
DataDog has open-sourced a software supply chain package “firewall”.
Its release comes as open source package consumption explodes.
Python (PyPI) saw an 80% increase in consumption compared to last year, for example, at over 530 trillion package requests, while JavaScript (npm) downloads increased by 70%, with 4.5 trillion package requests.
With it, has come a growing rise in supply chain attacks, with over 512,847 malicious OSS packages identified by Sonatype since Nov. 2023.
DataDog firewall: Apache 2.0...
The DataDog “firewall”, created by the firm’s Ian Kretz, scans packages from pip and npm install and will block known malicious packages.
These are software elements either that the company itself has observed or which have made it into open source feeds from the OpenSSF and OSV.
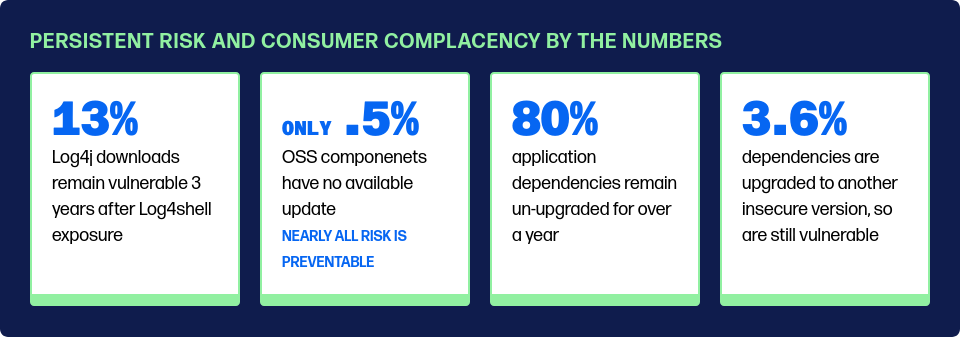
The welcome release comes amid rampant upstream “poisoning” of open source software packages. Just this month, Ultralytics, a Python package with close to 6.4 million downloads per month, appears to have been backdoored somewhere in the supply chain to run a cryptominer.
Whilst many organisations are on top of this, letting their developers use only pre-approved libraries of hardened base images and approved software packages, not everyone has a well-oiled machine of platform engineers or others on top of this and gaps can appear in controls.
Check out the S2C2F whilst at it...
(Check out the Secure Supply Chain Consumption Framework "S2C2F" for a really good starting point on OSS governance and ingestion process.)
As Kretz wrote: “Though prudent, expecting developers to thoroughly audit open source packages before installing and using them is not realistic and would negatively impact the developer experience… The result, however, is that open source software supply-chain security, at least with respect to the developer workstation, falls to the wayside.”
He added that the “scfw” firewall makes for a good “ad-hoc, install-time filter for open source packages” but also, “with a bit of very simple additional configuration, you can unlock the true potential of scfw as:
- An always-on protection for software developers
- A source of crucial telemetry data for system administrators about which packages are installed across their fleet of developer laptops
“You can accomplish the first goal by adding shell aliases to, for example, your .bashrc file so that pip and npm expand respectively to scfw run pip and scfw run npm. With a Datadog API key, you can achieve the second goal by making use of Supply-Chain Firewall’s native support for Datadog Log Management” its creator added in a blog post.
The command line tool is available under an Apache 2.0 licence here.
