Hackers proxied the Azure Active Directory (Azure AD) sign-in pages of thousands of organisations to steal credentials and bypass multi-factor authentication (MFA), Microsoft has warned, saying it tracked attempts against 10,000 organisations since September 2021 – many attacks resulting in successful follow-up business email compromise (BEC) campaigns (sophisticated phishing that mimics suppliers to steal money or data).
CISOs and other security professionals who have fought for broad MFA rollout sometimes painfully and now wondering wearily what to do, fear not -- organisations can make their MFA implementation “phish-resistant” by using solutions that support Fast ID Online (FIDO) v2.0 and certificate-based authentication, Redmond said.
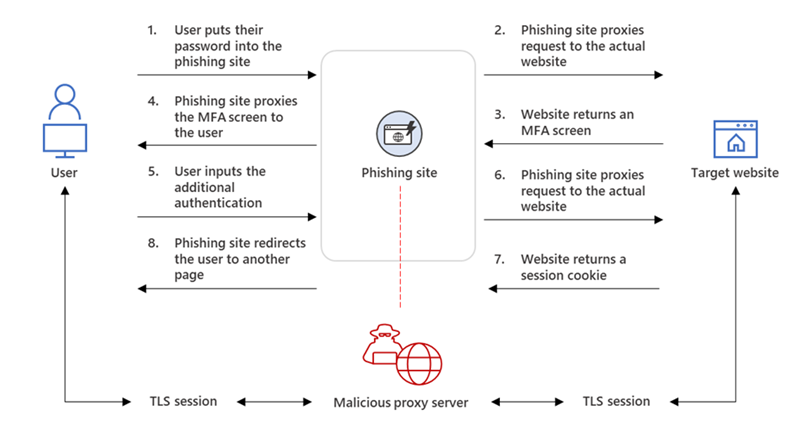
The so-called adversary-in-the-middle (AiTM) approach (known in less enlightened times as MiTM) as detailed in the Microsoft graphic above, lets the attackers intercept the authentication process and extracting data from the HTTP requests such as passwords and, more importantly, session cookies. Once the attacker obtains the session cookie, they can inject it into their browser to skip the authentication process, even if the target’s MFA is enabled.
Microsoft took the opportunity to tout its own security toolings and also urged security and IT professionals to be alert to "sign-in attempts with suspicious characteristics (for example, location, ISP, user agent, use of anonymizer services" [and] "hunt for unusual mailbox activities such as the creation of Inbox rules with suspicious purposes or unusual amounts of mail item access events by untrusted IP addresses or devices."
Sharon Nachshony, Security Researcher at Silverfort, added in an emailed comment: "This campaign is interesting because it outlines the creative approaches attackers will take to steal identities and the resultant domino effect once they have breached a network. Business Email Compromise, the endgame in this attack, has been used historically to siphon hundreds of thousands of dollars from single organizations. If, as Microsoft states, there were 10,000 targets – that is a potentially huge return from compromised credentials.
"While AiTM is not a new approach – obtaining the session cookie after authentication shows how attackers have had to evolve and take steps to try and sidestep MFA, which they hate. In addition to the steps outlined by Microsoft – an organization could also defeat this attack by sending the legitimate user a location with the MFA request. This would defeat the problem posed by proxy servers, which would be in a different location, and ensure a more secure authentication process." Microsoft's detailed writeup and IOCs seen to-date are here.









