
Both Elastic and Microsoft analysed previously unreported malware this week. Both (unrelated) campaigns use distinctive and unusual techniques to exfiltrate data or infiltrate commands onto compromised IT systems.
(When malware infects a host, it often initiates a C2 channel with its controlling server that can be used to issue instructions to compromised devices, download additional malicious payloads, or exfiltrate data.)
Whilst attackers have long showcased creativity in C2 (from executing PHP code via HTTP POST requests; exploiting Slack’s API; tapping networked printers, or using Telegram) both this week’s reports showcase notable techniques: A distinctive use of Tor, and abuse of Microsoft’s Graph API.
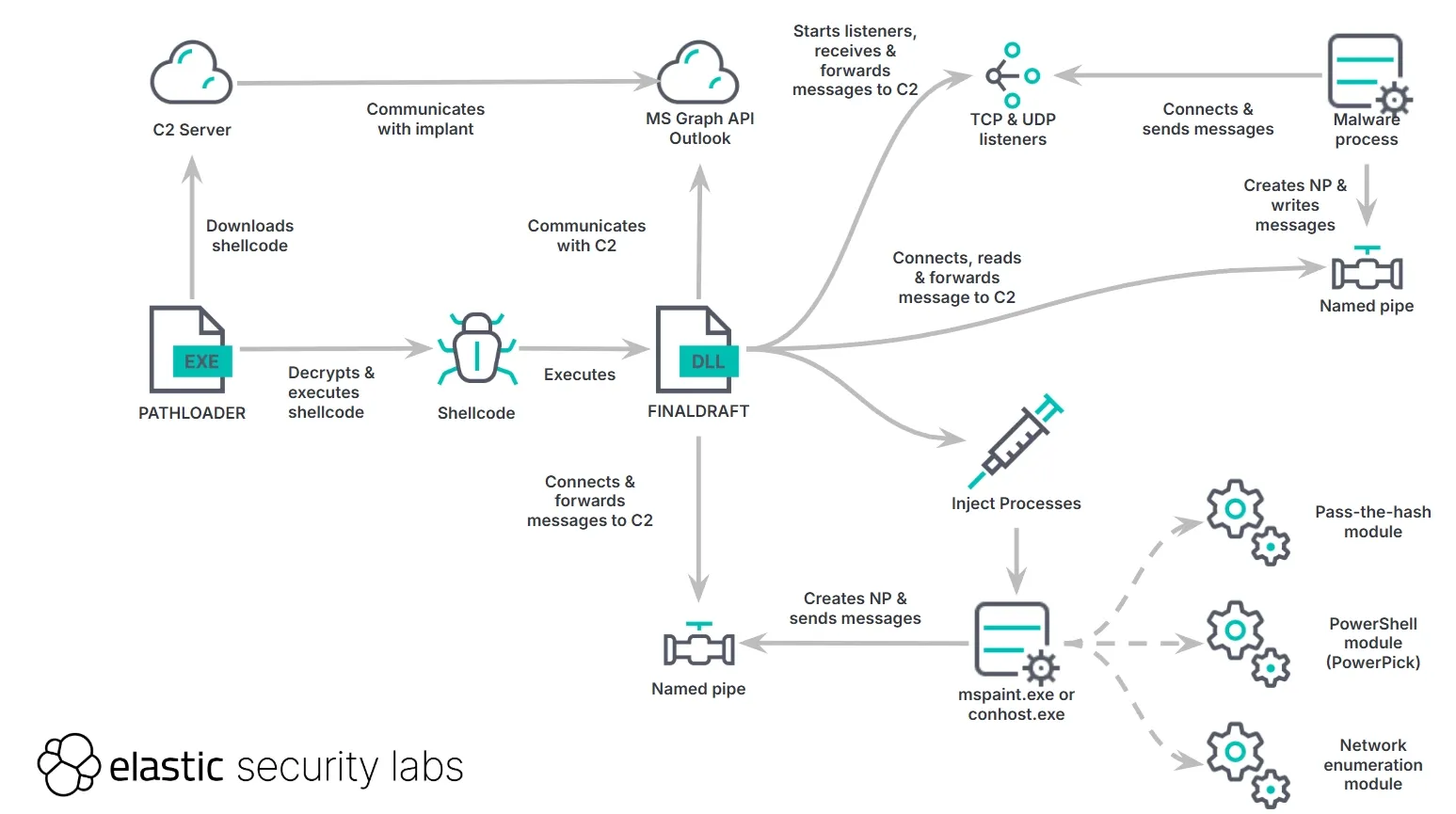
Elastic’s threat report, published February 13, details its discovery of a custom loader and backdoor that uses Microsoft’s Graph API for C2.
