
Gartner’s launched its first Magic Quadrant for OT security. It’s calling it “Cyber-Physical Systems” (CPS) though – and it throws up a few surprises.
"Security for these connected assets used to be 'out of sight, out of mind,' or covered under a generic OT security umbrella dominated by network-centric tools. An asset-centric security discipline has emerged," Gartner noted.
The research house claimed that the OT attack surface and threats to it are both growing; manual asset inventories in the industrial space are “time inefficient and costly”; and IT security tools are inappropriate for CPS.
It defines CPS as follows:
“Products that use knowledge of industrial protocols, operational/production network packets or traffic metadata, and physical process asset behavior to discover, categorize, map and protect CPS in production or mission-critical environments outside of enterprise IT environments.” – Gartner, CPS PP.
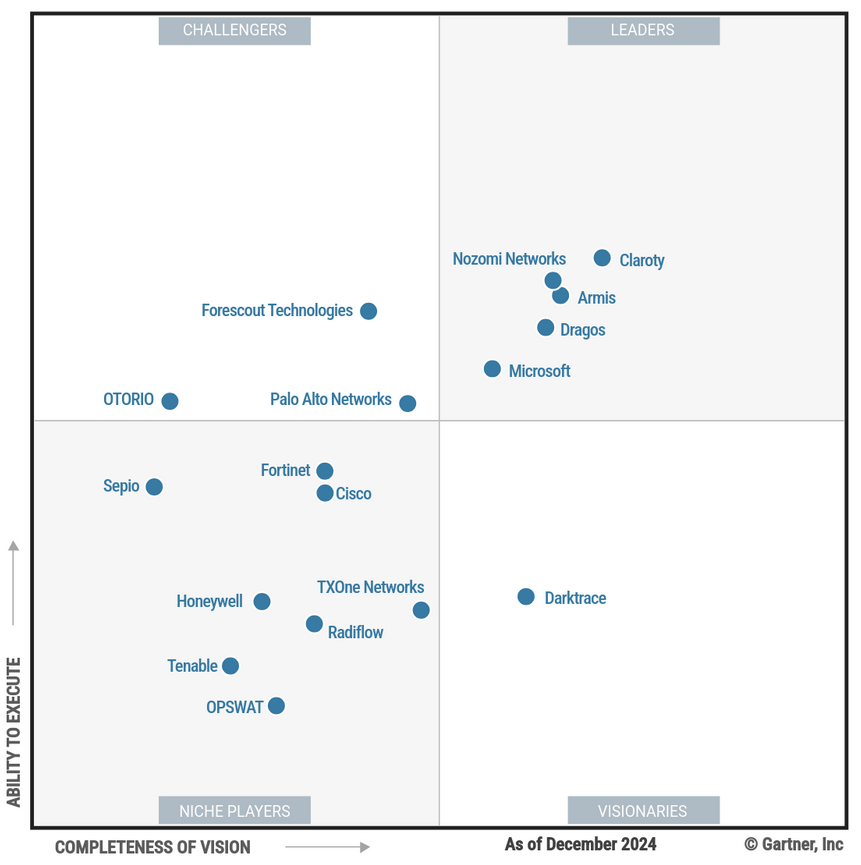
The report’s somewhat overlooked December 2024 release comes as utilities and other organisations move to bolster their security posture – in the UK nudged by government stakeholders concerned at the need to dramatically improve the cybersecurity of critical national infrastructure.
Assessment by the NCSC of previous industry breaches, for example, has resulted in the quiet creation of new requirements under an “enhanced” Cyber Assessment Framework (e-CAF). Conformity with a long list of requirements is not required until March 2028 but many are moving fast.
Wales & West Utilities – one of the UK’s five main gas distributors – for example in 2023 signed a three-year OT asset discovery contract with one of the Magic Quadrant leaders, Claroty, which was negotiated without a prior call for competition, owing to what it said was “extreme urgency brought about by events unforeseeable for the contracting entity.”
The threat landscape in this sector often goes overlooked.
OT security specialist Forescout for example, has claimed that only 35% of exploited vulnerabilities in the OT sector appeared in CISA’s “Known Exploited” catalogue (“KEV”) – suggesting a huge blindspot.
See also: Potemkin security standards propping up "insecure by design" OT
Armis, Claroty, Dragos, Microsoft, and Nozomi Networks were the five vendors that made the "Leaders" quadrant. Darktrace made the “Visionaries” quadrant. Forescout Technologies, OTORIO, and Palo Alto Networks slipped into the “Challengers” category of the report.
All, Gartner noted, have their flaws – with many relying on IT resellers with a lack of OT expertise, lacking deep industry vertical expertise (or conversely having it but keeping it distinctly narrow in scope), confusing licencing options or simply, desperately low brand visibility.
CPS PPs [protection platform], noted Gartner, are increasingly offered as a way to bring together network-centric and asset-centric security approaches: “This allows for multiple security capabilities to be added, such as vulnerability management, threat intelligence, visualizations, alerts, playbooks or feeds into other IT security (and inventory) tools.”
This particular market is still “nascent” it said yet “poised for rapid growth as cyberthreat actors (nation-states and profit-motivated alike)... target… critical infrastructure environments where CPS are prevalent.”
As one leader, Dragos notes: “OT security strategies often start with hardening the environment – removing extraneous OT network access points, maintaining strong policy control at IT/OT interface points, and mitigating high risk vulnerabilities. This approach reduces lateral movement within the network, confining potential intrusion… Use asset inventory and network mapping tools to identify all connected devices,
