Crowdstrike executive Adam Meyers has told a Congressional hearing that maintaining access to the Windows kernel is critical for securing systems - even though it played a central role in the mega-outage which brought down millions of computers around the world.
However, one important person was missing from the hearing: George Kurtz, CEO, who had been expected to face a grilling over the incident.
A key topic of the day was access to the kernel - a core part of the Windows operating system that manages critical tasks. Microsoft is both lauded and criticised for its open approach to the kernel, as opposed to Apple's walled garden approach, which strictly limits access.
On that fateful day back on July 19, the kernel became a heart of darkness for Kurtz and his team as a Microsoft Windows 10 blue screen of death outage grounded planes, closed down supermarket checkouts and hobbled vast numbers of devices across the world.
Earlier in September, Microsoft was widely rumoured to be planning to kick vendors out of the kernel at its Windows Endpoint Security Ecosystem Summit
This potentially ominous prediction did not come to pass, with Microsoft instead promising "more security capabilities to solution providers outside of kernel mode" and a "new platform capability".
Kernels of truth from the Crowdstrike outage
Speaking at the hearing yesterday, Rep. Eric Swalwell said: "One of our goals is to ensure that we stop relearning yesterday’s lessons so we can be more proactive in defending against the threats that we’ll face in the future.
"Toward that end, I was pleased that earlier this month Microsoft unveiled and convened the Windows Endpoint Security Ecosystem Summit, which brought together a diverse group of security firms to discuss issues ranging from safe deployment practices to providing additional security capabilities outside of kernel mode.
"Today, I hope to gain a better understanding of the trade-offs between kernel access and risks to the operating system and learn how we can better manage those risks."
Meyers then replied: "All operating systems have a kernel, which is the central component of the operating system. Often referred to as “ring zero,” the kernel is responsible for interfacing with all hardware connected to the system. CrowdStrike is one of many vendors that uses the Windows kernel architecture, an open system designed by Microsoft to support a wide variety of hardware and systems.
"The kernel plays a key role in ensuring system performance, providing visibility into everything happening on the operating system, and enforcing security measures like threat prevention and anti-tampering.
