
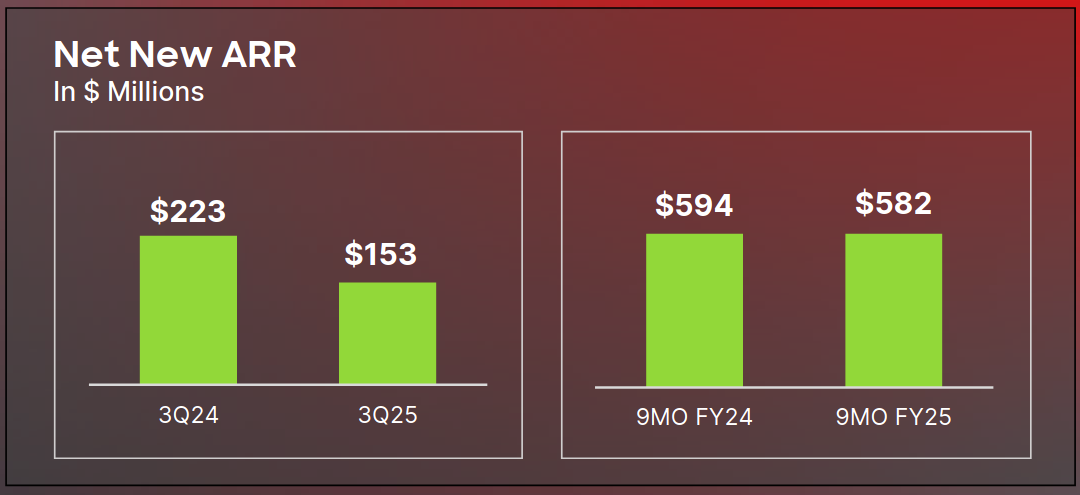
CrowdStrike said the incentives that it offered customers in the wake of a global July outage will cost it $30 million in Q4 – as net new recurring revenue for its third quarter slumped 30% versus the previous year.
Reporting fiscal Q3 2025 earnings, CEO George Kurtz put a positive gloss on the global incident, which crashed more than eight million computers, grounding flights, halting broadcasts, and stopping banking transactions.
He told analysts on an earnings call that “we turned crisis into a customer trust-building opportunity” – as CrowdStrike reported a net loss of $16 million for the quarter, versus a profit of $26 million last year.
The company continues to face legal action, including from Delta over the incident – which has also triggered a deep rethink by Microsoft over its controls around Windows kernel access and a wave of associated activities including the November 19 launch of the "Windows Resiliency Initiative".
Among new features promised by Microsoft after the incident is the pending "Quick Machine Recovery" due for insiders in early 2025.
The remote recovery feature, says Windows' Dave Weston, "will enable IT administrators to execute targeted fixes from Windows Update on PCs, even when machines are unable to boot, without needing physical access."
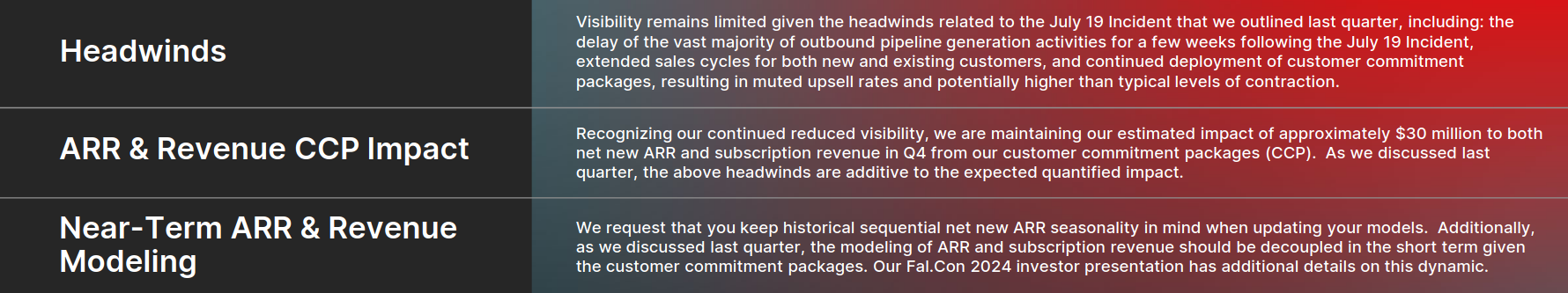
CrowdStrike CFO Burt Podbere told analysts that “as expected, the July 19 incident resulted in near-term headwinds to net new ARR… we are a little further from the sun. We're still kind of fighting through the incident."
