Researchers from HP Wolf Security have identified malware in the wild that appears to have been created by Generative AI (GenAI).
Although it is almost certain that bad actors have been using GenAI for nefarious purposes, actual proof of this inevitable trend has been "limited", the investigators said.
In Q2, HP Wolf Security observed a campaign spreading AsyncRAT, a Remote Access Tool (RAT), using VBScript (T1059.005) and JavaScript (T1059.007), which was "was highly likely to have been written with the help of GenAI".
"The scripts’ structure, comments and choice of function names and variables were strong clues that the threat actor used GenAI to create the malware," researchers wrote. "The activity shows how GenAI is accelerating attacks and lowering the bar for cybercriminals to infect endpoints.
"Threat actors have been using generative artificial intelligence (GenAI) to create convincing phishing lures for some time, but there has been limited evidence of attackers using this technology to write malicious code in the wild."
In early June, HP isolated an "unusual" French HTML email attachment that was "posing as an invoice" and asked for a password when opened.
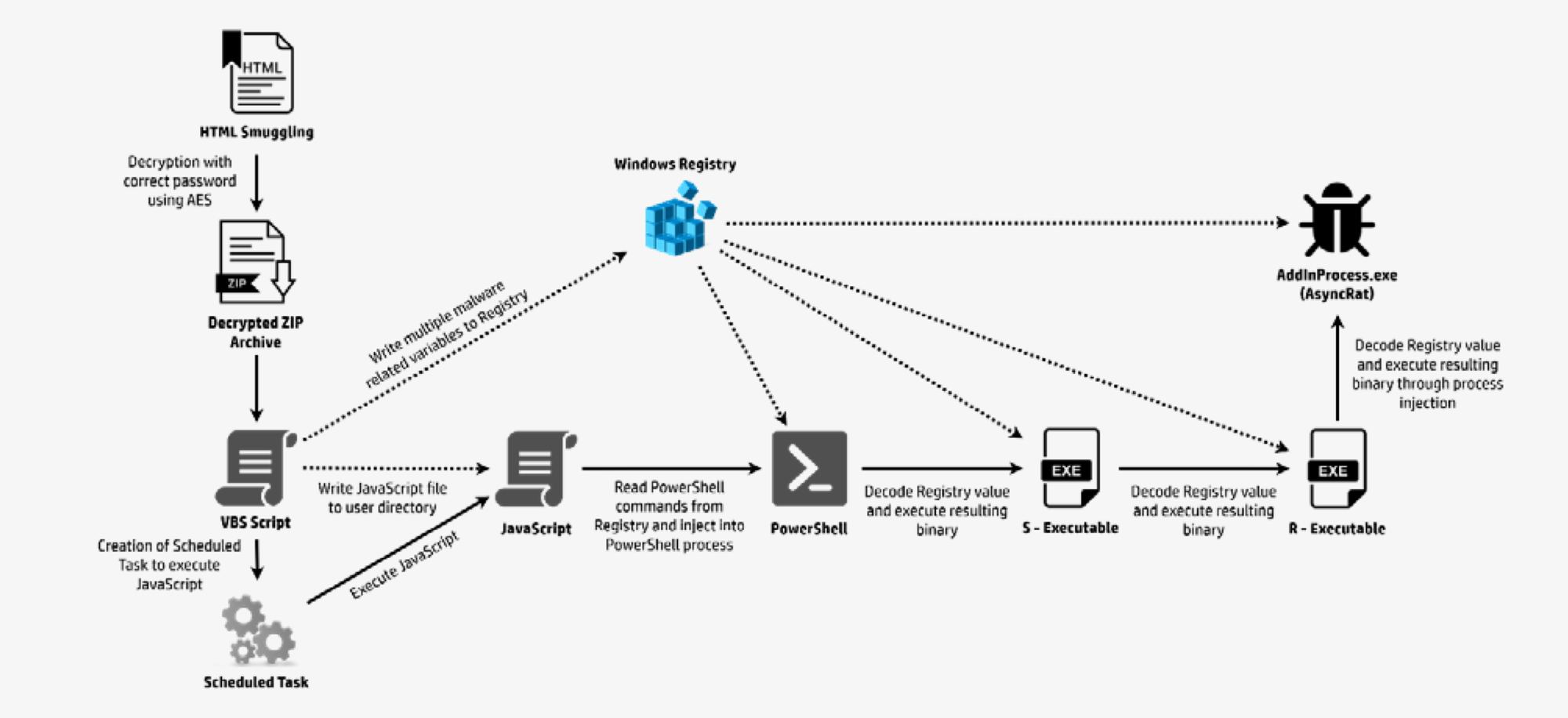
Initial analysis of the code found it was an HTML smuggling threat.
"But in contrast to most other threats of this kind, the payload stored inside the HTML file was not encrypted inside an archive," HP Wolf Research wrote. "Rather, the file was encrypted within the JavaScript code itself. The attackers encrypted the file using AES and implemented it without making any mistakes, meaning decrypting the file is only possible with the correct password."
After brute forcing the password "in a reasonable amount of time", the investigators obtained the password and gained access to a decrypted archive containing a VBScript file which launched an infection chain when launched and deployed AsyncRAT.
The VBScript writes key variables to the Windows Registry, which are used later in the attack. Subsequently, a JavaScript file is dropped into the user directory and executed through a scheduled task. This script retrieves a PowerShell script from the Registry and injects it into a new PowerShell process. The PowerShell script then uses additional Registry variables to run two executables, which initiate the malware payload by injecting it into a legitimate process.
"Interestingly, when we analyzed the VBScript and the JavaScript, we were surprised to find that the code was not obfuscated," the researchers wrote. "In fact, the attacker had left comments throughout the code, describing what each line does – even for simple functions. Genuine code comments in malware are rare because attackers want to their make malware as difficult to understand as possible.
"Based on the scripts’ structure, consistent comments for each function and the choice of function names and variables, we think it’s highly likely that the attacker used GenAI to develop these scripts."
The claims have sparked furious discussion on social media, with some people questioning how effective the malware would be - or to what extent it was created by GenAI.
On Reddit, one critic wrote: "It is speculative at best that GenAI was actually used and even if it was used, it's still trash at writing even the most basic, boilerplate software tasks. Being able to churn out small components of script kiddy level malware with open source payloads that'll get instantly blocked by every AV under the sun is not novel or even really useful honestly."







