A critical bug in a Cisco tool that automates data center network provisioning lets any unauthenticated, remote attacker write arbitrary files onto an affected system, the company has warned.
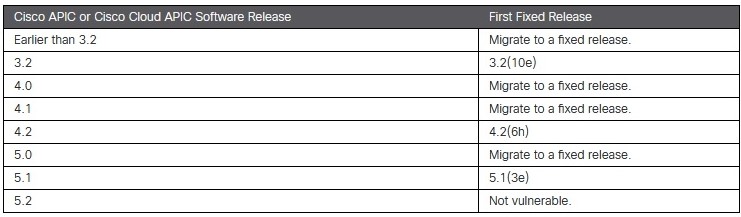
Allocated CVE-2021-1577 with a CVSS of 9.1, the bug affects Cisco Application Policy Infrastructure Controller (APIC) and Cisco Cloud Application Policy Infrastructure Controller (Cloud APIC) up to versions 5.1.
Over 14,000 CVEs have been allocated already in 2021, putting it on track to be a record year for reported software vulnerabilities, NIST data shows -- with 2010 CVEs already reported in August alone.
Cisco APIC is the main architectural component of Cisco ACI -- itself a software-defined networking offering that lets users set up a software-defined data center, with infrastructure implemented as code.
Mercifully, the vulnerability was found during internal security testing by the Cisco Advanced Security Initiatives Group (ASIG) and there is no indication that it has been exploited in the wild yet, the company said August 25.
"This vulnerability is due to improper access control. An attacker could exploit this vulnerability by using a specific API endpoint to upload a file to an affected device. A successful exploit could allow the attacker to read or write arbitrary files on an affected device" it added in an advisory.
With attackers reverse-engineering patches at ever-greater pace ("within days of their public disclosure" US authorities recently warned of Chinese APTs) users should check if they are affected and if so, patch promptly.








