Eighteen ransomware incidents this year have required a nationally co-ordinated response the National Cyber Security Centre (NCSC) revealed – pointing to attacks on MSP Advanced and South Staffordshire Water.
Some 63 other cyber incidents meanwhile were “significant enough to require a national level response.”
The numbers were disclosed in the NCSC’s annual review for 2022.
The NCSC report also disclosed that efforts by the government over the past five years to map and strengthen Critical National Infrastructure (CNI) “including their interdependencies and supply chains” this year had “allowed the government to identify previously unknown CNI systems.”
It did not disclose what those “previously unknown” systems were – e.g. whether they were infrastructure not previously thought to be critical, or components within existing CNI not previously mapped as critical dependencies. (NCSC declined to offer more information when asked by The Stack on the newly identified CNI.)

It appears plausible that the NCSC may be referring to certain co-location data centres.
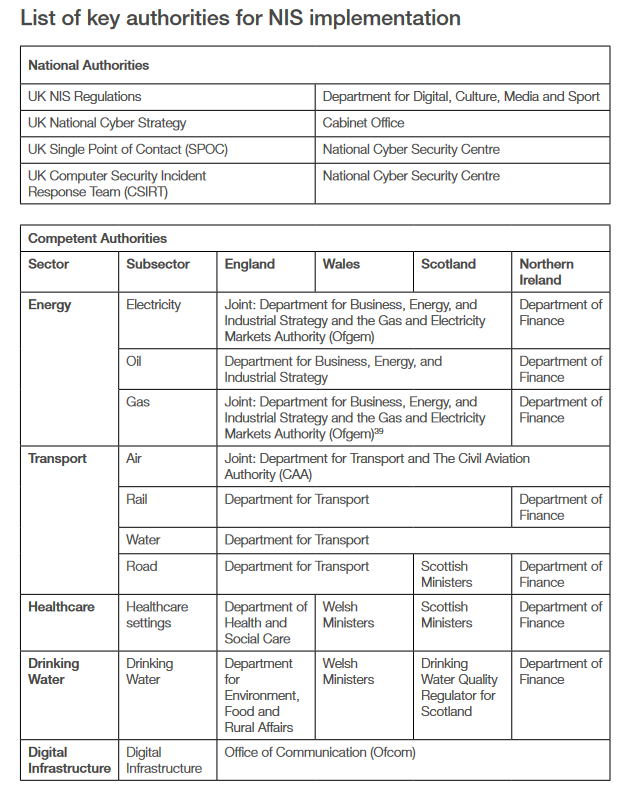
Despite some data centres in the UK being designated Critical National Infrastructure (CNI) their security and resilience is a “largely unregulated” sector in the UK as one law firm, Morgan Lewis put it this summer; data centres are not, for example, under the scope of 2018’s Networks and Information Systems (NIS) regulations.
A consultation run by the DCMS on this subject that ended in August 2022 emphasised that HMG is “developing a stronger risk management framework to address two risks associated with data storage and processing infrastructure.”
“The infrastructure where large volumes of data accumulate an attractive target to those who may have the intention or capability to threaten the UK’s national security, economy or ways of life” it added, saying “ensuring the continuity of service of data storage and processing infrastructure is [also] of national interest.”
Why is the gov’t suddenly concerned about data centre security?
The NCSC meanwhile warned this week that to ensure a more resilient UK, significantly more work is needed.
“Government departments, the wider public sector and regulated operators of CNI, must raise their standards and manage their risk more proactively. Large businesses and organisations, including providers of digital services and platforms need to be more accountable for protecting their systems, services and customers as a core part of running their business” the 2022 annual NCSC report noted as concern grows among government figures about the poor levels of Quality Assurance (QA) in software critical to CNI and other infrastructure.
NCSC annual report: Attacks on exposed RDP falling -- maybe because everyone's pwned
Other key takeaways from the report include a note that the use of Remote Desktop Protocol (RDP) to gain initial access to target systems appears to have tailed off notably: “This may be because potential target organisations are protecting themselves better from attacks of this kind or because a large proportion of the vulnerable configurations have already been exploited. As RDP services decline as an initial access route, other ways in such as phishing and access through third parties is increasing as a proportion of all attacks.”
The NCSC this year meanwhile broadened its Cyber Incident Response (CIR) scheme to support government, CNI
and large corporate organisations in their preparedness for significant targeted cyber attacks: "This included rewriting the Technical Standard and a new application process for the Cyber Incident Response scheme.
It added: "The scheme supports ‘high threat’ organisations of national significance and was relaunched at the end of March as Cyber Incident Response Level 1. Work has continued on a new Level 2 scheme, which is expected to support the growth in the sector while extending the reach of the NCSC in providing incident-response support to medium and large enterprises, local authorities and other government bodies."








