This week saw the first “Patch Tuesday” of the year, with all eyes predictably turning to Microsoft (one of several companies issuing patches on the second Tuesday of each month). Redmond posted fixes for 126 CVEs, nine rated critical, including one in Exchange Server that was reported by the National Security Agency (NSA).
Among the worst is CVE-2022-21907, an RCE bug that is wormable if exploited. It affects multiple products including Windows 10 and 11; Windows Server configured as webservers with a CVSS rating of 9.8/10. In Windows Server 2019 and Windows 10 version 1809, the HTTP Trailer Support feature that contains the vulnerability is not active by default, Microsoft noted. If you are affected, prompt patching would be judicious, if possible…)
As Greg Wiseman, Product Manager at Rapid7 noted, the patches include “two Remote Code Execution (RCE) vulnerabilities affecting open source libraries that are bundled with more recent versions of Windows: CVE-2021-22947, which affects the curl library, and CVE-2021-36976 which affects libarchive…”
Get yourself following The Stack on LinkedIn and say hello to the team
Adobe meanwhile pushed out patches for 41 CVEs. As the Zero Day Initiative, a bug bounty programme, noted: “The update for Acrobat and Reader fixes a total of 26 bugs, the worst of which could lead to remote code execution (RCE) if a user opened a specially crafted PDF. Several of these bugs were demonstrated at the Tianfu Cup, so it would not be unexpected to see these used in the wild somewhere down the line.”
Bharat Jogi, Director, Vulnerability and Threat Research, Qualys, noted that the "monster" Patch Tuesday came at a time of "chaos in the security industry whereby professionals are working overtime to remediate Log4Shell – reportedly the worst vulnerability seen in decades. Unpredictable events such as Log4Shell add significant stress to the security professionals dealing with such outbreaks – and bring to the forefront the importance of having an automated inventory of everything that is used by an organization in their environment."
The ZDI and Qualys are among several useful providers of insight on Patch Tuesday. We won't reiterate what you can easily find elsewhere, including in the links immediately above. Happy patching folks.
Security vulnerabilities in 2021: 50 CVEs a day landing....
Despite the predictable monthly focus on Microsoft, it was actually Google that suffered/patched the most software security vulnerabilities (CVEs) in 2021 of all companies, with the Chrome browser most frequently the culprit -- also suffering double-digit 0-days that got exploited in the wild. (The high numbers can also reflect mature disclosure programmes, attractive bug bounties, and other signs that aren't all bad news...)
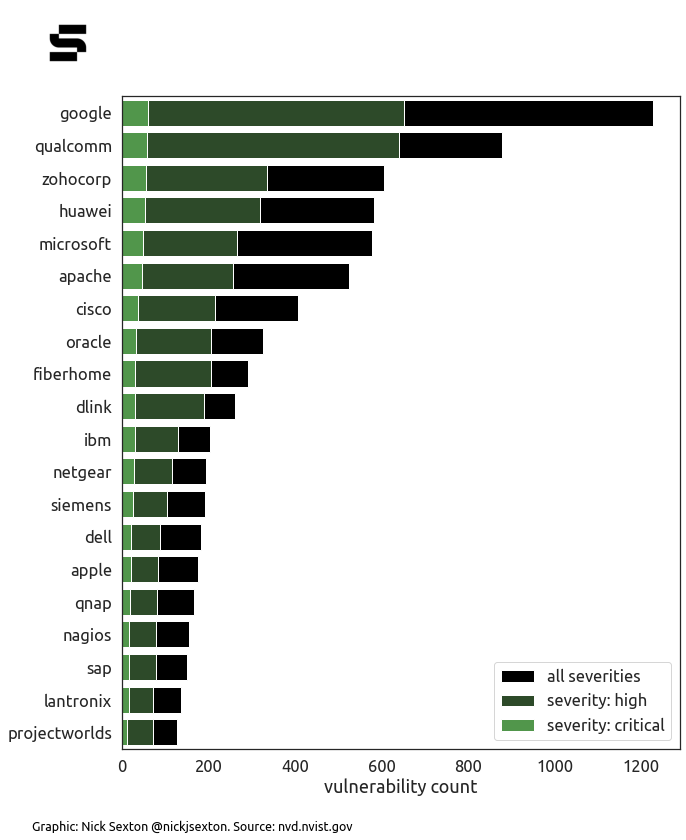
That’s according to a review this week by The Stack of data for all of 2021’s record number of CVEs (short for Common Vulnerabilities and Exposures; CVEs are allocated to many, if not all, publicly disclosed security flaws).
