Twitter has been rocked by a series of hard-hitting allegations from its former cybersecurity lead – a distinguished ex-hacker brought in to help toughen up the social media company’s defences after a 2020 security breach that saw the accounts of Apple, Barack Obama, Bill Gates and Elon Musk hacked, among others.
Peiter “Mudge” Zatko was fired earlier this year by the company for alleged “poor leadership”. Twitter’s CISO – a separate role – rapidly followed him out of the door, it remains unclear whether voluntarily or not.
Among Zatko’s many allegations, broken by CNN on Tuesday, were claims that the company’s executive team instructed Zatko to “provide an oral report of his initial findings on the company’s security condition to the board rather than a detailed written account, ordered Zatko to knowingly present cherry-picked and misrepresented data to create the false perception of progress on urgent cybersecurity issues, and went behind Zatko’s back to have a third-party consulting firm’s report scrubbed” to downplay vulnerabilities.
https://twitter.com/mainframed767/status/1562099439510007809 CISOs, many argue, should report outside IT.
Whilst Twitter disputes the allegations, the furore sadly will not sound unfamiliar to many security professionals, who regularly live with being the bearer of bad news and the fear that executives may be minded to “shoot the messenger”, particularly when such tidings reflect badly on broader leadership.
How can boards ensure CISOs are not being muted?
How can organisations best tackle this risk? The Stack spoke several senior security leaders from a range of blue chip multinationals for their views – many of whom said they had experience of (and experience of resisting) requests to provide oral rather than written reports on cybersecurity posture at their employers.
One CISO, working for a multi-billion revenue software company on condition of anonymity, told us a little wearily in a series of Signal messages: “It can be difficult for CISOs to be completely transparent with the board of directors because of the operating model that exists in most companies. CISOs and CSOs work for executive management and in the end are beholden to CEOs for everything from compensation to performance reviews.”
They added: “Typically in the internal audit space at most public companies, the lead audit executive reports to a Director on the Audit Committee, resulting in safeguards for transparency. Executive leadership has a limited ability to stifle the views of the audit leader. CISOs and CSOs may need to be positioned similarly to ensure independence with not even an appearance of perception of undue influence by the management team.”
(It's a view shared by Deloitte, which notes that "overseeing a successful cybersecurity programme requires frequent and proactive engagement from the board of directors and audit committee" -- something of a problem in itself when so few board members are, as one participant in a Cyber Risk Director Network has put it, "illiterate about cybersecurity and the company’s reliance on information technology. But enterprise access to the internet is fundamental to delivering value, and all those transactions that rely on access to the internet are inherently unsafe. That’s not true of any other aspect of risk that boards deal with...")
Follow The Stack on LinkedIn
At many larger enterprises oversight of cybersecurity already usually defaults to the audit committee, but these are not typically put together with cybersecurity expertise in mind and many feel that there needs to be ongoing "robust discussion at the governance committee about the alternatives" -- whether that's a dedicated technology committee or another approach. (We'd welcome further views on optimal management structures.)
More broadly meanwhile, as Paul Gribbon, from managed cybersecurity services provider Reliance acsn noted to The Stack by email, the “perception that the CISO is a merely a very senior technician still persists… Even where the CISO reports to an organisation’s Risk function [rather than the CIO], which is better in our view, the role is still one level down from the Board, meaning that advice is filtered through the CRO.
"Wherever the CISO reports, another key challenge they face is to articulate information and cyber risk in business terms. Many aspiring CISOs have great technical experience but need to develop both their information and business risk language (especially avoiding the trap of talking technology and products to top management), and their stakeholder management skills. Given that many strategic decisions require influencing outside the confines of the Board Room, this is often an overlooked aspect of the CISO role.”
How to report cybersecurity issues to the BOD?
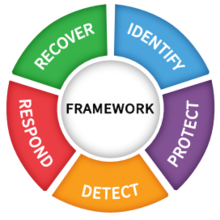
A CIO at a major manufacturing multinational (full on-the-record interview coming soon) meanwhile earlier told us that they had cut through to the Board of Directors on the need for dramatically improved security spending and more organisational accountability by using a heavily reworked version of the NIST Framework designed for clarity across just three metrics.
The NIST Framework is a voluntary model for organisations seeking to identify, assess, address, and manage cybersecurity risk and is widely used as the foundation of enterprise cyber maturity assessment programmes. (It has recently had a request for information out as it plans an update to the framework. Among the responses is a call for NIST to consider building a "navigable NIST Cybersecurity Framework Ecosystem that could also link and show the relationship between the Cybersecurity Framework, the Risk Management Framework, and the Privacy Framework, as well as mappings, links, informative references, etc.”)
To Axonius’ Dan Trauner, Senior Director for Security, meanwhile, the problem "isn’t just that CISOs aren’t reporting into the broader C-suite. It’s also that when companies hire new security leadership, they sometimes have unrealistic expectations about what the security team’s role should encompass. Fixing serious security issues, and even more so, implementing basic security hygiene, requires business-wide buy-in including tangible action by other teams. Perhaps the most surprising thing about the Twitter whistleblower complaint is that it isn’t actually that surprising at all. The reality is that there are a whole lot more companies out there with an even worse security posture, and that’s because the fundamentals are so hard to do – especially at scale.”









