
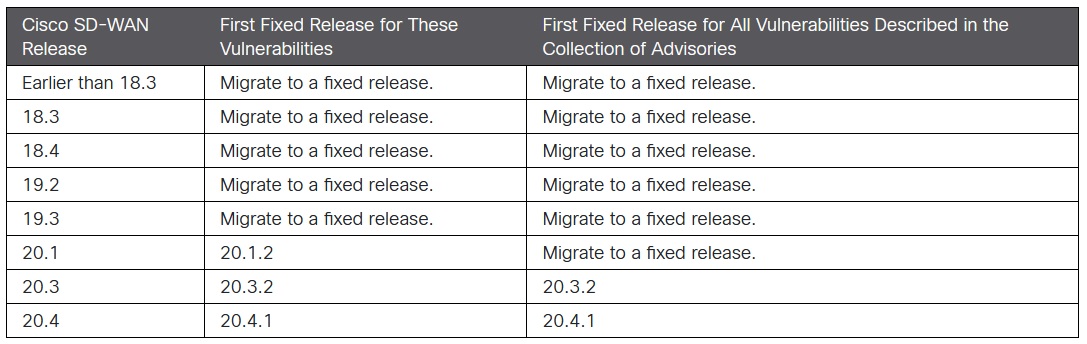
Cisco has released 32 security advisories, including four listed as critical -- two of which are for troubling vulnerabilities in its SD-WAN software that would an unauthenticated remote attacker root powers over a set of powerful tools often used to help connect data centres. They include command injection and buffer overflow vulnerabilities.
"Multiple vulnerabilities in Cisco SD-WAN products could allow an unauthenticated, remote attacker to execute attacks against an affected device" Cisco said. The first critical vulnerability is CVE-2021-1300 which Cisco says is "due to incorrect handling of IP traffic." An unauthenticated remote attacker could exploit it by "sending crafted IP traffic through an affected device, which may cause a buffer overflow."
A successful exploit could then allow the attacker to execute arbitrary code on the underlying OS with root privileges.
Products affected include:
- IOS XE SD-WAN Software
- SD-WAN vBond Orchestrator Software
- SD-WAN vEdge Cloud Routers
- SD-WAN vEdge Routers
- SD-WAN vManage Software
- SD-WAN vSmart Controller Software
(The vulnerabilities were found during internal testing and Cisco says it's not aware of them being exploited in the wild. But with threat actors increasingly swift at reverse-engineering patches to work out how to exploit the bug being fixed, rapid patching is recommended).
Critical Cisco SD-WAN vulnerabilities
The second of the critical SD-WAN vulns (tracked as CVE-2021-1299) requires an attacker to be authenticated, but once gaining authentication they could abuse it to execute arbitrary commands as root. (Given the apparent ease with which credentials can be guessed, brute-forced, or acquired on the dark web, not a high initial hurdle).
It only affects the central SD-WAN managing vManage console.
Of the two other critical vulns, one (CVE-2021-1264: CVSS 9.6) affects the Command Runner tool of Cisco DNA Center (a network controller and management dashboard). This has a list of approved commands that can be executed on a managed device, but the advisory notes an attacker can bypass this list on the managed device or configuration CLI.
The fourth (set of) critical vulns are in a license managing tool, Cisco Smart Software Manager Satellite releases 5.1.0 and earlier. They again could allow an unauthenticated, remote attacker to execute arbitrary commands on the underlying OS. They have a base CVSS score of 9.6 and are being tracked as CVE-2021-1138, CVE-2021-1140, CVE-2021-1142.
