
One of the most feared ransomware operations, LockBit, appeared to be mortally wounded today after international agencies took over its key websites and posted decryption tools for the gang’s victims.
The ransomware as a service group is credited with some of the most high profile ransomware attacks in recent years, including a breach that brought the UK’s Royal Mail to a virtual standstill last year and an attack on the US branch of the world's largest bank, China's ICBC.
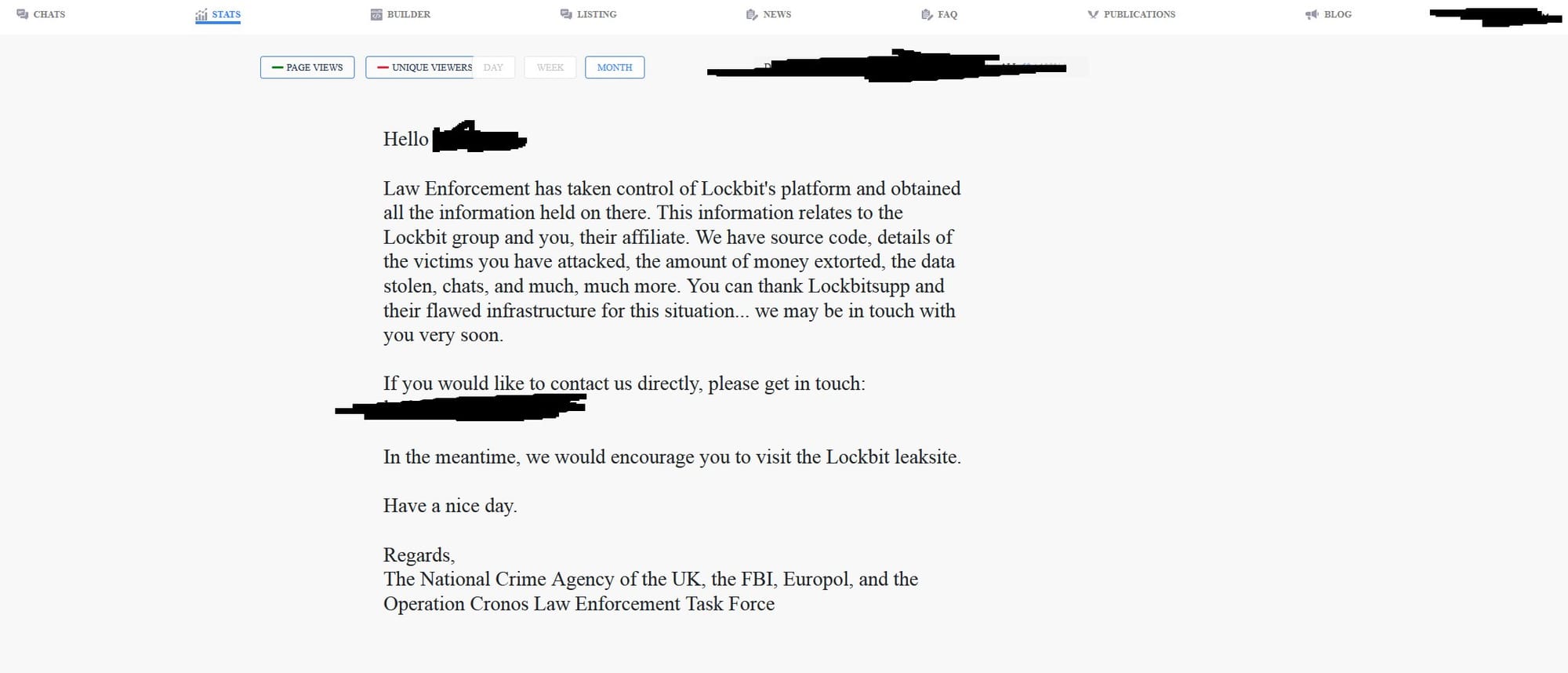
This morning LockBit’s affiliate website was carrying a message saying, “Law Enforcement has taken control of LockBit’s platform and obtained all the information held on there.” It said this includes source code, details of victims and ransoms paid, data, chats and “much, much more”.
