Hackers appear to be increasingly adopting the Havoc command and control (C2) framework, security researchers say. The open source framework, developed by C5pider, supports the building of offensive agents in several formats including Windows PE executable, PE DLL and shellcode and is an alternative to the paid for (or cracked) tools like Cobalt Strike that have become so ubiquitous in hacking campaigns.
Zscaler researchers are among those who have noticed its use in the wild recently (to target a government organisation), describing it in a recent blog as “an advanced post-exploitation command and control framework capable of bypassing the most current and updated version of Windows 11 defender due to the implementation of advanced evasion techniques such as indirect syscalls and sleep obfuscation.”
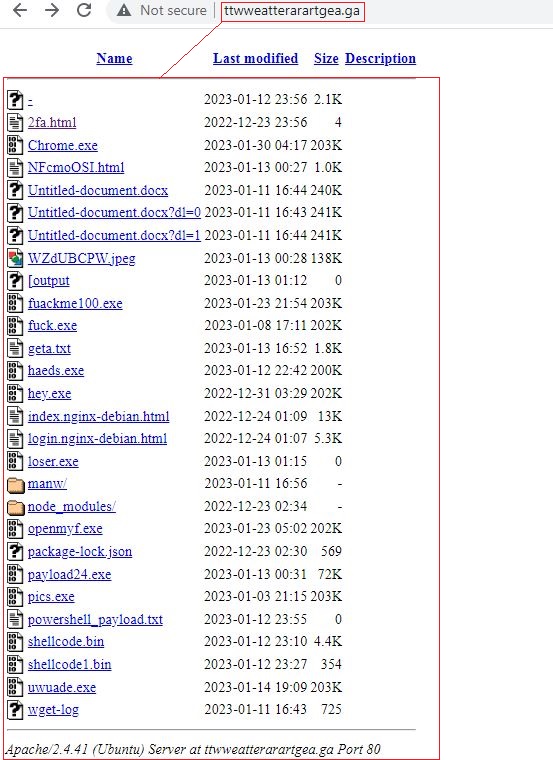
(In that campaign, however, Zscaler said, the bad actors made “several opsec failures”, saying that the server from which the final payload was downloaded had an open-directory it “where multiple demon & metasploit payloads along with internal logs and screenshots were hosted as shown in the screenshot below…”).
The framework has been seen being deployed via a malicious npm package (Aabquerys) typosquatting legitimate module, as revealed in a report from ReversingLabs' research team earlier this month and first reported by Bleeping Computer’s Sergiu Gatlan – this campaign saw an initial malicious download summon “Demon.bin”, a malicious agent with remote access trojan functionalities that was generated using Havoc.
As one security researcher recently noted: “Havoc C2 has quickly become one of my favorite open source C2s. It’s features offer everything that you need to complete a pentest or red team engagement and there are new modules coming out every week… With Havoc’s popularity going through the roof, it’s only natural that the payloads would get signatured by AV vendors including Windows Defender. Luckily, there are ways that we can get around the signature and still get system privileges on a fully patched Windows 11 machine.”
Hackers are always going to use the best tool for the job and Cobalt Strike’s ubiquity has meant defenders are getting better at spotting it. Over the years other tools of the C2 trade have included the C3 framework – a platform that was first released publicly by F-Secure Labs in September 2019 and which was adopted by one threat group dubbed “UNC2628” to hide their traffic home; they used it to proxy their C2 communications through the Slack API, FireEye said in a 2021 blog; others have used networked printers as a C2 channel.
Cyberreason in January 2023 said it had also seen wider adoption of the open source C2 framework Sliver. created by security company Bishop Fox and released in 2020, which has been spotted being deployed in the wild by the NCSC and Proofpoint, among others; other C2 frameworkers also increasingly proliferate.
As well as broader cyber resilience best practices to ensure compromises can be mitigated, defenders can also look at a range of tools from trusted partners that sniff network traffic to detect suspicious activities that may be indicative of attacker activity, using a mixture of machine learning and rule-based matching techniques to try and detecs zero-day C2 servers and new variants of malware families based on patterns found in the session size, direction, and interarrival times (the time between the "start" of two events.)








