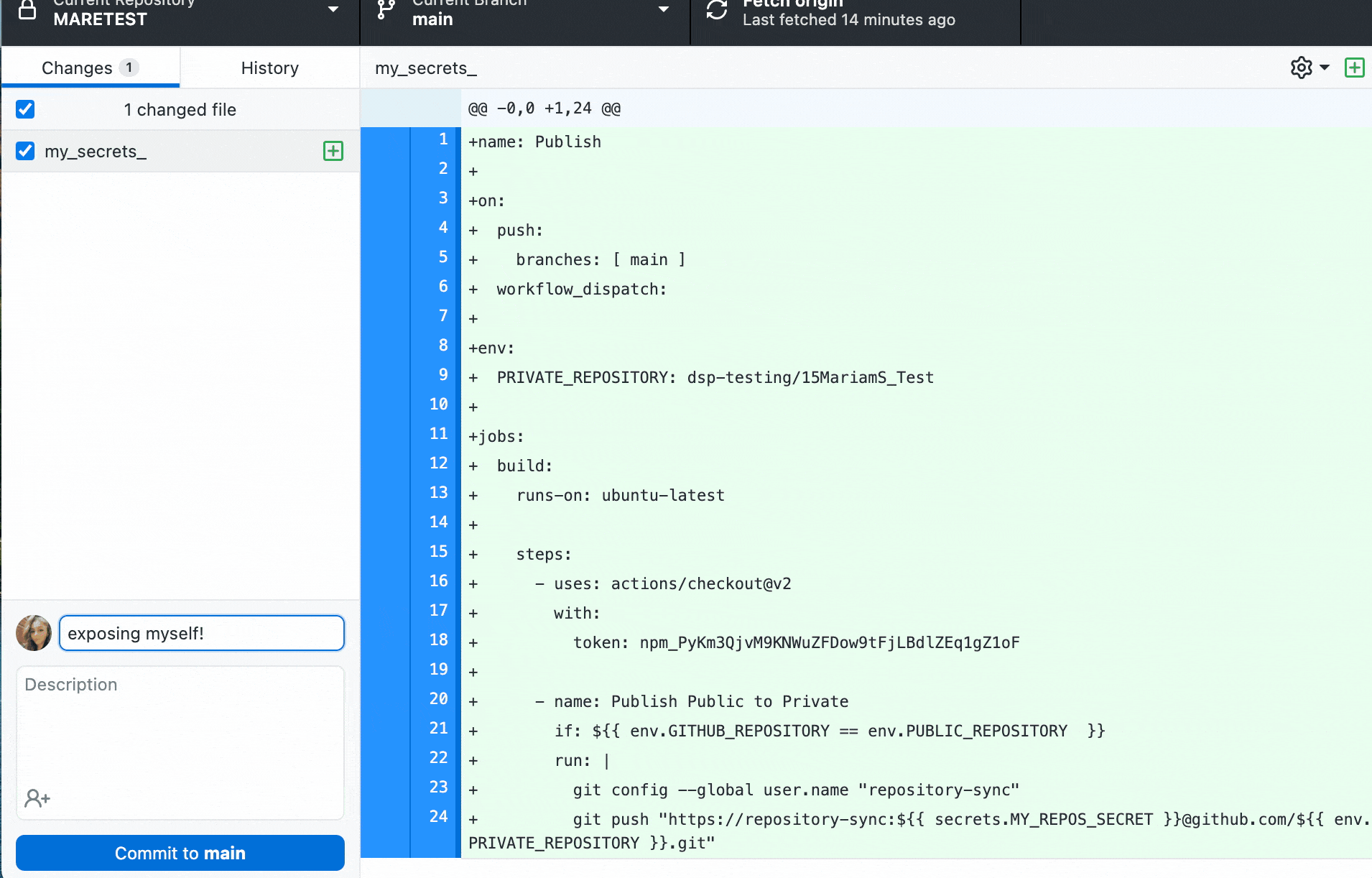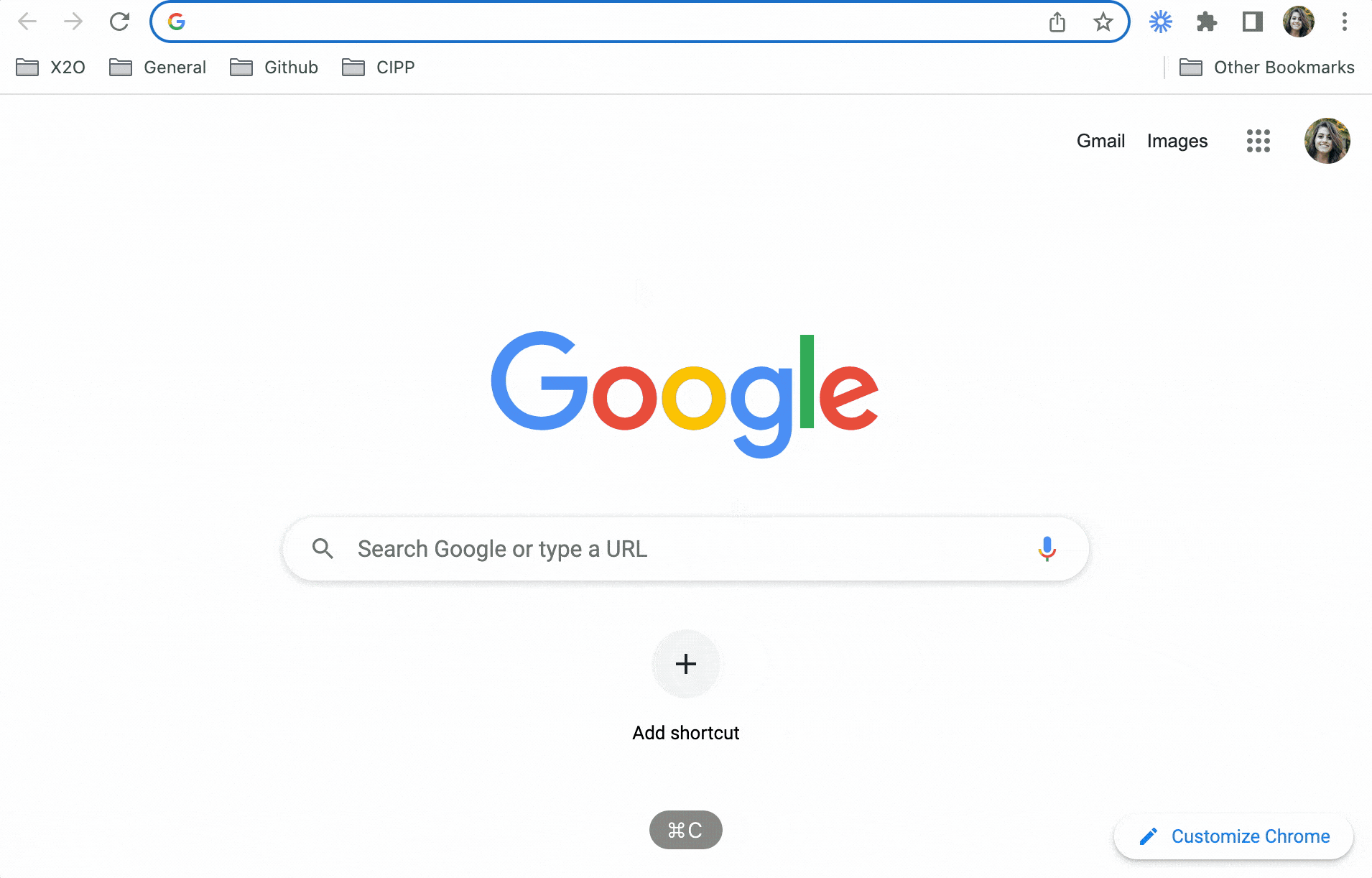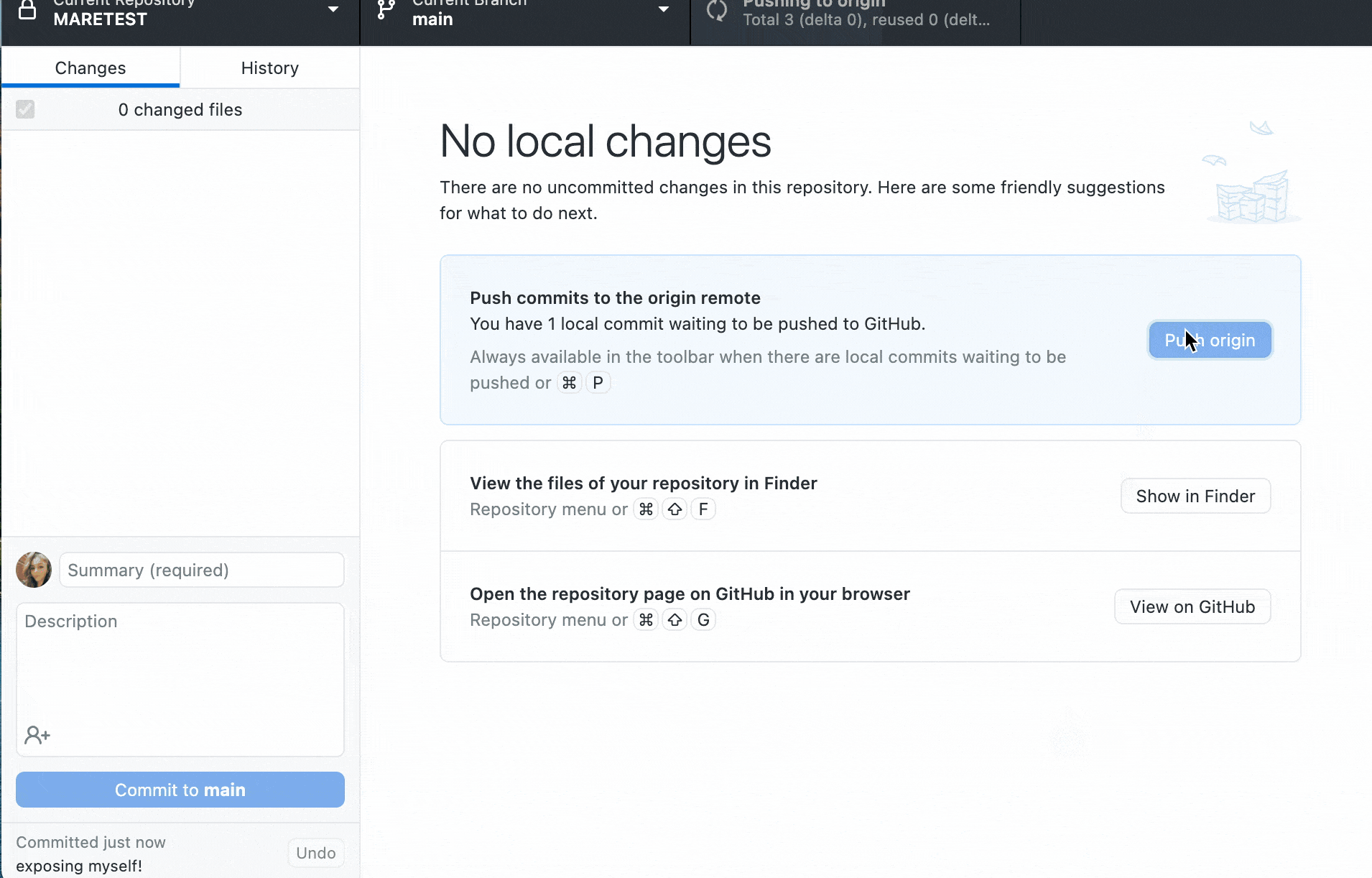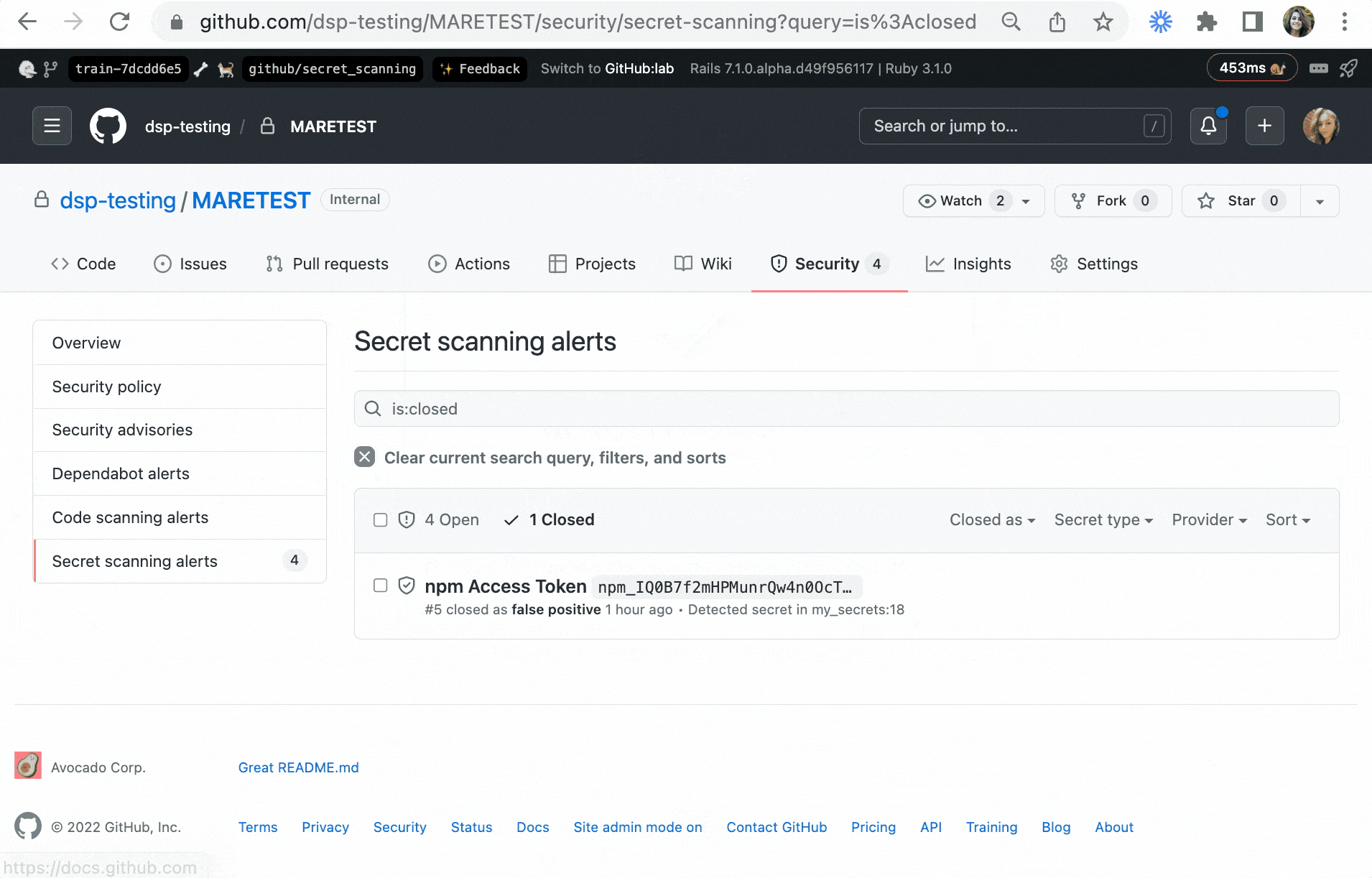
Developers have a bad habit of leaving private passwords, API tokens, and credentials in GitHub repositories that can be spotted and abused by those with the intention of abusing the access they give.
(This CyberArk blog showcases just how common and easy that is to exploit...)
This week GitHub -- which now has some 73+ million users -- said it was adding a welcome option for GitHub Advanced Security customers that scans for secrets before a git push is accepted. (i.e. it checks for private credentials et al before content is uploaded to a given repository in a bid to pre-empt such leaks).
(Existing GitHub tools let users scan for secrets after a push. Hackers enjoy that too...)
