
A British government-funded life sciences organisation with a drug discovery focus; a Singaporean software firm promising “enterprise grade security”; a Japanese power grid multinational; a Polish data centre support firm; a German automotive parts specialist; Bletchley Park…
These are among the entities potentially exposed to exploitation of their Fortinet firewalls, after 15,000 credentials including email addresses, passwords (some in plaintext) and firewall rules were dumped online.
The Fortinet credentials date back to zero day exploitation in 2022. It is not clear why the threat group behind them shared them now. Security researcher Kevin Beaumont has now published the email addresses however in a bid to help drive awareness among potentially affected organisations – many devices in the cache are still listed on Shodan.
Fortinet firewall data dump
As Beaumont noted on his blog: “Even if you patched back in 2022, you may still have been exploited as the configs were dumped years ago and only just released — you probably want to find out when you patched this vuln. Having a full device config including all firewall rules is… a lot of information.” (The list has been organised by TLD by Florian Roth here.)
The list of Fortinet credentials is unrelated to ongoing exploitation this month of another Fortinet zero day (now patched) that has been allocated CVE-2024-55591 and which is a CVSS 9.8 authentication bypass vulnerability that gives remote attackers super-admin privileges. If your organisation is on the list, at bare minimum you need to rotate creds.
See also: Fortinet zero day confirmed. CVE allocated. Attackers tunnelling
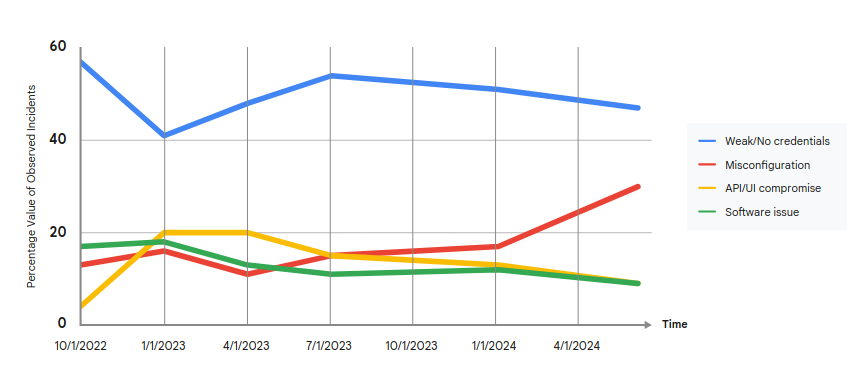
Its publication comes after Google Cloud Security highlighted that according to its telemetry and analysis, in the second half of 2024, credential-related vulnerabilities were the most common entry point for attackers. Lest anyone needed reminding that leaked credentials are bad:
A single stolen credential can initiate a chain reaction, granting attackers access to applications and data, both on-premises and in the cloud. This access can be further exploited to compromise infrastructure through remote access services, manipulate MFA, and establish a trusted presence for subsequent social engineering attacks. Stolen credentials can also be used to register malicious applications for persistent access to communication platforms, or to obtain long-lived credentials like access keys and certificates, further solidifying a foothold. Ultimately, an initial credential compromise can enable attackers to pivot across on-premises or cloud infrastructure, escalate privileges, and establish persistence, resulting in stolen data, extortion, and destructive activities – Google Cloud Security
Nearly half (46.4%) of the security alerts seen by Google Cloud’s security team meanwhile were due to overprivileged service accounts. So check those emails for exposure and rotate credentials regularly. Perhaps, as AWS Security said this week, ideally “never create long-term credentials in the first place…" if that’s conceivably a real-world option for you.
