A botnet formed from an army of “evil” routers has initiated a “record-breaking” DDoS attack, security researchers have claimed.
Infosec investigators from OVHCloud, a major European cloud provider, have observed a “sharp increase” in the rate of Distributed Denial of Services attacks (DDoS) attacks since the beginning of 2023, with a “new trend” seeing threat actors bombard their targets with high packet rate attacks.
This flurry of DDoS assaults culminated in a truly massive attack which leveraged compromised routers (network core devices, rather than domestic routers) to unleash an attack of an epic scale.
“This could be a new era for packet rate attacks: with botnets possibly capable of issuing billions of packets per second. It could seriously challenge how anti-DDoS infrastructures are built and scaled,” wrote Sebastien Meriot and Christophe Bacara.
DDoS attacks are, of course, a notorious and slightly old-school way to bring down online services, often relying on botnets made up of vast numbers of zombie devices. In the past, attacks tended to follower familiar patterns.
“Just craft as many packets as you can in an attempt to reach the highest possible bit rate (or packet rate) to cripple your target’s networking capabilities,” the researchers wrote. “This is what happened with the Mirai botnet back in 2016 which was the first one to generate more than 1 Tbps (Terabit per second).”
Since then, several botnets have surpassed Mirai and surged up to 3.47 Tbps.
However, attacks of over 1 Tbps remained “quite rare… until recently,” the researchers added.
See also: France fends off unprecedented DDoS attacks as it gears up for Olympian challenge
They continued: “Starting from November of [2023], a significant acceleration of the trend has been observed by our teams at OVHcloud. While DDoS reaching 1 Tbps or above were occasional, they aren’t anymore. In the past 18 months, we went from 1+ Tbps attacks being quite rare, then weekly, to almost daily (averaged out over one week). The highest bit rate we observed during that period was ~2.5 Tbps.”
The packet rate attacks involve malicious actors spraying their targets with garbage data to saturate bandwidth (network-layer attacks) or sending a lot of application requests to cause excessive CPU or memory usage (application-layer attacks).
“Packet rate attacks are quite effective since dealing with a lot of small packets is usually harder than dealing with bigger but less numerous packets,” the researchers continued. “This is because the computing cost is generally higher…. If your job is to deal mostly with payloads, bandwidth may be the hard limit ; but if your job is to deal mostly with packet headers, packet rate is the hard limit. That’s why in most conditions, dealing with small packets is harder than dealing with big packets.”
The team found that a 10 Gbps DDoS attack using big packets of 1480 bytes yields roughly 0.85 Mpps, whilst 10 Gbps using the smallest packets of 84 bytes on wire for Ethernet yields a 14.88 Mpps.
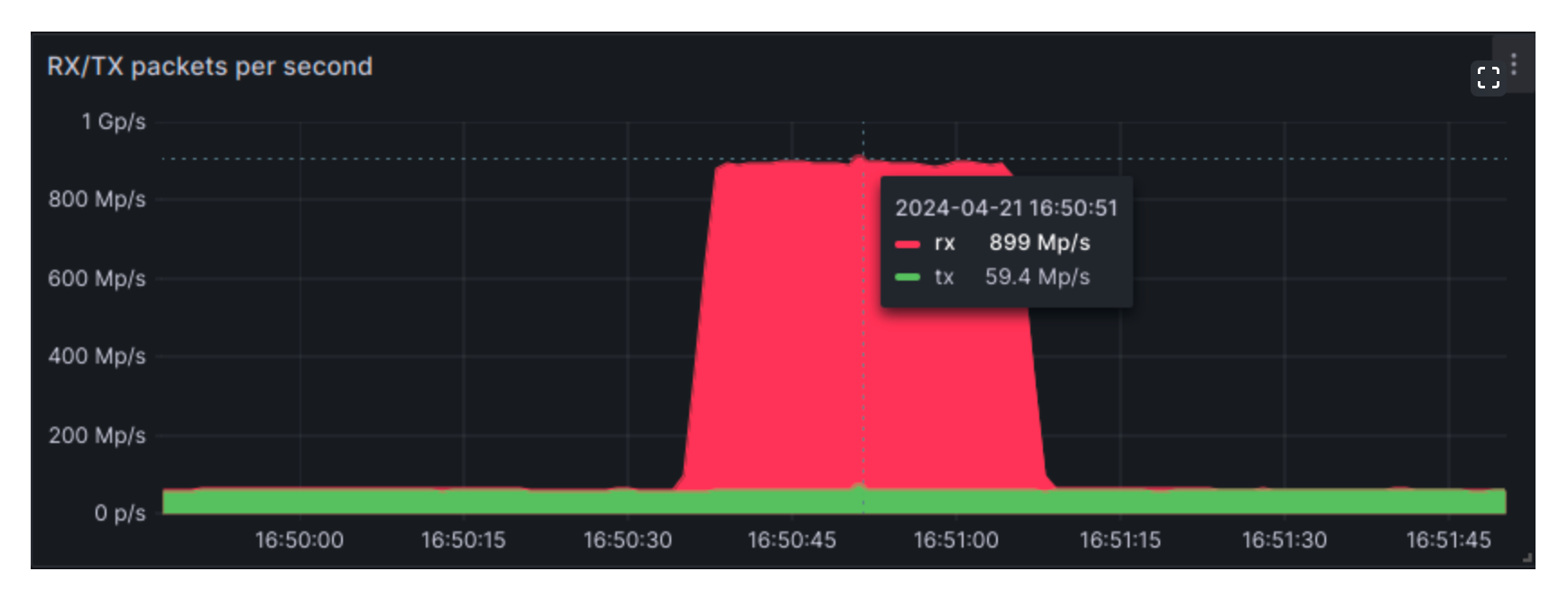
DDoS attacks relying on high packet rates “are not new and network operators all over the world had to face such attacks at least once”, OVHCloud continued. On June 21, 2020, Akamai mitigated the largest packet-per-second (PPS) distributed denial-of-service (DDoS) attack ever recorded on its platform, for instance, which generated 809 million packets per second (Mpps) during an assault on a large European bank.
