
The Ministry of Defence (MOD) faces a "misaligned culture, endemic obsolescence, [and] inadequate cyber resilience" its own new Cyber Resilience Strategy for Defence report warned this week -- as it laid out plans to try and bring improved cyber hygiene to the MOD's sprawling set of agencies and organisations by 2030.
Led by MOD CIO Charles Forte and MOD Second Permanent Under Secretary, Laurence Lee, the report was delivered and will be implemented by a team headed up by Christine Maxwell, MOD's Director of Cyber Defence and Risk, who said that the report "sets out the real foundational approach we are taking" across the MOD.
Among the strategy's promises is more openess from MOD, which will aim to "adopt a default ‘share’ posture... where policy permits" and, critically, to "reset the relationship" with industry: something the report warns may require an "open mindset to resetting security relationships" from enterprise partners as MOD looks to push resilience requirements further up it supply food chain, to include resilience audits and remediation.
Here are The Stack's seven key takeaways from the MOD Cyber Resilience Strategy for Defence report, which focuses on the strategic priorities for the Ministry of Defence that will be "directed and cohered" by Defence Digital.

1) MOD's Cyber Resilience Strategy has a singular purpose...
"The strategy pursues a central aim - for Defence’s critical functions to be significantly hardened to cyber-attack by 2026, with all Defence organisations resilient to known vulnerabilities and attack methods no later than 2030," the report notes. "Delivering the aim will require immediate focus on delivering the basics of cyber resilience."
2) It's going to take a lot of help from industry...
Turning the vast and unwieldy Defence sector around when it comes to cyber resilience is going to be no mean feat. Private sector partnerships will be a big part of the efforts, the report suggests, noting that "our relationship with industry will fundamentally shift to work ever closer in delivering wider defence and security..."
Industry will also need to deliver "capability that is Secure by Design and integrated with our defences whilst actively protecting our data throughout the supply chain," the report warns (a call to arms that comes as a major network protection vendor was caught -- for the second time in 24 months -- this week shipping its flagship perimeter security platform with an unauthenticated API to its management interface, giving full RCE).
This "reset" in private sector relationships will include "refreshing the Defence Cyber Protection Partnership process" and securing "controlled and auditable access to data held on Industry or Defence’s networks" as part of plans to ensure MOD can audit the cyber resilience of its suppliers amid mounting supply chain risk.

3) Getting rid of and risk-managing obsolete technologies
From aging Operating Systems to the use of punched paper tape to distribute crypt-keys, there is no shortage of aging technology in play across the MOD -- understandably for an organisation over 360 years old, and one which, like its counterpart in the US, is grappling with the need to dramatically adjust its procurement approach.
(Risk aversion, waterfall processes and other issues mean rapidly evolving digital technology often runs the risk of being borderline obsolete by the time people in uniform get their hands on it.)
See also: The Big Interview with US Army CIO Raj Iyer
When it comes to legacy technology, the new Cyber Resilience Strategy for Defence report notes that its 25 agencies will need to "accelerate the elimination of obsolete technologies across the digital environment" and emphasises that where they remain in-service, they "must be actively risk managed and funded..."
4) Identify critical systems, improve compliance
Like many setting out on building a cohesive cyber resilience strategy, identifying key assets and setting red lines for each is a key starting point and the report reflects that, noting a need to: "Define our critical systems and the levels of resilience each needs; engage with our critical suppliers to improve the supply chain security; provide new pan-Defence cyber security policy" and more specifically in the wake of mounting threats "continually evolve our risk response plans and use key risk indicators to measure progress across all Defence organisations."
If execution goes as planned, growing scrutiny can be expected, with the promise of "compliance checks across Defence organisations and industry [our italics] to identify and remediate shortcomings in cyber resilience."
5) Secure by Design
While the report doesn't spell out those compliance checks, it does emphasise a need for a "Secure by Design" approaches and calls on all parties to create mechanisms that "support SROs and delivery teams to assess security risks clearly before considering options to trade out security: "We will," it promises, "define and communicate the key principles of Secure by Design based on international standards and NCSC guidance."
The Cyber Resilience Strategy for Defence also promises to "revise mechanisms for escalating non-compliance..."
6) Rapidly detect and respond
MOD wants to "aggressively implement higher quality detection methods" -- no doubt music to industry partners' ears -- and "assertively automate our processes to reduce the workload on the cyber defenders and increase the speed of response". That automation and improved tooling will be critical in a sector that is fighting a consistently losing battle to retain digital talent in a world of red-hot salary offerings from the private sector.
As Army Chief Data Officer (CDO) Brigadier Stefan Crossfield noted last summer: "The Army are working on what we need and how we can retain the right skills in a marketplace that’s highly competitive and evolving quickly. We’ve experimented with apprenticeships in the DevSecOps world, but ultimately many leave us for better paid roles. The result is we are currently dominated by 'As A Service' contracts... The RAF are currently working to train a number of software engineers and it will be fascinating to see whether or not they retain them in service and see a return on that investment. Ultimately, the Army needs to think hard about value for money and sustainability of capability – and there is a lot of work still to do to overcome this hurdle."

