Security researchers at Dragos have discovered a novel malware that lets threat actors interact directly with operational technology systems.
Dubbed "FrostyGoop" it has been linked to a cyberattack in Ukraine that sabotaged a heating facility, and left people living in six hundred apartments shivering through the brutal cold of January.
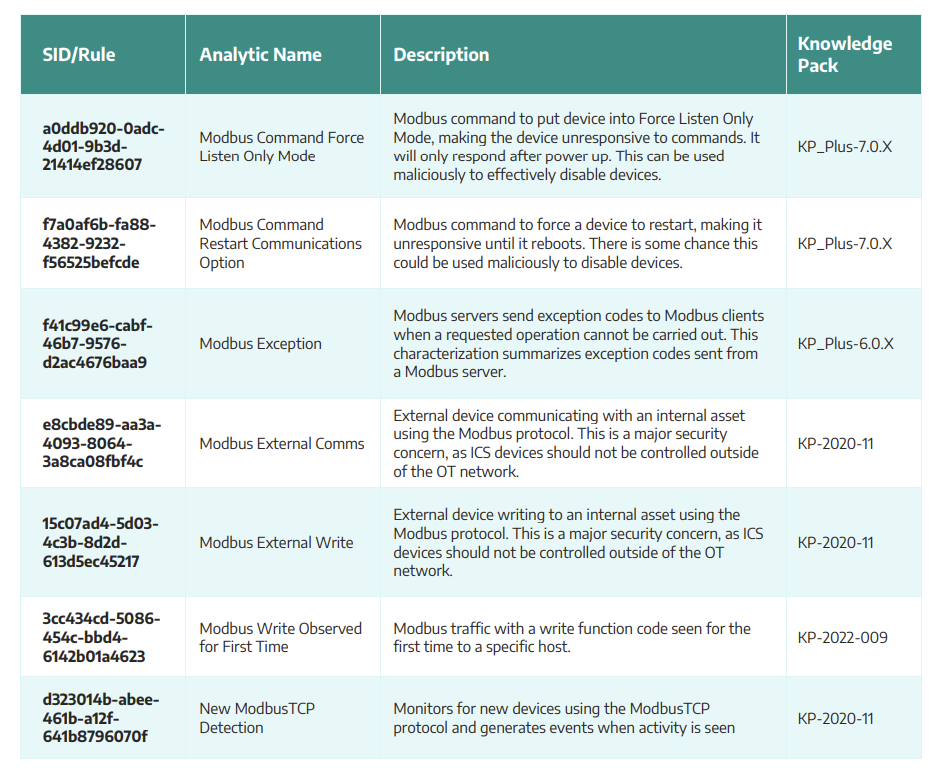
The first-of-its-kind threat is industrial control system (ICS)- specific malware, which allows threat actors to engage with operational technology via Modbus, a widely used communication protocol in ICS environments.
Modbus is a commonly available protect that connects industrial electronic devices. It is typically used to transmit signals from instrumentation and control devices back to a main controller or data-gathering system.
During the cyber attack in Lviv, Ukraine, the malware was used to send Modbus commands to ENCO controllers, causing inaccurate measurements and system malfunctions at a municipal district energy facility.
"The discovery of the FrostyGoop ICS malware and its capabilities has raised significant concerns about the broader impact on OT cybersecurity," Dragos wrote.
"The specific targeting of ICS using Modbus TCP over port 502 and the potential to interact directly with various ICS devices pose a serious threat to critical infrastructure across multiple sectors."
The malware has been compiled for Windows systems, and at the time of the discovery, antivirus vendors did not detect it as malicious, according to Dragos.
Explaining how the malware functions, security researchers noted that it can read and write to an ICS device holding registers containing inputs, outputs, and configuration data.
"FrostyGoop accepts a JSON-formatted configuration file containing information used to execute Modbus commands on a target device. The malware reads the file, parses the JSON data, connects to the IP address from the file, and sends Modbus TCP commands to holding register addresses specified in the configuration file," the report explained.
What makes FrostyGoop particularly dangerous is both the widespread use of Modbus in critical infrastructure networks – and the sheer number of exposed instances Dragos researchers were able to find.
“We’ve already identified at least 40 ENCO controllers across Europe which are directly vulnerable to FrostyGoop via the open internet. Malicious actors could access these devices, communicating over ModbusTCP to manipulate control, modify parameters, and send unauthorised command messages," said Magpie Graham, Principal Adversary Hunter and Technical Director, Dragos.
"Beyond this specific brand of controller, upwards of 46,000 exposed ModbusTCP devices could be subject to similar attacks," Graham added.
While initial access was likely made by exploiting an undetermined vulnerability in an externally facing Mikrotik router, threat actors deployed FrostyGoop to downgrade firmware on the ENCO controllers, disrupting their functioning.
According to Dragos and Ukraine's Cyber Security Situation Center- remediation of the facility took two days.
"The potential risk to unprotected critical infrastructure across Europe and around the world is clear," Graham said in context of this attack.
As a first step organisations must secure themselves by utilising network segmentation, along with strict privilege and user access control practices to prevent these kinds of attacks," he cautioned.








