February’s Patch Tuesday brings the post-Valentine’s Day hangover of 75 bug fixes from Microsoft including three for CVEs known to be exploited in the wild: CVE-2023-21715, CVE-2023-23376 , and CVE-2023-21823.
Strikingly, more than half of the bugs fixed this month are remote code execution (RCE) vulnerabilities.
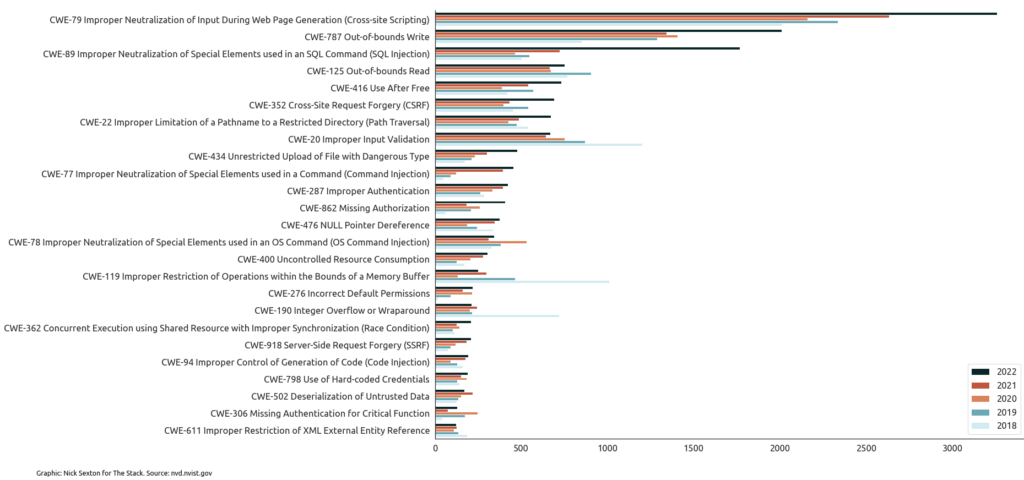
(A record 26,448 software security flaws were reported in 2022, with the number of critical vulnerabilities up 59% on 2021 to 4,135, according to analysis by The Stack of Common Vulnerabilities and Exposures (CVEs) data. Unpatched software is a top three access route for hackers and patching, says the UK’s National Cyber Security Centre (NCSC) “remains the single most important thing you can do to secure your technology.”)
Here are the three bugs disclosed in February 2023’s Patch Tuesday that are being actively exploited.
February Patch Tuesday: The 3 bugs getting exploited
CVE-2023-21715 is a security bypass/EOP bug in Microsoft Publisher. Microsoft says an “attacker who successfully exploited this vulnerability could bypass Office macro policies used to block untrusted or malicious files.” The bug is a good reminder that not every vulnerability getting exploited is an all-singing critical RCE bug. This ranks a modest CVSS 7.3, requires local access and user interaction to exploit, but it’s still getting used – bypassing Office macro policies used to block untrusted or malicious files is a powerful and useful thing for attackers. Unusually, this vulnerability find was attributed not to a Microsoft security team but to a specific Microsoft individual, Hidetake Jo, who is Principal Security Architect at Microsoft. Microsoft’s increasingly threadbare security updates mean we have no idea how widely it is getting exploited, but patch it regardless.
CVE-2023-23376 is a Windows Common Log File System Driver Elevation of Privilege (EOP) vulnerability. Microsoft notes tersely that exploitation gives SYSTEM. It requires local access but no user interaction and has a CVSS score of 7.8. Microsoft credits its Microsoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC) teams with the disclosure. As the Zero Day Initiative puts it: “This is likely being chained with an RCE bug to spread malware or ransomware. Considering this was discovered by Microsoft’s Threat Intelligence Center (aka MSTIC), it could mean it was used by advanced threat actor…”
CVE-2023-21823 is a Windows Graphics Component RCE that was reported by Mandiant. Microsoft describes it as an RCE but also says it requires local access. Exploitation gives SYSTEM. Privileges. Microsoft Store will automatically update affected customers unless you have disabled automatic updates for the Microsoft Store, in which case you will need to revisit Get updates for apps and games in Microsoft Store.
Also to look out for in the February 2023 Patch Tuesday update from Microsoft are nine critical bugs including a Microsoft Word RCE bug with a CVSS 9.8 rating. CVE-2023-21716, reported by Joshua Drake, in Microsoft’s words, allows an “unauthenticated attacker [to] send a malicious e-mail containing an RTF payload that would allow them to gain access to execute commands within the application used to open the malicious file.
Adobe meanwhile released nine patches addressing 28 CVEs in Adobe Photoshop, Substance 3D Stager, Animate, InDesign, Bridge, FrameMaker, Connect, and After Effects. A PhotoShop patch is among them that fixes five bugs, three of which are rated Critical. Premier Rush, corrects two Critical-rated code execution bugs.
For what it is worth, The Stack has noted a sharp rise in frequency of many of the top 25 most dangerous Common Weakness Enumeration (CWE) types over the past five years, for example cross-site scripting (XSS) and SQL Injection weaknesses. (CWEs are potentially exploitable weaknesses that can occur in architecture, design, code, or implementation: The CWE open standard “dictionary” is maintained by The MITRE Corporation.)