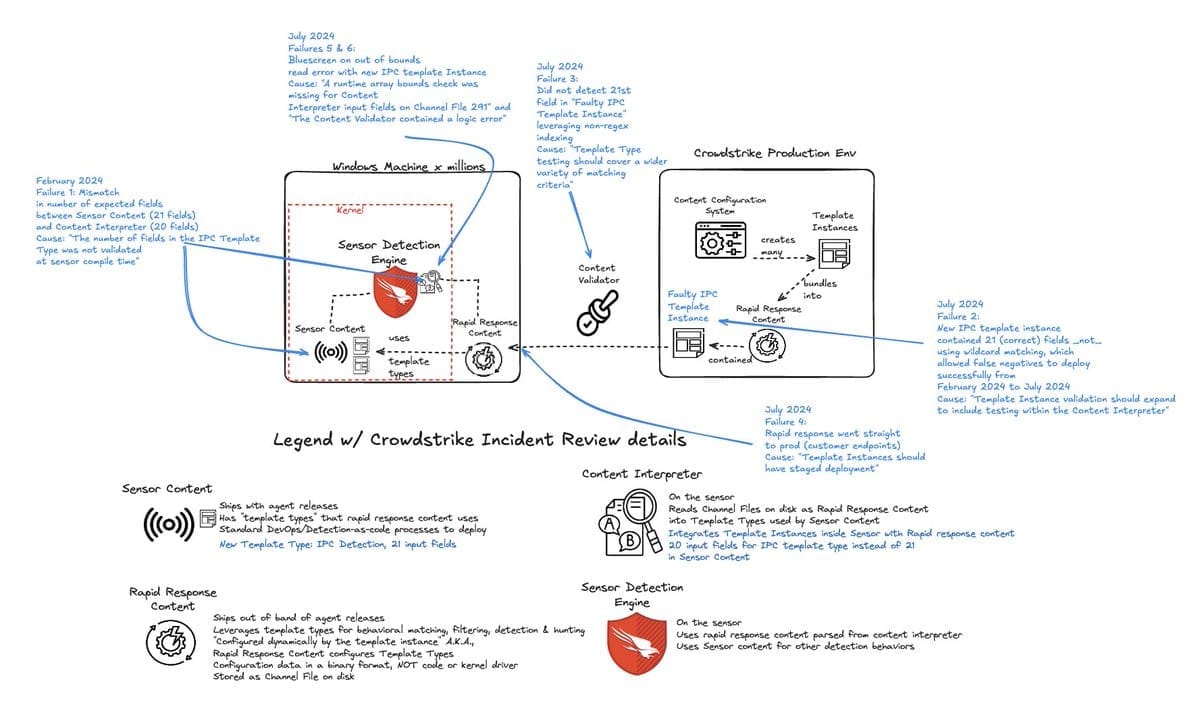
(A RCA was described by one architect as "a very long explanation for an out of bounds read, because of insufficient testing procedures and negligence in the kernel code." CrowdStrike has since made QA changes.)
“Extended sales cycles for new and existing customers and continued deployment of customer commitment packages including discounts and flexible payment terms have undermined growth," said Podbere.
“I think customers have additional scrutiny, additional layers of approvals, all that sort of thing. And I think we're going to continue to deploy customer commitment packages. This is going to result in muted upsell rates and potentially higher-than-typical levels of contraction…”
CrowdStrike executives emphasised on the call that CISOs however continue to "want to consolidate" the sprawling suites of security tools.
"This complexity normally breeds inconsistencies and seams in protection gaps within multiple technologies, so a broad platform approach is something that aids in stopping the breach. And they want to drive down their overall operational cost" as CEO George Kurtz put it on the earnings call.
(Interviews The Stack conducts suggests this is perfectly accurate, with Nomura's Global CTO for example telling us last month that the company has "more than 70 tools in our cybersecurity suite. Our aim is to reduce that by half in the next three years.")
CrowdStrike customers either looking to double-down or jump ship may also want to be mindful of a recent CISA Red Team report: The agency breached a critical national infrastructure (CNI) organisation, later saying that it "relied too heavily on host-based endpoint detection and response (EDR) solutions and did not implement sufficient network layer protections..." (It did not name the EDR.)
"The organization’s EDR solutions largely failed to protect the organization. EDR detected only a few of the red team’s payloads in the organization’s Windows and Linux environments. In the instance the EDR protected the organization from the initial phishing payload, it generated an alert that network defenders neither read nor responded to. The red team excelled in bypassing EDR solutions by avoiding the use of basic “known-bad” detections the tools would capture. The team also inflated its file sizes above the upload threshold of the organization’s EDR. In addition, the organization completely lacked any EDR solution in a legacy environment. As such, the red team’s persistence there went undetected throughout the assessment." CISA noted.
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
