
Big changes are coming to the Common Vulnerability Scoring System (CVSS) framework – which is used by cybersecurity professionals and vendors to communicate details about software vulnerabilities, with CVSS 4.0 now out for public preview in the first major update in seven years.
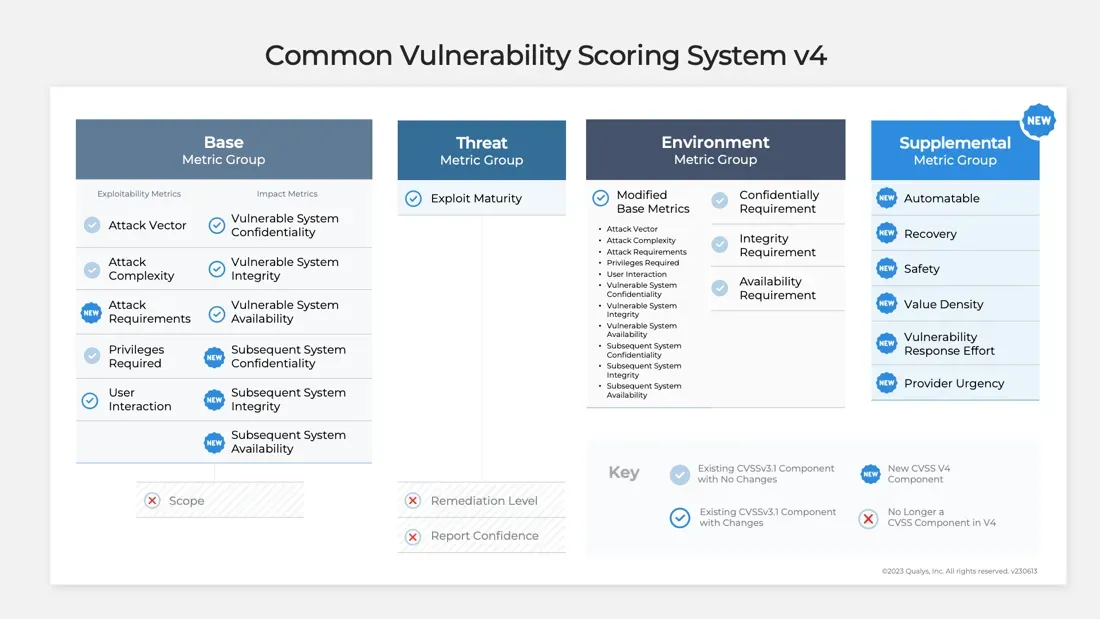
CVSS 4.0 makes a significant effort to improve how risk is calculated, amid concerns that CVSS Base Scores are being used by many organisations to (inadequately) assess risk. It also adds new guidance for Operational Technology (OT) and a wide range of supplemental metrics including “Vulnerability Response Effort” – ranked as “low, moderate, high.”
New metrics for Operational Technology exposure include whether the "consequences of the vulnerability meet definition of IEC 61508 consequence categories of "marginal," "critical," or "catastrophic."
Those inclusions come amid growing concern about OT cyber risk – with the US's CISA now regularly regularly releasing tranches of industrial controls systems cybersecurity advisories (27 to-date in June alone, some of which have public exploits available and wide potential impact.)
CVSS 4.0: More detail, more complications?
CVSS 4.0 adds a new four-fold nomenclature.
| CVSS-B | Base metrics |
| CVSS-BE | Base and Environmental metrics |
| CVSS-BT | Base and Threat metrics |
| CVSS-BTE | Base, Threat, Environmental metrics |
“If used properly, CVSS-BTE scores represent more comprehensive attributes than many highly respected 3rd-party security organizations consider when they generate their proprietary ‘Risk’ ratings,” said CVSS 4.0 authors Dave Dugal, of Juniper Networks, and Dale Rich, of Black & Veatch – adding that CVSS 3.1 lacked “enough real time threat and supplemental impact details” and was “only applicable to I.T. systems.”
CVSS 4.0 is open for public comment until July 31.
It is likely to be formalised and published in Q4, 2023.
Bharat Jogi, threat research director at Qualys, said CVSS 4.0 makes it "much easier for end users to evaluate the severity of a vulnerability. The inclusion of fine-grained details regarding user interaction required for vulnerability exploitation is also a welcome addition."
He noted however that "alongside the beneficial changes in version 4.0, there is also an increase in complexity. One longstanding issue with CVSS ratings has been the potential for inconsistencies in how individuals/vendors rate vulnerabilities. Moreover, with the introduction of more variables, the resulting scores can vary."
The CVSS 4.0 beta release comes as a number of new scoring systems have been released to try and better assess exploit risk and patch prioritisation, including EPSS: Exploit Prediction Scoring System – a "data-driven effort for estimating the likelihood that a software vulnerability will be exploited in the wild within 30 days" and SSVC: Stakeholder-Specific Vulnerability Categorization, a "decision-tree system for prioritizing actions during vulnerability management."
The CVSS 4.0 team described these as "welcome additions to the vulnerability scoring toolbox, providing innovative exploit prediction and decision support..."
You can see CVSS 4.0 here and comment on cvss at first dot org
