
Google has released an urgent update to eliminate a new Chrome 0day vulnerability, which has an in-the-wild exploit. Other Chromium based browsers, including MS Edge and Opera, are also affected.
The high-severity vulnerability, allocated CVE-2022-1096, is within Chrome’s JavaScript engine V8, relating to a “type confusion” flaw. Google did not provide any details of the vulnerability or exploit.
“Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed,” said PrudhviKumar Bommana of the Chrome team in a blogpost.
“Google is aware that an exploit for CVE-2022-1096 exists in the wild,” added Bommana in the post.
According to Bugcrowd CTO Casey Ellis, the new chrome 0day vulnerability was reported on 23 March, before being fixed on 25 March. The update to Chrome also only addressed this single issue, which Ellis noted as being unusual. On Twitter and other social networks there were reports the vulnerability could lead to a full system take-over, and some crypto enthusiasts reported attacks on browser-based wallets, which they linked to the vulnerability.
Google's Project Zero maintains a “0day in the wild” tracker. Chrome accounted for nearly 25% of the 57 publicly exploited 0days it tracked in 2021 -- and was the software that saw most CVEs allocated to it in 2021. As it auto-updates however and not rich with the kind of dependencies Microsoft or other enterprise software products often have, both exploited vulnerabilities and patches tend to draw somewhat less attention.
See also: Google sees most CVEs in 2021
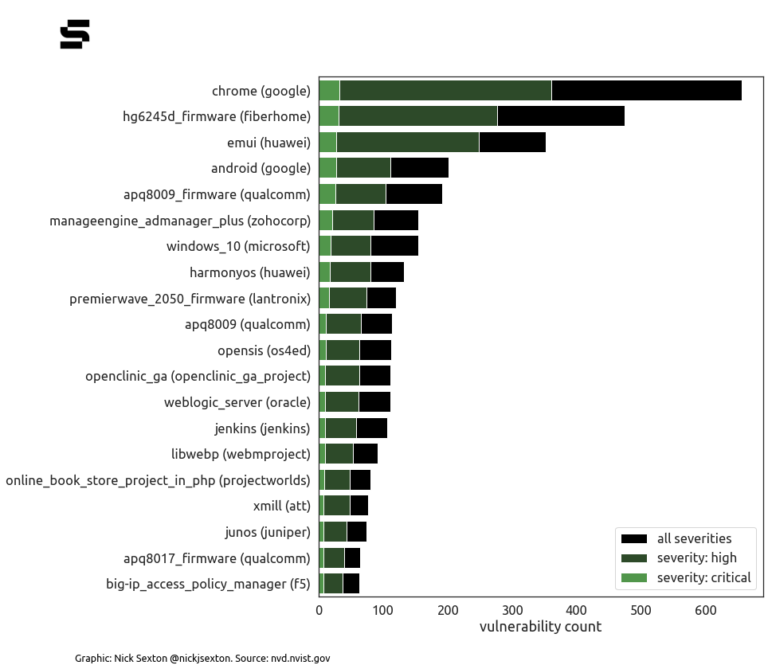
This is the second new Chrome 0day of 2022, following CVE-2022-0609 in February, which was also being exploited at the time of patching. In that case, after the initial announcement, Google linked exploitation of the bug to North Korean hacking groups.
“We observed the campaigns targeting U.S. based organizations spanning news media, IT, cryptocurrency and fintech industries. However, other organizations and countries may have been targeted. One of the campaigns has direct infrastructure overlap with a campaign targeting security researchers which we reported on last year,” said a Google blog post from the time.
“The exploit was patched on February 14, 2022. The earliest evidence we have of this exploit kit being actively deployed is January 4, 2022,” the post added.