"Anti-tampering is a critical concern in cybersecurity, as attackers often try to disable security tools when they gain access to a system. Kernel visibility is essential for detecting when these actions occur. The kernel driver is a vital component of most security products, and while the extent to which each vendor uses kernel access may vary, securing the operating system without it would be extremely difficult."
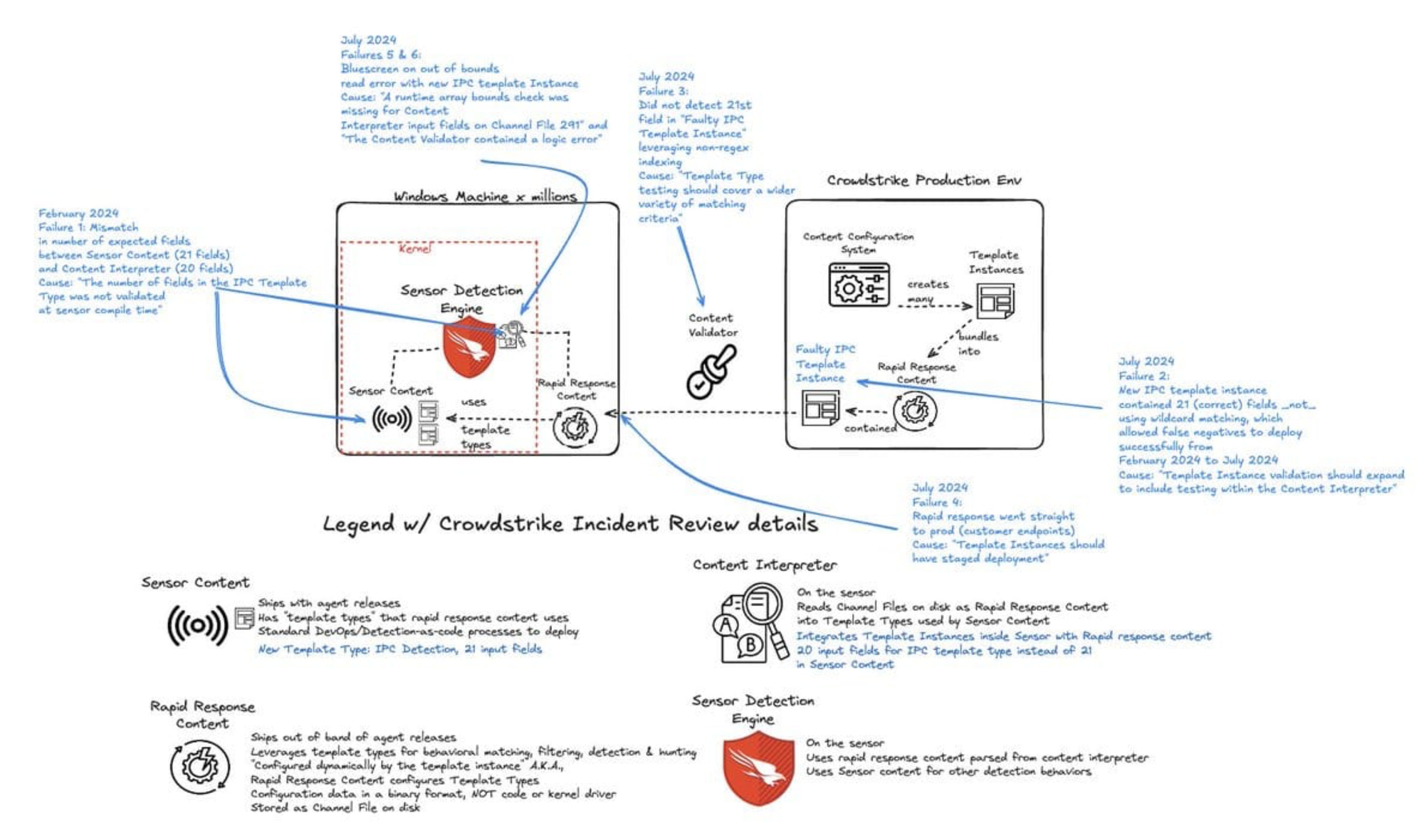
Meyers said Crowdstrike was "deeply sorry" for the incident, which was caused by a "perfect storm" of technical issues around one of the "10 to 12" content updates released every day.
"The content file triggered an issue within the kernel sensor, causing a problem when the sensor processed the configuration," he said. "It’s comparable to trying to move a chess piece to a spot without a square, which is essentially what happened inside the sensor.
"When the sensor attempted to apply the rule, it couldn’t complete the action, leading to the issue within the sensor."
Why did George Kurtz not appear at the hearing?
The hearing was notably gentler than the rough and tumble treatment given to leaders such as Mark Zuckerberg. However, one person was notable by their absence.
Simon Pardo, director of the UK IT support firm Computer Care, told The Stack: “While it's a step in the right direction that a senior CrowdStrike executive has apologised before Congress for July's catastrophic IT outage, the penitence really doesn’t fit the crime.
"The scale of disruption caused by CrowdStrike's faulty update was unprecedented. With about 8.5 million computers affected and an estimated cost running into billions of pounds, this incident deserves a place in the world record books.
"The fact that CEO George Kurtz isn't personally appearing before Congress is troubling. As the co-founder and leader of CrowdStrike, the buck stops with him. Could his absence suggest a lack of full accountability at the highest level of the company?
"This apology is just the start. We need a comprehensive, transparent explanation of what went wrong, and more importantly, the concrete steps CrowdStrike is taking to ensure this never happens again."
“This must include a complete overhaul of their testing and deployment procedures, enhanced failsafes, and a more considered rollout process for critical updates. At the same time, there needs to be a broader industry conversation about the risks associated with centralised security solutions. While these tools offer powerful protection, the CrowdStrike incident demonstrates how they can also become single points of failure with far-reaching consequences."








