
A vulnerability in multiple Fortinet products gives an unauthenticated remote attackers root access to its core product’s administrative interface – and the vulnerability has been exploited in the wild the company warned.
Given exploitation the company has warned customers to check for Indicators of Compromise.
https://twitter.com/Horizon3Attack/status/1579920320685035520
The Fortinet vulnerability – allocated CVE-2022-40684 – was reported to customers on October 7.
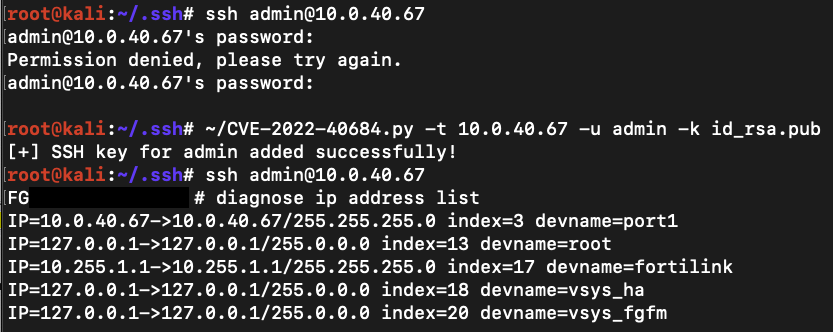
The patch was rapidly reverse engineered by security researchers at Horizon3 who said they would publish a proof-of-concept this week after having successfully gained access to “all management API endpoints”.
UPDATED October 12: CVE-2022-40684 POCs are circulating, the vulnerability is a breeze to exploit and there were about 50,000 folks out there with exposed endpoints according to security researchers. Adds comment at end.
FortiOS “the foundation of the Fortinet Security Fabric, consolidating many technologies and use cases into a simplified, single policy and management framework” is among the trio of solutions vulnerable.
Fortinet made details public today (October 10) in a security advisory.
The cybersecurity company has a large enterprise customer base including Siemens, Brazil’s BK Bank, and one of the world’s largest fresh fruit and vegetable suppliers, NYSE-listed Dole PLC, according to Fortinet.
The FortiOS administrative Trusted Hosts function "is not effective against this particular vulnerability" the company noted in response to discussion around the bug on Reddit. Having management interfaces -- like those affected by this vulnerability -- exposed to the internet obviously is not best practice but still happens regularly...
Fortinet vulnerability CVE-2022-40684: What’s affected?
The FortiProxy and FortiSwitchManager products are also affected, the company warned.
These are the vulnerable versions. Upgrades are available now.
- FortiOS version 7.2.0 through 7.2.1
- FortiOS version 7.0.0 through 7.0.6
- FortiProxy version 7.2.0
- FortiProxy version 7.0.0 through 7.0.6
- FortiSwitchManager version 7.2.0
- FortiSwitchManager version 7.0.0
Given exploitation in the wild Fortinet advised customers to start “immediately validating your systems against the following indicator of compromise in the device's logs: user="Local_Process_Access".
Customers unable to promptly update should disable HTTP/HTTPS administrative interface or throttle the IP addresses that can reach the administrative interface to trusted ones only, Fortinet said today.
Caitlin Condon, Manager, Vulnerability Risk Management Engineering at Rapid7, added in an emailed comment: "[This is] pretty much a worst-case scenario for security teams who rely on the affected devices (firewalls, web proxies, switch management platforms) to keep attackers out. While details are still a little fuzzy on when or how many attackers exploited this vulnerability prior to publication, Fortinet has now clearly indicated that it has been used in the wild—the implication being that it was used in a zero-day attack. Fortinet devices frequently sit at the edge of organizations’ networks, which makes them high-value targets. This vulnerability is likely to be exploited quickly and at scale, particularly for organizations that expose their management interfaces to the public internet.
They added: "History contains a lesson here. CVE-2018-13379, an information disclosure vuln in Fortinet's SSL VPN web portal from several years back, was one of the most prolifically exploited vulnerabilities in recent memory. Compromised credentials from those attacks were used for years to gain access to devices whose passwords weren't changed. Attackers who gain access to devices with CVE-2022-40684 may be similarly able to persist in victim environments by conducting administrative operations undetected.
"To be clear, this isn't a concern about the security of Fortinet products in general; it's a very specific risk posed by a critical bug that, from what we can see, was discovered, fixed, and communicated with appropriate urgency when exploitation was detected in the wild. Fortinet devices are hugely popular, and as researchers have been quick to point out the past few days, they're also pretty darn easy to identify on the internet. A quick internet survey by our Labs team identified well over a million devices running FortiOS. While certainly not all of those are exposed management interfaces, that number is a solid indicator of Fortinet devices' popularity—for attackers as well as legitimate users.
"Since the vulnerability was used in the wild before details were available, it's likely that initial exploitation was targeted. It's unlikely that it will stay targeted, as attackers and researchers have more time to reverse engineer the patch and develop exploits. Advanced threat actors may have specific motivations for targeting specific organizations, but we'll typically also see plenty of adversaries who are purely opportunistic, particularly when there's an easily discoverable target population. I won't speculate on who specifically is using CVE-2022-40684 (or to what ends) without solid data that we can validate ourselves.”