The latter, FINALDRAFT is a 64-bit malware written in C++ that “focuses on data exfiltration and process injection” – and which “abuses the Outlook mail service via the Microsoft Graph API.” (This same technique was, admittedly, previously observed in SIESTAGRAPH, a malware family that was also first reported by Elastic Security Labs in February 2023.)
Elastic said: “The Microsoft Graph API token is obtained by FINALDRAFT using the https://login.microsoftonline.com/common/oauth2/token endpoint. The refresh token used for this endpoint is located in the configuration.
Building refresh token request
Token refresh POST request
Once refreshed, the Microsoft Graph API token is stored in the following registry paths based on whether the user has administrator privileges:
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\UUID\<uuid_from_configuration>
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\UUID\<uuid_from_configuration>
This token is reused across requests, if it is still valid.
See full details in Elastic’s report here.
BadPilot
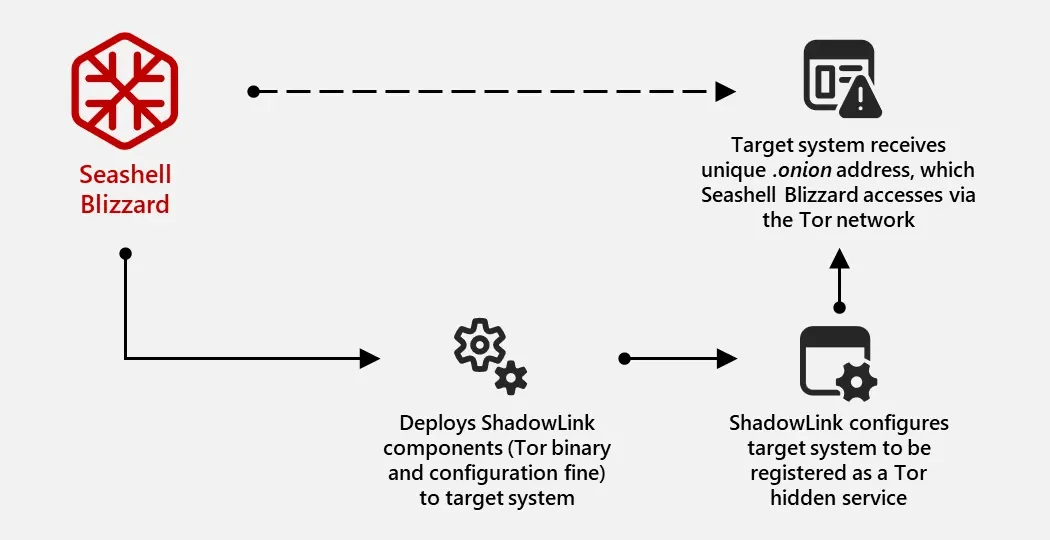
Microsoft, meanwhile, has been investigating a “multiyear initial access operation” by Russian state actor Seashell Blizzard that it dubs “BadPilot.”
Detailing a wide range of TTPs ised by the threat group, Microsoft noted that “among a subgroup of victims, Seashell Blizzard carried out unique post-compromise activity… In these cases, Seashell Blizzard deployed OpenSSH with a unique public key, allowing them to access compromised systems using an actor-controlled account and credential, in addition to a unique persistence and assured C2 method… [that it calls] ShadowLink.”
ShadowLink facilitates persistent remote access by configuring a compromised system to be registered as a Tor hidden service. This is achieved using a combination of Tor service binaries and a unique actor-defined Tor configuration file (referred as the ‘torrc’) configuring the system for remote access. Systems compromised with ShadowLink receive a unique .onion address, making them remotely accessible via the Tor network.
This capability allows Seashell Blizzard to bypass common exploit patterns of deploying a RAT, which commonly leverages some form of C2 to actor-controlled infrastructure that are often easily audited and identified by network administrators. Instead, by relying on Tor hidden services, the compromised system creates a persistent circuit to the Tor network, acting as a covert tunnel, effectively cloaking all inbound connections to the affected asset and limiting exposures from both the actor and victim environment.
Microsoft has more details here. Whilst we have chosen to focus, briefly, on some novel C2 techniques here, Redmond also highlights a range of other offensive techniques the group uses and has shared some limited hardening advice and IOCs in its advisory.
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