GitHub said: "To make this possible without disrupting development productivity, push protection only supports token types that can be detected accurately. Last year, we changed the format of our own secrets and started collaborating with other token issuers to drive highly identifiable patterns. Today, we’re launching with support for 69 high confidence patterns that each have a signal-to-noise ratio that developers can trust."
"If a secret is identified, developers can review and remove the secrets from their code before pushing again. In rare cases where immediate remediation doesn’t make sense, developers can move forward by resolving the secret as a false positive, test case, or real instance to fix later" GitHub added on April 4, 2022.
Follow The Stack on LinkedIn and connect with the team
To use GitHub Advanced Security license in a private or internal repository you must be using paid-for GitHub Enterprise. Its suite of security tools are free however for public repositories
Owner Microsoft noting on its last earnings call (January 26, 2022) that "as companies prioritize embedding security into their developers' workflow, we're investing across GitHub to secure open source. Increasingly, every DevSecOps workflow will start with GitHub Advanced Security, and we're seeing strong demand from both digital natives like Afterpay and Mercari, as well as established companies like 3M and Bosch."
Those seeking to secure their GitHub environments may also like to consider policy-bot.
That's a GitHub application open sourced by data mining company Palantir under an Apache 2.0 licence and designed to enable complex change approval workflows; focussed more on the "pull" than "push" side.
As Palantir CISO Dane Stuckey notes on Twitter: “If you’re staring at your CI/CD pipeline and wondering how to better secure it, I highly recommend policy-bot“. While GitHub natively supports required reviews, policy-bot provides more complex approval features and a UI to view the approval status of any pull request.
It lets users:
- Require reviews from specific users, organizations, or teams
- Apply rules based on the files, authors, or branches involved in a pull request
- Combine multiple approval rules with
andandorconditions - Automatically approve pull requests that meet specific conditions
Users can best understand the importance of this tool by contextualising it against a rising trend towards Infrastructure as Code (IaC); a way of managing IT infrastructure using machine-readable configuration files which are often versioned and store in GitHub to enable full traceability of configuration changes.