However, most packet rate attacks come in at well below 100 Mpps, according to OVHCloud, because “generating a lot of small packets is harder than generating big ones (you need much more compute – similarly to processing) and is harder to hide from network monitoring and anti-abuse systems.”
Packet rate attacks started to “seriously get some attention” at OVHcloud two years ago, when it fended off a “gigantic” UDP flood for more than 6 hours.
Over the past 18 months, it has gone from mitigating "a few" 100 Mpps DDoS attacks each week to "tens or even hundreds". After batting off several 500+ Mpps attacks at the beginning of 2024, including one peaking at 620 Mpps, it faced a “record-breaking” DDoS attack in April which reached roughly 840 Mpps - slightly above the previous record reported by Akamai.
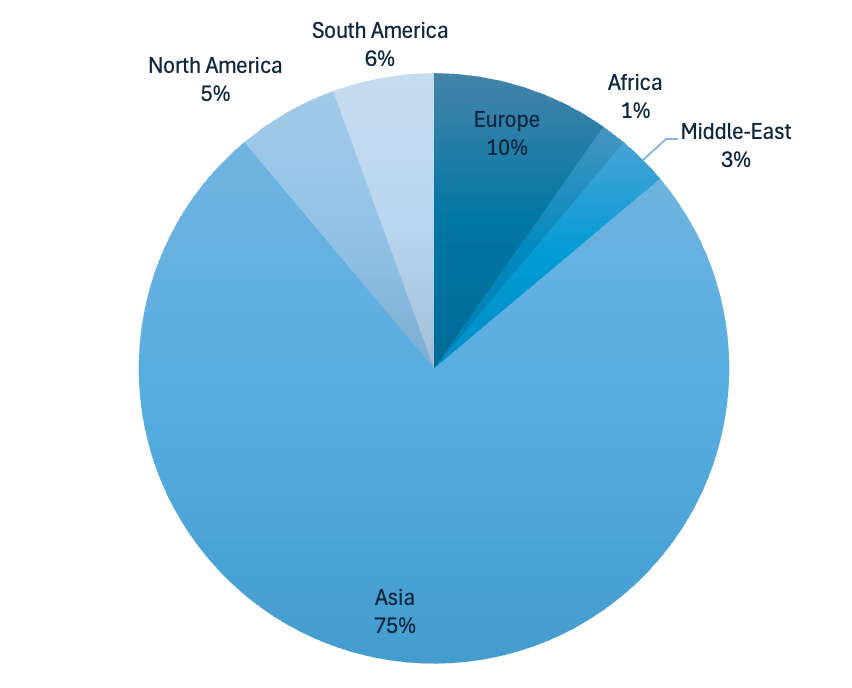
The attack made OVHCloud question its assumption that it was impossible to send a huge DDoS attack from a small number of locations.
Two-thirds of the total packets entered from only four points of presence (PoP), all located in the US, with three of them on the West Coast, making the team rethink their previous stance.
“Based on this assumption, our infrastructures are scaled horizontally, spread worldwide, and they absorb the load more easily. However, the traffic distribution of the 840 Mpps attack has strongly questioned this assumption. While we do have the local capacity to mitigate this attack, we will consider to adjust the general scaling and distribution model of our anti-DDoS infrastructures to ensure to cope with future (and probably bigger) attacks.”
The researchers claimed that a significant number of the IPs were related to a specific brand of router. The researchers proposed poor management practices resulted in administration interfaces being exposed online. Victims may also have neglected to install patches for CVEs, making their routers vulnerable.
This finding suggests defenders face a growing threat from attackers “leveraging compromised network core devices to perform powerful attacks.”
“While any high-end server could perfectly be capable of generating packet rates at this scale, they will probably be limited by the actual amount of available public bandwidth,” OVHCloud added. “Because of their location within the network, core devices are much less affected by this assertion: they are generally connected to even bigger devices using high-capacity network links. Moreover, the mitigations implemented by network administrators to identify abnormal behaviours on the network — such as servers initiating DDoS attacks — can be bypassed in this case because routers are generally not subject to these measures.”
The team said they would “definitely take this new threat into account” when building and scaling new anti-DDoS infrastructures.








