
Elon Musk has warned that the Starlink terminals in Ukraine could be targeted by Russia, days after re-routing satellites over the embattled country and promising delivery of more receiver terminals.
He said on Twitter: "Starlink is the only non-Russian communications system still working in some parts of Ukraine, so probability of being targeted is high. Please use with caution" -- pressed on whether he meant they ran the risk of being hacked (as well as potentially bombed) he noted: "Almost all Viasat Ukraine user terminals were rendered permanently unusable by a Russian cyberattack on day of invasion, so … yes."
His comments came after Viasat, a US-owned broadband satellite and other aerospace provider, said its KA-SAT broadband services had been badly affectly by what it believed to be a cyber-attack. The subsequent outage took down satellite broadband across Ukraine and also affected services more broadly across Europe.
One affected customer lost remote monitoring capabilities for 5,800 wind turbines as a result.
Multiple unconfirmed reports suggest Viasat users' modems were "bricked" or rendered completely inoperable during the attack, which only appears to have hit a large subset of users on certain bands.
The incident comes after the NSA in January 2022 warned that "Very Small Aperture Terminal" (VSAT) satellite networks leave communications over these links "at risk of being exposed and may be targeted by adversaries for the sensitive information they contain or to compromise connected networks.
"Most of these links are unencrypted, relying on frequency separation or predictable frequency hopping rather than encryption to separate communications. Public vulnerability research has found certain terminal equipment vulnerable to compromise and illicit firmware modification. NSA recommends that VSAT networks enable any available transmission security (TRANSEC) protections, segment and encrypt network communications before transmitting across the VSAT links, and keep VSAT equipment and firmware up to date."
See also: KA-SAT issues hit German wind farm

John Scott-Railton, a senior researcher at Canada's CitizenLab, warned that cyber attacks on Starlink terminals in Ukraine were far from the only risk for users.
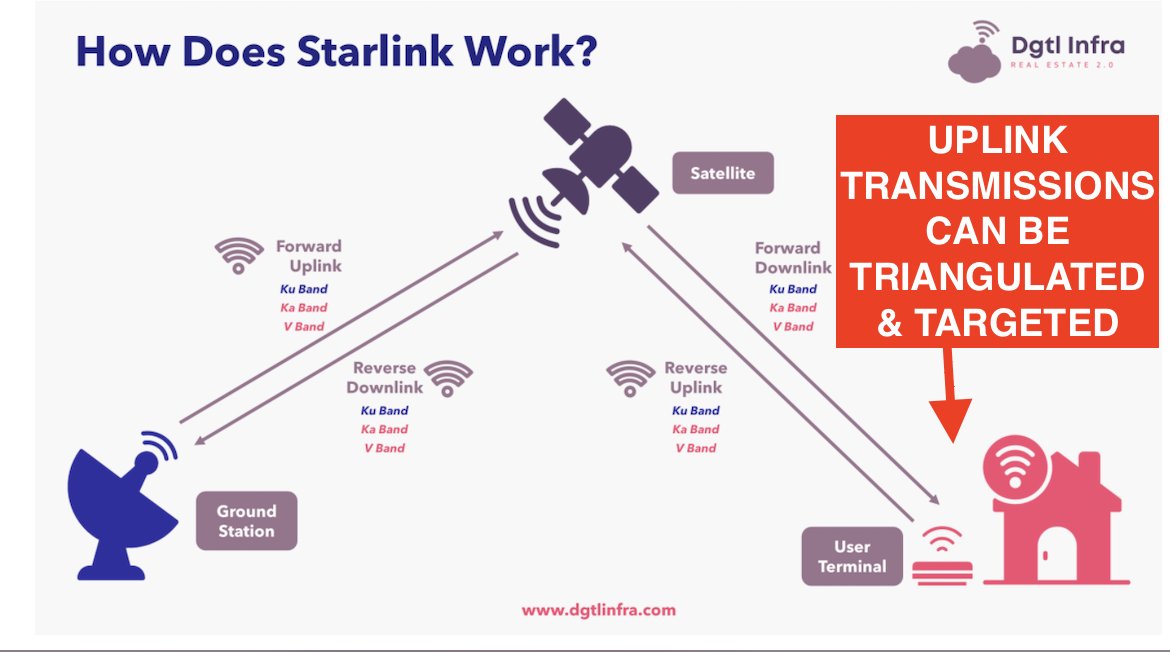
He noted: "Remember: if Putin controls the air above Ukraine, users' uplink transmissions become beacons for airstrikes... there are various ways to spot, geolocate, and drop a missile on VSAT satellite internet terminals -- and Russia has recent battle-tested experience doing just this in Syria..."
He added: "In Syria, ISIS reportedly came up w/ various tactics to avoid being killed by strikes against their satellite internet terminals. E.g. Distancing dishes from their installations, covertly taking a connection from civilian internet cafes' VSATs, etc.
"Deadly cat & mouse...
"Early in a conflict w/disrupted internet, satellite internet feels like a savior. But it quickly introduces *very real, deadly new vulnerabilities* If you don't understand them, people die needlessly until they learn and adapt. Remember," he added in a Twitter thread, "encryption doesn't prevent GEOLOCATION based on radio emissions.
"A smartphone or satcom user can be on encrypted call, using a VPN, etc. etc. correctly believing that nobody is LISTENING to them... right up until the instant they are nabbed. Now that Starlink devices are headed into an active conflict zone, though, *possible* risks are about to get battle tested. I hope that OPSEC is front of mind as decisions are made about terminal distribution, use and placement."
In 2020 an Oxford University-based security researcher used £270 ($300) of home television equipment to capture terabytes of real-world satellite traffic — including sensitive data from “some of the world’s largest organisations"; demonstrating that an attacker can intercept and even modify VSAT connections using standard satellite television equipment and creating a purpose built forensic tool dubbed "GSExtract" designed to "recover sensitive IP traffic from even highly corrupted maritime VSAT feeds collected on consumer-grade equipment."
As James Pavur noted at the time, a lack of encryption was a key issue for many: "Satellite transmissions cover vast distances and are subject to speed-of-light latency effects and packet loss which can impair the function of encryption schemes designed for high-reliability terrestrial environments (e.g. by requiring re-transmission of corrupted key materials)... Moreover, satellites themselves are limited in terms of computing capabilities and any on-board cryptographic operation risks trading off with other mission functionality.”
As Scott-Railton noted however, it's not just that risk of traffic interception that's concerning, it is that regular use paints a geolocated target on the users' forehead. (There's only so much distance a healthy length of ethernet cable from receiver to device can give you from an airstrike that may not be accurate anyway.)