LockBit affiliates suggested that they had fallen victim to exploitation by law enforcement of an unpatched PHP vulnerability, CVE-2023-3824.
A statement by Europol said an international taskforce, “Operation Cronos” had disrupted the group at every level, “severely damaging their capability and credibility.”
The investigation was led by the UK’s National Crime Agency, which said it had “taken control of the technical infrastructure that allows all elements of the LockBit service to operate, as well as their leak site on the dark web.”
This involved the takedown of 34 servers across the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States and the United Kingdom, Europol said. Authorities have also seized over 200 Lockbit-linked cryptocurrency accounts.
Moreover, two “LockBit actors have been arrested in Poland and Ukraine”, with three international arrest warrants and five indictments issued by French and US authorities.
The NCA said two defendants were in custody and will face trial in the US, and the US had unsealed indictments against two Russians for conspiring to commit LockBit attacks.
Japanese Police, the National Crime Agency and the Federal Bureau of Investigation have developed “decryption tools designed to recover files encrypted by the LockBit Ransomware”, which are available on the No More Ransom Portal.
The NCA said it had obtained over 1000 decryption keys and would be contacting UK-based victims in the coming weeks.
In its statement, which went live shortly after 11.30 GMT, the NCA said that over the last 12 hours the infrastructure behind LockBit’s StealBit data exfiltration tool “has been seized by members of the Op Cronos taskforce, and 28 servers belonging to LockBit affiliates have also been taken down.”
The UK organization said it had taken control of “LockBit’s primary administration environment”, which enabled affiliates to build and carry out attacks, and its public-facing leak site on the dark web, “on which they previously hosted, and threatened to publish, data stolen from victims”.
It said the latter would be used to post information exposing Lockbit’s capability and operations over the course of the week. The takedown notice on the affiliate site pointed to Lockbit’s “flawed infrastructure” and warned affiliates “we may be in touch with you very soon”.
The NCA also said it has LockBit’s source code, “and a vast amount of intelligence from their systems about their activities and those who have worked with them and used their services to harm organisations throughout the world.”
This includes data for which ransoms had already been paid, it said, showing the group had not stuck to its own commitments to victims.
As former NCSC head Ciaran Martin posted on X, “Guess we’re about to find out if #lockbit have good backups and an effective business continuity & recovery plan”.
The NCA said, LockBit may well seek to rebuild its operations. “However, we know who they are, and how they operate. We are tenacious and we will not stop in our efforts to target this group and anyone associated with them.”
CISA last year described LockBit as the “most deployed ransomware variant across the world.” It noted that it had an affiliate friendly model, allowing clients to receive ransomware before taking its cut, and offering a “simplified, point and click interface for its ransomware.” It also engaged in “publicity generating stunts”.
Tim West, Director, Threat Intelligence & Outreach at WithSecure, said that LockBit had been responsible for a fifth of breach site posts in 2023 and a quarter so far in 2024. “Of all the ransomware brands to disrupt, LockBit is almost certainly the preferred choice.”
But, West pointed out, “LockBit have proven themselves in the past to be a resilient ransomware variant, surviving major leaks and rebrands, [and] we do not yet know the impact that these takedowns will have on operations.”
He noted that LockBit was claiming that only servers running PHP elements were impacted, data is safe and backup servers were unaffected which, “if true, will probably mean LockBit (as well resourced actors) can recover fairly swiftly.”
But, he continued, “The collective of law enforcement agencies will certainly have carefully weighed short term and long term impact opportunity to ensure maximum disruption and impose maximum cost on LockBit.”
Stephen Robinson, Senior Threat Intelligence Analyst at WithSecure, added, the LockBit takedown had echoes of the recent ALPHV takedown. That had led to ALPHV announcing that “in response they would begin targeting CNI, something they previously claimed was off limits for their affiliates. ALPHV has since attacked several CNI entities.”
The disruption of LockBit could follow the same pattern, he said, though initial reports suggested “LEA were able to penetrate much deeper into LockBit's internals”.
But, he added, “Even if that is the case, it may simply lead to the group fracturing and cross-pollinating their expertise and tools across the cybercrime landscape, as happened when Conti disbanded."
