
The FBI quietly deleted “PlugX” malware from over 4,200 infected computers across the US after being given permission to do so via nine court orders – in an extraordinary action led by French law enforcement.
End users were unaware that the FBI was remotely accessing their devices.
The action took place after French law enforcement gained access to the PlugX command and control (C2) server and French cybersecurity firm Sekoia.io identified commands to delete the persistent malware – believed to be installed on potentially millions of machines around the world.
The FBI said that PlugX was likely installed by a China-backed threat group called Mustang Panda, which it claimed “has infiltrated the computer systems of numerous government and private organizations, including in the United States…foreign targets include European shipping companies in 2024, several European Governments from 2021 to 2023,” it added.
The action came after Sekoia in April 2024 detailed its C2 capture and ability to delete the malware – and called on national CERTs and law enforcement agencies "to contact us if they wished to disinfect systems within their countries, promoting the concept of sovereign disinfection and addressing the legal aspects associated with such operations."
Following this call, and with the support of the Paris Public Prosecutor’s Office and the French Gendarmerie National Cyber Unit, more than twenty countries responded, pushing us to move from theory to practice" the company said in a post it published on Boxing Day. It was not immediately clear how many authorities took action like that of the FBI.
Join peers following The Stack on LinkedIn
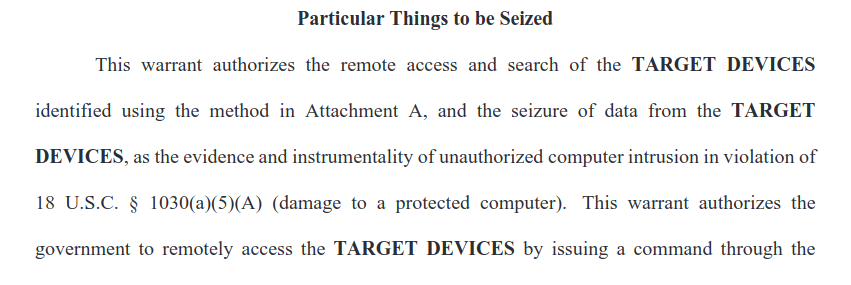
The agency is now “providing notice to U.S. owners of Windows-based computers affected by this court-authorized operation” the Department of Justice said Tuesday in an affidavit revealing the operation.
It did not do so earlier/in advance because “premature disclosure to the public at large or to individual owners of the TARGET DEVICES could result in publicity that would then give the hackers the opportunity to make changes to the malware, enabling continued or additional damage to remaining victims’ devices” the FBI said in unsealed court papers.
FBI action against PlugX malware: Legal because...
The DOJ said Federal Rule of Criminal Procedure 41(b)(6) (which details when search warrants can be granted) and Title 18, United States Code, Section 1030(a)(5)(A) (part of the Computer Fraud and Abuse Act) gave it the authority to act without the computer/network owners’ knowing.
“This variant of PlugX malware spreads through a computer’s USB port, infecting attached USB devices, and then potentially spreading to other Windows-based computers that the USB device is later plugged into. Once it has infected the victim computer, the malware remains on the machine (maintains persistence), in part by creating registry keys which automatically run the PlugX application when the computer is started. Owners of computers infected by PlugX malware are typically unaware of the infection” – FBI
“The Department of Justice prioritizes proactively disrupting cyber threats to protect U.S. victims from harm, even as we work to arrest and prosecute the perpetrators,” said Assistant Attorney General Matthew G. Olsen of the DOJ’s National Security Division in a press release. “This operation, like other recent technical operations against Chinese and Russian hacking groups like Volt Typhoon, Flax Typhoon, and APT28, has depended on strong partnerships to successfully counter malicious cyber activity.”
“I commend partners in the French government and private sector for spearheading this international operation to defend global cybersecurity.”
