
F5 today (March 10) disclosed a series of critical vulnerabilities in its BIG-IP and BIG-IQ services, including pre-authentication remote code execution (pre-auth RCE) bugs that could lead to "complete system compromise".
Among the worst, a CVSS 9.8 bug (CVE-2021-22986) in its iControl REST API for BIG-IP: an externally accessible tool designed to provide "granular control" over BIG-IP configuration and management across data centres.
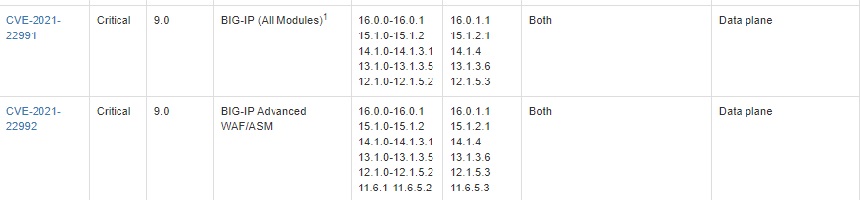
"Because of the severity of these vulnerabilities, F5 recommends that all customers install fixed software as soon as possible. All seven vulnerabilities are fixed in the following BIG-IP versions: 16.0.1.1, 15.1.2.1, 14.1.4, 13.1.3.6, 12.1.5.3, and 11.6.5.3. CVE-2021-22986 also affects BIG-IQ, and this is fixed in 8.0.0, 7.1.0.3, and 7.0.0.2," F5 said.
The bug was one of 21 CVEs revealed today by F5.
See also: Check out these 6 free open source security tools you should know about
The patches land just seven months after F5 pushed out an emergency fix for the CVSS 10-rated CVE-2020-5902; a devastating vulnerability that saw thousands exposed and exploits proliferate within days of its disclosure. That CVE, reported in July 2020, gives root as administrator, letting anyone with network access to the Traffic Management User Interface through the BIG-IP management port execute arbitrary system commands.
BIG-IP is product suite widely used by blue chip financial services and tech firms, government agencies and more. It acts as a gateway to data centres, handling network load balancing, SSL offloading, and more.
The company claims 48 of the Fortune 50 rely on F5.
Four of today's new bugs are critical, including CVE-2021-22987, a CVSS 9.9 rated bug in F5's Traffic Management User Interface (TMUI) and CVE2021-22992, for which a malicious HTTP response to an Advanced WAF/BIG-IP ASM virtual server with Login Page configured in its policy can alllow RCE "leading to complete system compromise."

More from F5 here.