We pulled the data from NIST’s NVD: a government repository of vulnerability management data.
This revealed that 19,796 CVEs were allocated in 2021. Of these, some 2,715 were rated “critical”, we found.
The figure is equivalent to over 54 vulnerabilities every day; including 7 critical security bugs every day.
Per the chart at left, Qualcomm, Zohocorp and Huawei featured in the "top five" vendors, alongside Google and Microsoft. Arguably also noticeable is the number of CVEs allocated to Siemens products as the German multinational pushes more industrial and security software.
See also: An 800-pound gorilla eyes the Operational Technology security space -- Can Siemens compete?
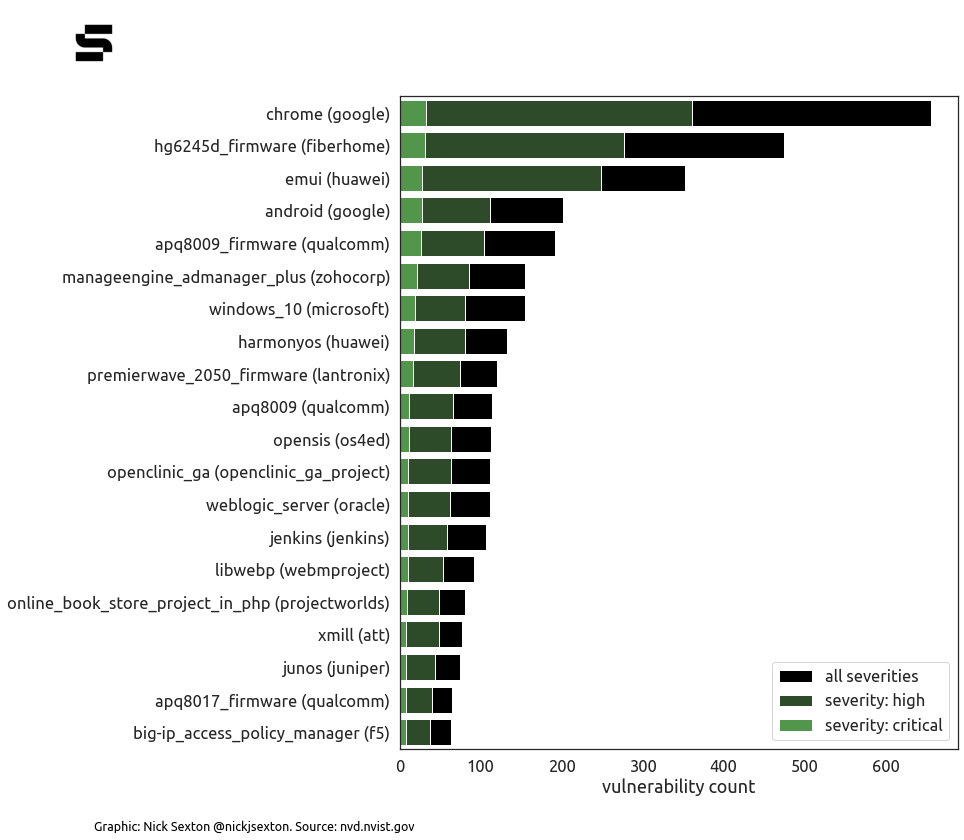
Security vulnerabilities in the dominant Chrome browser (which has over 60% of global market share) accounted for the most CVEs in the NVD by individual software product.
Google's patches tend to get less widely reported than those in Microsoft products, for various reasons, including Google's often thin updates on the bugs. The company's Project Zero does maintain a "0-day in the wild" tracker however, in which Chrome accounts for nearly 25% of the 57 publicly exploited 0-days it tracked in 2021.
The data on the huge number of vulnerabilities comes after what has been an intensely testing year for IT professionals on the security front.
The year included several critical and easy-to-exploit bugs in widely used cybersecurity software – the very tools there to protect you -- as well as widely and rapidly exploited vulnerabilities in Exchange Server.
Attacks on MSPs were also rampant; the downstream impact of hitting an organisation delivering IT services for a wide range of organisations is clear and well demonstrated.
July’s attack on Kaseya is a powerful case in point. That saw an affiliate of the REvil ransomware syndicate use vulnerabilities in software from Florida-based Kaseya to hack some 50+ MSPs that used its products; piggybacking on that access in turn to hit over 1,500 organisations with ransomware.
Prompt patching, of course, is not always easy: complex webs of dependencies, the risk of outages, the need for sustained uptime and more all sometimes mitigate against patching.
And sometimes even when you do do the right thing, well...