7) Zero Trust, general modernisation
Defence Digital wants to see MOD "implement a zero-trust architecture that applies the appropriate security
controls based on a data centric security model; transform the crypt-key capability to keep our secrets secret [few details here on this longstanding yet hard-to-execute aspiration]; deliver a modern, centralised identity and access management service to make sure the right individuals to access to the right resources at the right time, and for the right reasons; create a service catalogue of trusted security control solutions that must be adopted across Defence [and] trial and test new security solutions early to be on the front foot".
These aspirations come as MOD continues to seek what it describes as a "Digital Backbone" connecting "sensors, effectors and deciders across military and business domains and with partners, driving integration and interoperability across domains and platforms" -- as MOD CIO Charles Forte has previously put it, to: "connect our decision-makers across our military and business domains, to enable... improved Defence outcomes."
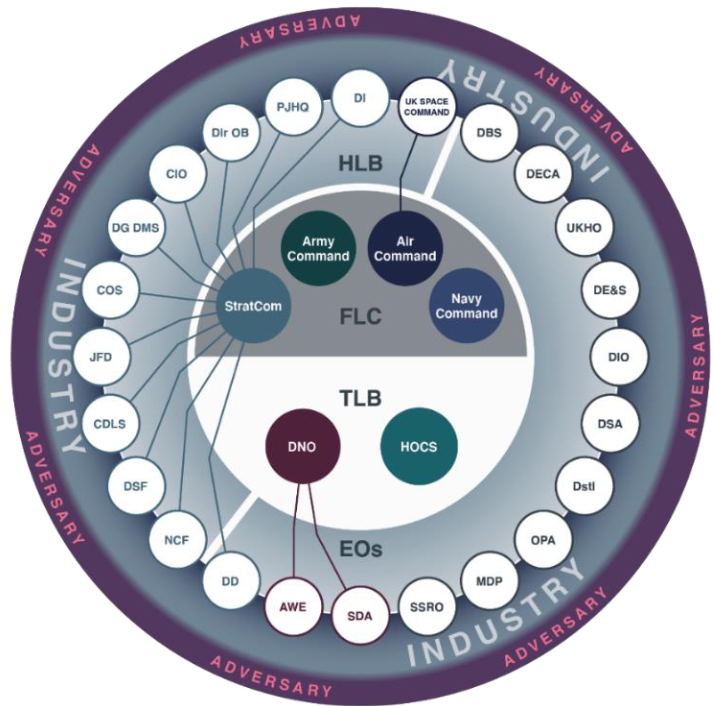
Who's making this all happen?
"Based on the national effort led by Government, Cyber Defence and Risk will direct the activities that must be completed to deliver the vision," the report notes, with MOD's various operating authorities and SROs responsible for overseeing the delivery of Secure by Design capabilities delivered by "equipment capability programmes, industry and delivery teams", while the Defensive Cyber Joint User will perform the role its name suggests.
There's a lot of moving parts to MOD, some of them move very slowly and we wish Defence Digital and the rest of the MOD's technology leaders every success in executing the ambitious and necessary strategy.
