
It's a vulnerability that's literally as bad as it gets, with a CVSS score of 10.
Now an exploit for an Ivanti pre-auth deserialization RCE tracked as CVE-2024-29847 has been spun up and posted to GitHub (albeit in a slightly neutered form).
Ivanti patched the flaw on September 12, warning that a "deserialization of untrusted data exists in the agent portal of Ivanti Endpoint Manager (EPM)" which "allows a remote unauthenticated attacker to execute remote code on the target system."
EPM is a highly attractive target for attackers: Ivanti describes it as letting users get "one-click access to see, configure, and manage the IT policies and processes related to your users and groups" and automate IT tasks.
See also: Ivanti CEO promises product security overhaul after shocking analysis
The bug was discovered by Sina Kheirkhah, a vulnerability researcher whose X account @SinSinology has more than 11,000 followers.
He has also now published a "fully working unauthenticated exploit" and revealed attack path details.
He reported the Ivanti vulnerability via the Zero Day Initiative bug bounty programme in May. Ivanti pushed a hotfix on September 12.
"For the time being I’ve made the exploit a bit difficult to utilize since this is a high value target and this might help in slowing APT Kiddies down," Kheirkhah in a blog covering his research.
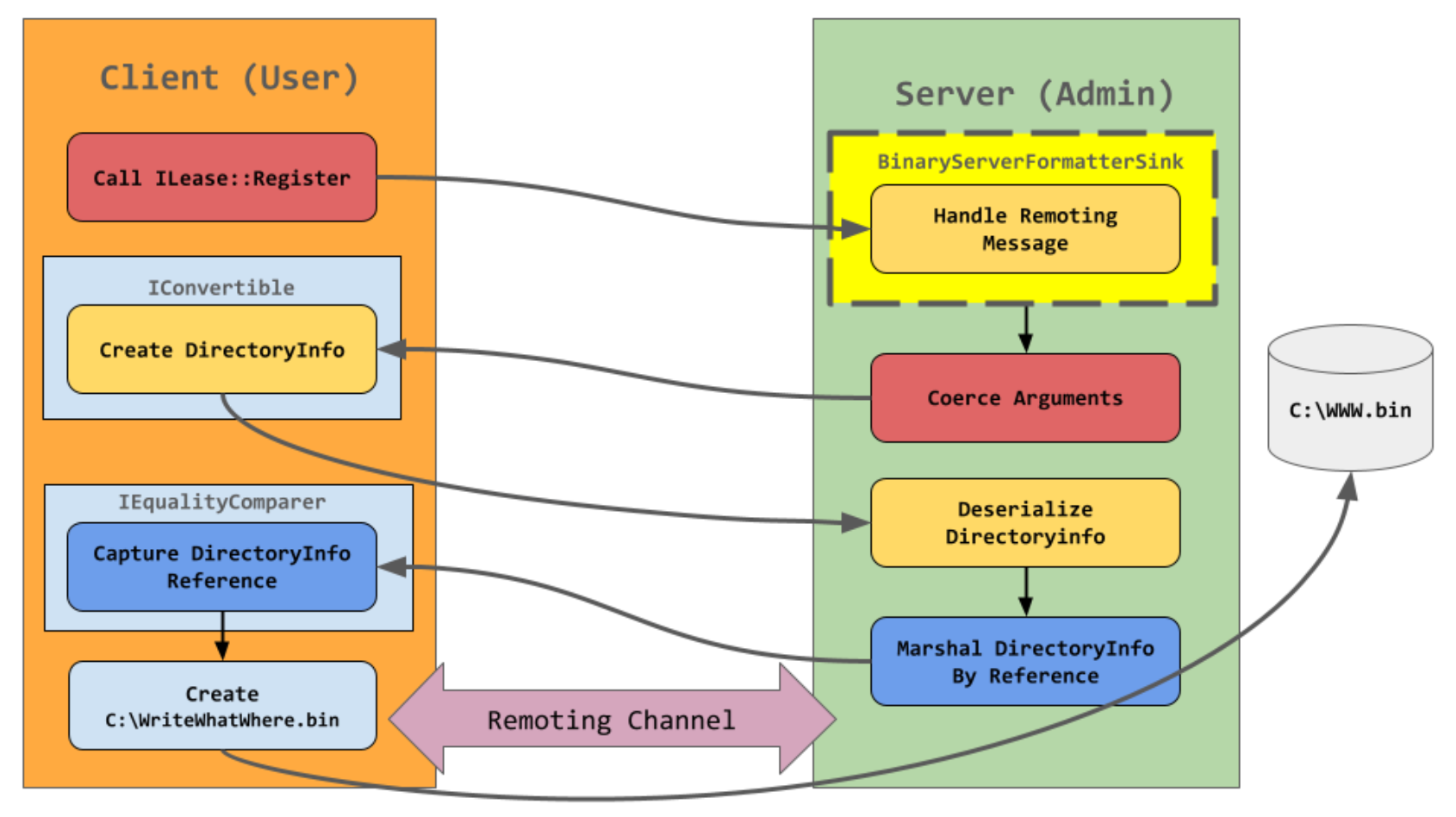
The vulnerability can be traced back to Ivanti's use of Microsoft .NET Remoting; a deprecated framework feature that enabled communication between applications or processes across different domains, allowing objects to interact remotely over a network or within the same machine.
In his 2019 research, Forshaw said "no one should be using .NET remoting in a modern context" – a sentiment that appears to be backed up by the latest research.
See also:
"The vulnerability here is the fact that Microsoft .NET Remoting is a dangerous and powerful technology," Kheirkhah wrote. "It’s use is extremely prohibited by Microsoft but to this day [is used] in a lot of critical infrastructure."
The specific flaw exists within the AgentPortal service. The issue results from the lack of proper validation of user-supplied data, which can result in deserialization of untrusted data. An attacker can leverage this vulnerability to execute code in the context of SYSTEM – Zero Day Initiative advisor.
He added: "Inside of the Agentportal.exe executable the LANDesk.AgentPortal.AgentPortal.OnStart method is invoked when ever the “Agent portal" service starts, this service is always running by default and it is possible to achieve unauthenticated remote code execution by exploiting this service."
Nothing to be scared about folks, just another CVSS 9.8 0day disclosed 0days ago that's gonna get code execution in 0 seconds (3 seconds to be more accurate), no limitation, no authentication, no shit, just straight up remote code execution#IvantiForLife pic.twitter.com/KrCTnFGgEB
— SinSinology (@SinSinology) May 2, 2024
The exploit involves bypassing a Low Type Filter which would normally protect against attack.
Kheirkhah concluded: "For Ivanti I used a different technique when exploiting the Low Type Filter, usually you might be taking the approach of remotely causing a side load of the FakeAssembly, but I’ve decided to abuse the Write What Where MarshalByRefObj Primitive and write a web shell to one of the EPM Public IIS Application Pool directories, this is because comapred to the FakeAssembly.
"Defender won’t catch this (which it will after this post, lol)."
