
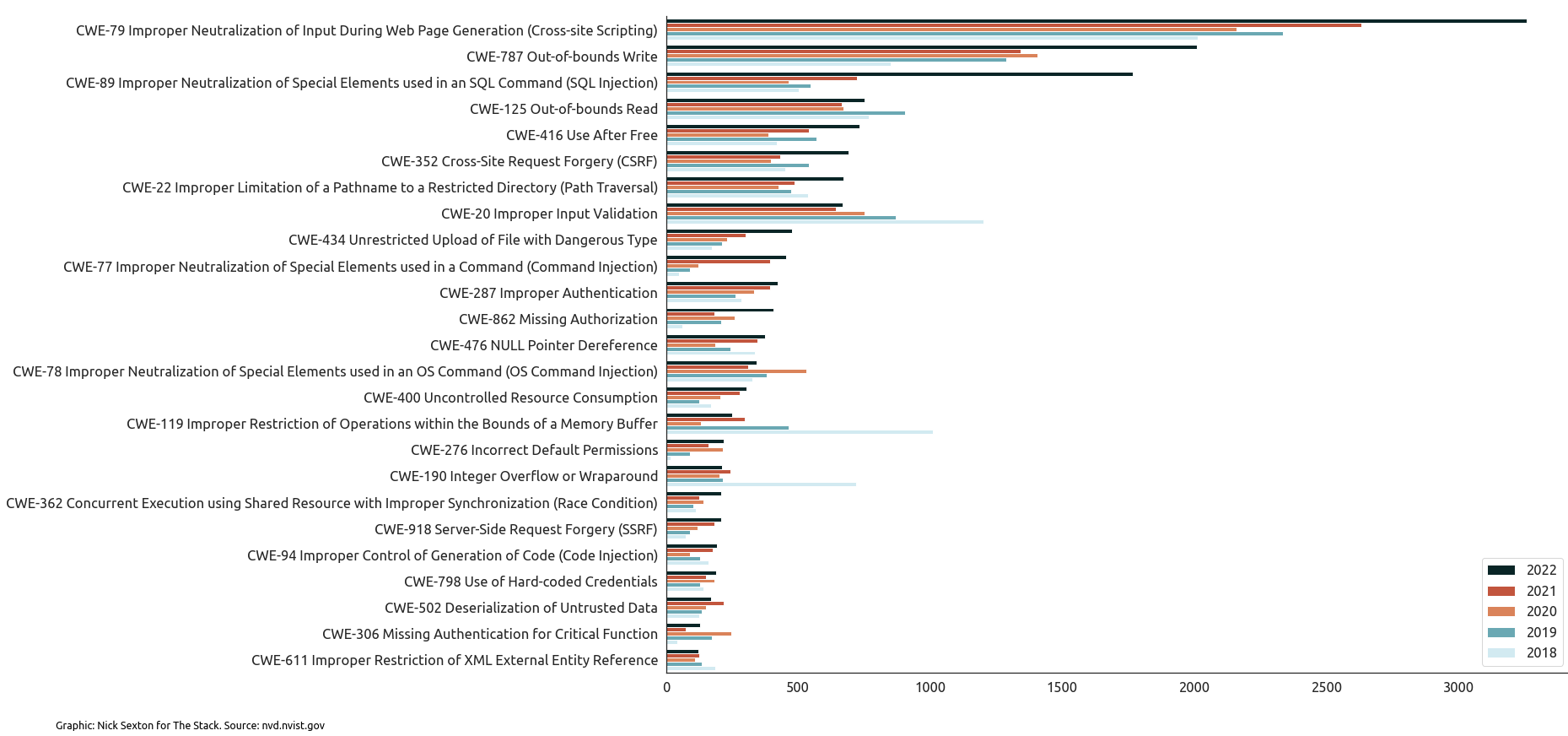
Analysis by The Stack of over 90,000 vulnerabilities revealed a sharp growth in bugs associated with widely known “CWEs” – or potentially exploitable weaknesses that can occur in architecture, design, code, or implementation and which could potentially have been caught upstream in a secure development process.
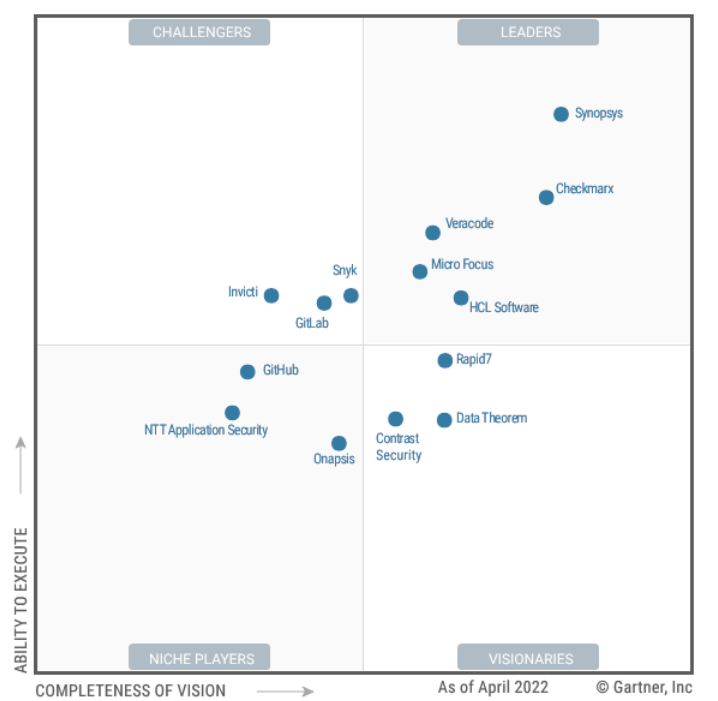
One control is to use fuzzing to find security and stability issues in software. A wide range of richly featured commercial Application Security Testing tools are available, although as Gartner’s Magic Quadrant for the segment notes, “customers have cited high costs: an increasingly common concern across many vendors.”
