The US's Cyber and Infrastructure Security Agency (CISA) has added six vulnerabilities to its "Known Exploited" catalogue, which tracks software bugs seen exploited in the wild that CISA describes as "a frequent attack vector for malicious cyber actors and [which] pose significant risk to the federal enterprise."
The latest batch are not hot-off-the-press bugs however. They include four GIGABYTE vulnerabilities allocated CVEs in 2018 and given a belated security advisory in May 2020 by the company. The bugs largely stem from the fact that GIGABYTE’s drivers allow user-mode applications read/write access to memory.
(Read SecureAuth's comical disclosure timeline here to get a sense of how well the Taiwanese company handled the vulnerability disclosure. In brief: It received a vulnerability disclosure in April 2018. It responded in May 2018 that "Gigabyte is a hardware company and... not specialized in software"; it said in July 2018 that its "products are not affected by the reported vulnerabilities"; it quietly fixed its drivers in May 2020...)
See also: 7 free security tools to explore merrily
https://twitter.com/SpecialHoang/status/1144796969388400641
Among the GIGABYTE vulnerabilities exploited is a CVSS 9.8 bug (CVE-2018-19323) affecting multiple GIGABYTE products first reported by SecureAuth's Diego Juarez.
This affects the "GPCIDrv and GDrv low-level drivers in GIGABYTE APP Center v1.05.21 and earlier as well as graphics and gaming engines (Here's a POC.)
(As one security researcher, "SpecialHoang" noted at the time, the bugs can be exploited "for privilege escalation and potentially EDR bypass... [but] Gigabyte and the listed drivers are not the only one that is doing it wrong. Plenty of other drivers from all different sources are failing to secure their driver correctly...")
Two other known exploited vulnerabilities included ones that affect Cisco AnyConnect Secure Mobility Client for Windows releases earlier than 4.8.02042.
They include CVE-2020-3153, which lets an authenticated local attacker "copy user-supplied files to system level directories with system level privileges. The vulnerability is due to the incorrect handling of directory paths. An attacker could exploit this vulnerability by creating a malicious file and copying the file to a system directory. An exploit could allow the attacker to copy malicious files to arbitrary locations with system level privileges" as Cisco's advisory put it at the time.
Patches for all vulnerabilities listed by CISA in this latest tranche are available.
Follow The Stack on LinkedIn
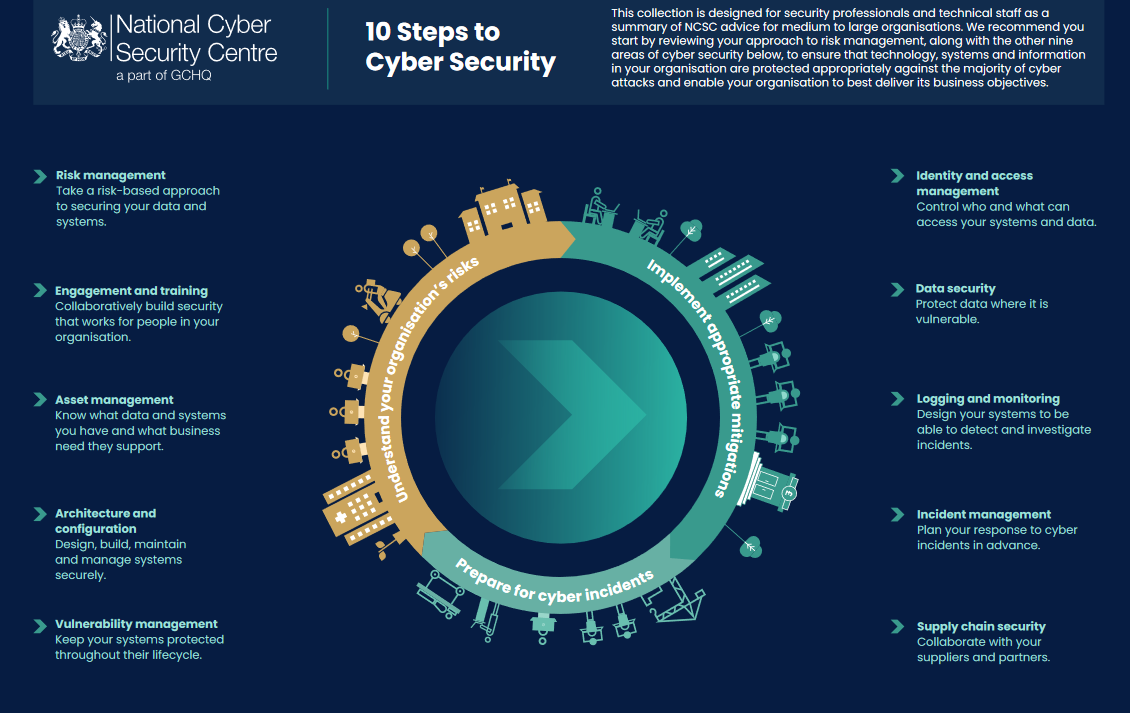
As ever, patch as promptly as you can, be kind to your security team because everything is badly broken and held together with duct tape and it's not their fault. Do revisit the NCSCs handy "10 steps to cyber security" guide here if stuck for inspiration, which spans risk management; engagement and training; asset management; architecture and configuration; vulnerability management; identity and access management; data security; logging and monitoring; incident management; supply chain security and try not to give domain admin credentials to hundreds of people and run your servers on an unpatched and unsupported OS like this.