Scores of companies across the FTSE 350 are still demonstrating "nakedly dangerous" protocol exposures, with Windows Remote Desktop (RDP), file-sharing (SMB), and Telnet exposed to the public internet.
That's according to a troubling new investigation run by security company Rapid7, which found that the financial sector "accounts for an outsized share of the kinds of especially worrisome exposures."
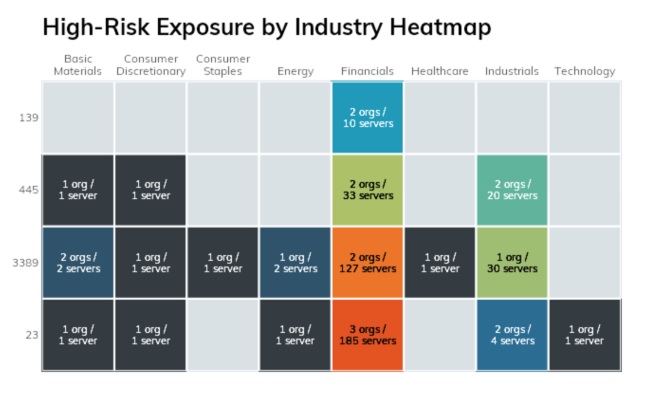
The company found 164 RDP services exposed across nine companies, and 65 servers exposing SMB across eight companies. (Some running a version of the open source SMB server Samba released in late 2009.) It also found 193 Telnet hosts exposed across nine companies: 185 of them in the financial services sector. These exposed routers, switches, industrial control systems gateways, cameras, firewalls, and servers.
SMB exposure risks include "data leakage from file shares, credential compromise via brute force attacks, and malware infection, Rapid7 research director Tod Beardsley noted in the report.
Aging plaintext-based protocol Telnet meanwhile "nearly always transmits credentials and data in cleartext and has no protections against man-in-the-middle injection of commands or data."
Follow The Stack on LinkedIn
He added: "Any non-zero number of these services made available to the general internet is... unacceptable in organisations with mature security programmes. Despite all the vulnerability and exploit churn we saw in 2019 and 2020, we appear to be overdue for another self-replicating issue across open ports to insecure services. Closing off your exposure to these services will certainly save you weeks of cleanup later."
nb: For more detailed analysis, read Beardsley's write-up here >.Download
Is it *that* bad? Follow the discussion on Reddit/sysadmin
Want to report such issues? Not so fast...
Good samaritans in the security research community who have found such issues may still struggle (yes, even in 2021) to report them. The majority of the FTSE 350 still don't have a vulnerability disclosure programme -- a formal policy that describes a process for the public/white hat hackers to find and report vulnerabilities .
(Any overwhelmed IT leaders/CISOs looking for a cheat sheet to start thinking about how to build a vulnerability disclosure programme would do worse than to crib some guidance from the US's recently mandatory one, rolled out in September 2020. A starting point may include specifying how security vulnerability reports are tracked to resolution; how remediation activities are coordinated internally; how disclosed vulnerabilities are evaluated for potential impact and prioritised for action; how reports for systems and services that are 'out of scope' are handled; guidelines for communication with the reporter and other stakeholders; any impact of the reported vulnerabilities; resolution of vulnerabilities, including notification of the outcome to the reporter, etc.)
Fixing the protocol exposure issue won't require some expensive software. It will require some back-to-basics inventory-making. This might include making and *maintaining* a list of internet-facing hosts including software versions, roles, and services that are expected to be exposed, then validating it by outside-in scans of all public-facing IP ranges. As Tod Beardsley notes, CISOs or IT teams should also be looking to enforce the use of secure protocols and configuration settings: "Every device currently using Telnet should be able to support SSH—and if it doesn't, it is too old or insecure to be directly connected to the internet."
Want to vent off-the-record on what makes fixing issues like this difficult for you? Drop us a line here or if a more discreet approach is preferred, find us on encrypted messenger Element.








