
A VMware vulnerability is being exploited in the wild to gain full administrative access to ESXi hypervisors and then drop ransomware.
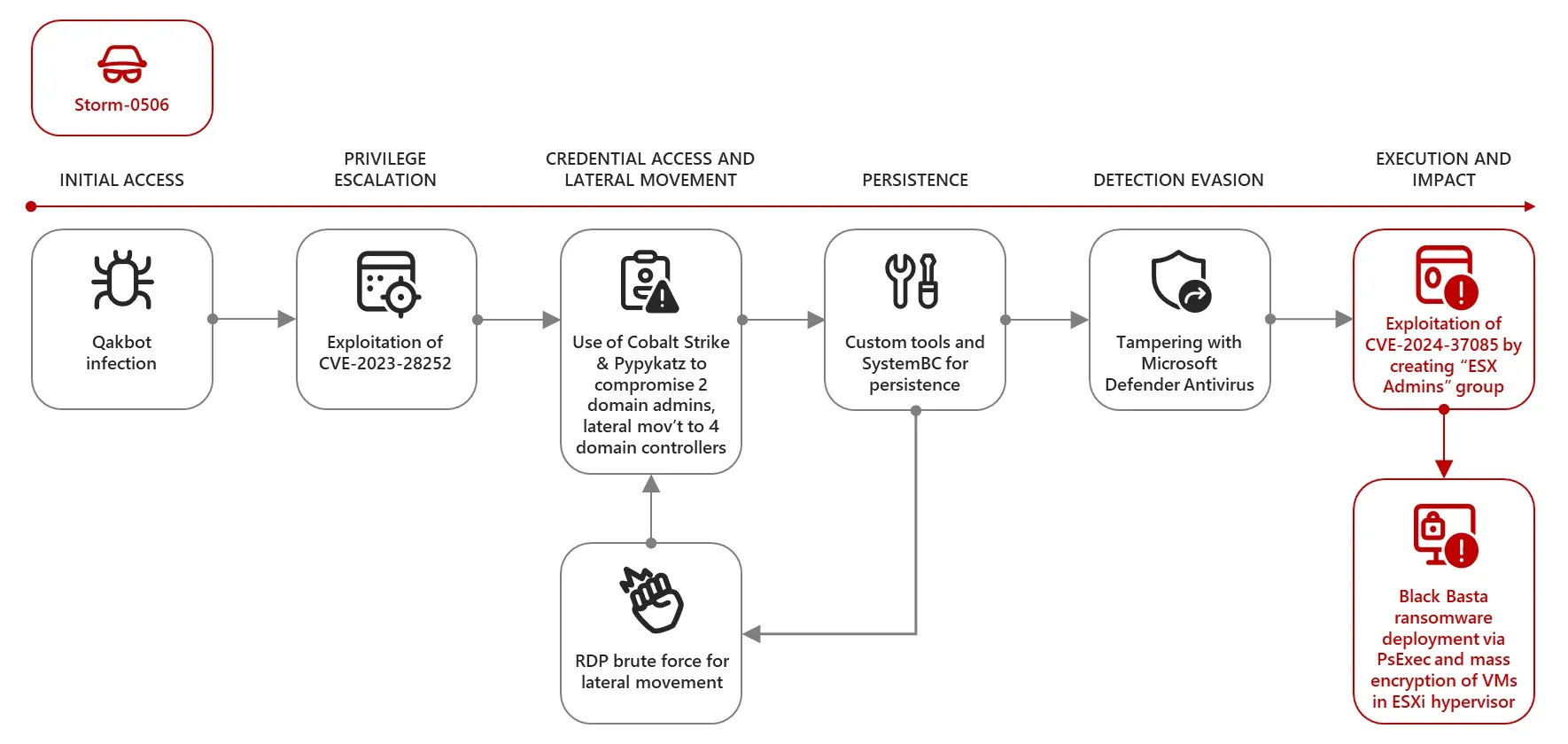
Several threat groups are now exploiting the bug, allocated CVE-2024-37085. Exploitation has sometimes been followed by Akira and Black Basta ransomware deployments, said Microsoft Threat Intelligence.
Attackers are effectively abusing the expansive permissions granted by VMware to a group called ‘ESX Admins’ that it creates by default when users opt to manage their VMware hypervisor hosts via Active Directory.
These permissions, per CVE-2024-37085, continue to exist in “ghost form” even if a conscientious administrator restricts them or deletes the group.*
“This group is not a built-in group in Active Directory and does not exist by default” said Microsoft – apparently keen to emphasise that its perennially hard-to-secure and generally opaque service is not implicated.
CVE-2024-37085: Can we call it Hyperhaunt?
VMware has documented for 14 years (e.g. here) that it “provides a default AD group named ‘ESX Admins’ that automatically gets added to each host by default” when using AD to manage hypervisor hosts – and has cautioned in its documentation that “not only is this group added to each host, but by default it is also granted full administrative rights.”
But as Microsoft noted in a July 29 blog, VMware ESXi hypervisors joined to an AD domain “consider any member of a domain group named ‘ESX Admins’ to have full administrative access by default”.
That's right: It’s not just the default group that VMware creates.
It is ANY GROUP with that name.
As Microsoft found, ESXi hypervisors do not validate that the ESX Admins group exists when the host server is joined to a domain and “still treats any members of a group with this name with full administrative access, even if the group did not originally exist.” (Our italics; Microsoft’s semantics.)
“Additionally, the membership in the group is determined by name and not by security identifier (SID)” Microsoft sniffed, rightly, in its blog.
“The name’s Admin, ESX Admin”
Microsoft Threat Intelligence, detailing how CVE-2024-3705 is being exploited, said threat groups are adding the “ESX Admins” group to a domain they have control over and adding a user to it.
As a result of the bug they can “escalate privileges to full administrative access to domain-joined ESXi hypervisors by creating such a group, and then adding themselves, or other users in their control, to the group.”
They can also exploit the bug by renaming any group in the domain “ESX Admins” and adding a user. Even if a network admin assigns another group to be the management group for the ESXi hypervisor, the full admin privileges “ESX Admins” members get are not immediately removed, Microsoft said. (It has not seen those two latter approaches deployed.)
VMware gives the “authentication bypass” vulnerability a CVSS rating of just a “medium” 6.8 and pushed patches for it and other bugs on July 25.
Don’t panic outright: Exploitation requires a threat actor to already control what Microsoft admitted would be “a highly privileged” AD user. But if you don’t want someone who popped your AD to pillage your ESXi hypervisors that you used AD for user management of, then patch up, sharpish.
Exploitation, perhaps obviously to some readers, gives an attacker “full administrative access to the ESXi hypervisors, allowing threat actors to encrypt the file system of the hypervisor [or] exfiltrate data or move laterally within the network” added Microsoft Threat Intelligence.
It has sensible mitigations in its blog.
*Let's call it "Hyperhaunt" as a result.
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