Fuzzing, which attempts to trigger errors by supplying a large volume of random inputs, can be particularly effective at finding common issues like cross-site scripting, and code injection vulnerabilities; both of which have seen their occurrence soar in recent years, as The Stack’s analysis in the chart below reveals.
For those operating on a tight budget, free fuzzing tools in 2023 are an option.
Here are 3 free fuzzing tools to consider using in 2023
1) ClusterFuzz
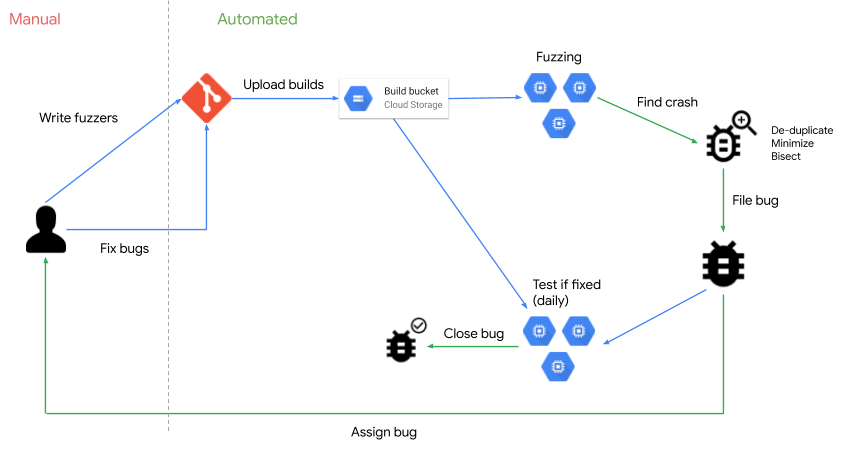
ClusterFuzz was open-sourced by Google under an Apache 2.0 license in 2021.
(Google uses ClusterFuzz to fuzz all of its own Google products…)
ClusterFuzz integrates fuzzing into a software project's development process: As of May 2022 it had already helped find ~29,000 bugs in Google (e.g. Chrome) and 36,000+ bugs in over 550 open source projects.
It is highly scalable – Google’s own instance runs on 100,000 VMs – and supports automatic bug filing, triage and closing for issue trackers (e.g. Monorail, Jira) as well as multiple coverage guided fuzzing engines (libFuzzer, AFL, AFL++ and Honggfuzz) for optimal results. You can a local instance of ClusterFuzz to test core functionality with support for Ubuntu (14.04 or later) Debian 8 or later and recent versions of macOS with homebrew , but perhaps frustratingly for most, many features of ClusterFuzz depend on Google Cloud Platform services.
Full ClusterFuzz documentation is here.
2) Ffuf
Ffuf (“Fuzz Faster you Fool”) is a free fuzzing tool written in Go and open-sourced under an MIT license.
It has a lively community for support and plenty of enthusiasts in the penetration testing community.
The command line-based tool, first released by Joohoi, can be used to fuzz a web application to discover directories, find usernames, enumerate virtual hosts, and even brute-force email/password combinations as well as to check how your applications react to unknown GET and POST requests.
You can find a useful guide here.
https://www.youtube.com/watch?v=aN3Nayvd7FU
3) Wfuzz
Wfuzz lets you perform complex web security attacks in different web application components such as: parameters, authentication, forms, directories/files, headers, etc. The web appl vulnerability scanner is supported by a range of plugins (as with all of these free fuzzing tools use at your own risk) and is highly modular.
As a command line utility that can be used in Kali Linux it is often used by penetration testers to discover web pages that don’t provide proper access control (e.g. admin panels or configuration files) as well as those pesky injection based vulnerabilities, such as directory traversals, SQL injections, XSS injections, and XXE injections that are so rife, as we showed in our chart at the top of this story. Wfuzz documentation is here.
For those looking to develop more of a DevSecOps approach however, tooling is a small part of the answer and in fact, many experts say that culture is key.
This includes applying operational discipline to automation scripts and infrastructure security posture and implement stronger version control on all code and components.
See also: Azure's CTO touts S2C2F Framework: IT leaders, pay heed
Ultimately a DevSecOps approach aims to make sure that you are secure in development (i.e. that code passes rigorous testing and analysis standards) and secure in delivery – to ensure unauthorised changes, drift and anomalies.
Those looking for commercial tools – and ones not in the Magic Quadrant at left above – could also continue offerings like CloudBees’ CI/CD software platform or equivalents, which let users orchestrate testing during development and enforce role-based access control, gates and thresholds at each stage – with automated deployment strategies for safer remediation or instantly mitigate defective code in production.
