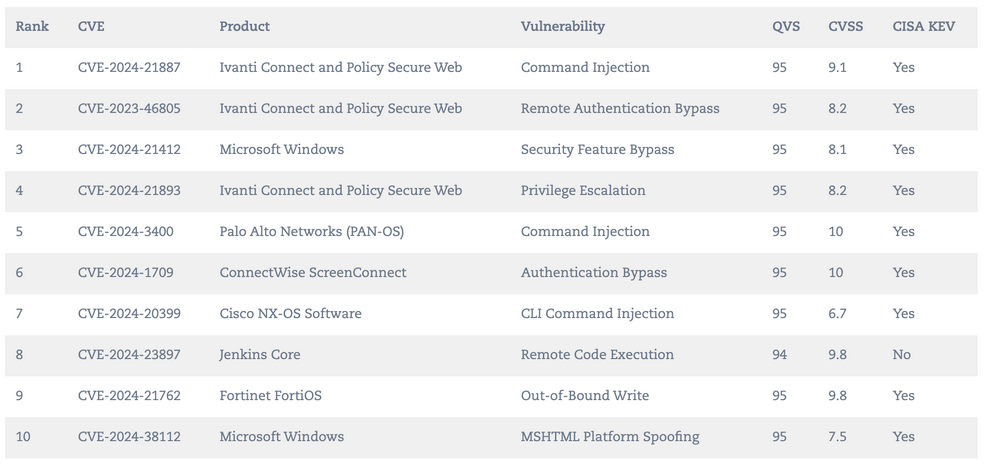
Just how much mayhem a clutch of bugs can cause is illustrated by the Top 10 Exploited chart in the report. The top two spots were taken by CVE-2024-21887 and CVE-2023-46805, both related to Ivanti Connect and Policy Secure Web, the former representing command injection, the latter a remote authentication bypass. They were initially spotted by security researchers at Volexity, which identified attacks by a Chinese state level actor, and were rapidly exploited at scale as of January.
A privilege escalation in the same product – CVE02024-21893, took the third sport.
The situation was compounded when Ivanti admitted patches would take weeks to arrive. CISA eventually told Federal agencies to simply disconnect Ivanti products by February 2.
