The United States’s cybersecurity agency CISA hacked Critical National Infrastructure (CNI) through a web shell “left from a third party’s previous security assessment” in a recent Red Team engagement – the equivalent to breaking into a house by the same window as a previous burglar.
The shell, or bit of malicious code to give remote access, was left on an "old and unpatched service" with an exposed endpoint that had also previously been used as a beach head into the unnamed organisation.
CISA periodically conducts such offensive security campaigns against US organisations, when invited, with the aim of helping them improve their security posture. It then shares details in reports designed to encourage readers to apply lessons from their work to their own environments.
Worryingly, if perhaps familiarly for some security professionals, CISA reported of this engagement that “leadership minimized the business risk of known attack vectors for the organization” (it did not name the entity.)
CISA added: “Leadership deprioritized the treatment of a vulnerability their own cybersecurity team identified, and in their risk-based decision-making, miscalculated the potential impact and likelihood of its exploitation.” (Do we suspect a furious cybersecurity team found a way to get CISA involved, to teach leadership about the gravity of the issue?)
CISA Red Team: She sells web shells on the...
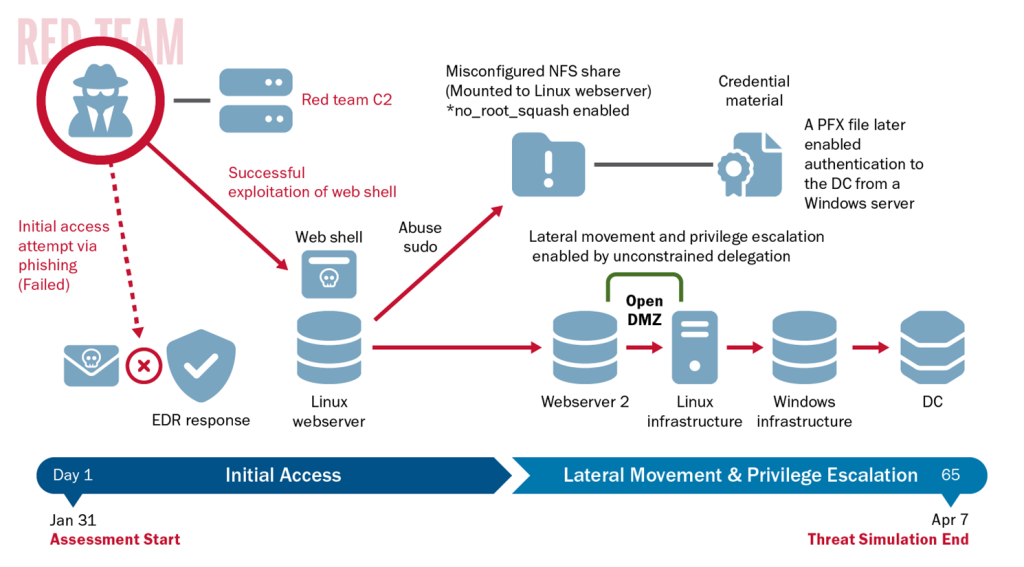
CISA first tried phishing. This failed. It then used commonly available tools to scan for publicly accessible devices or services and “identified an old and unpatched service with a known… vulnerability and leveraged a public proof of concept to deploy a web shell. The associated product had an exposed endpoint—one that system administrators should typically block from the public internet—that allowed the red team to discover a preexisting web shell on the organization’s Linux web server” CISA wrote.
“The preexisting web shell allowed the red team to run arbitrary commands on the server as a user (WEBUSER1). Using the web shell, the red team identified an open internal proxy server to send outbound communications to the internet via… HTTPS. The red team then downloaded and executed a Sliver payload that utilized this proxy to establish… C2 over this host, calling back to their infrastructure.”
“Network defenders had previously identified and reported the vulnerability but did not remediate it” CISA found. The organisations defenders meanwhile were “unaware of the web shell and believed it was likely leftover from prior VDP (vulnerability disclosure program) activity.”
Cue much finger-pointing and amusement on social media this week.
CISA’s detailed breakdown of the campaign contains multiple critical lessons. Some other key takeaways, digested: EDR was largely useless.
EDR spotted an initial phishing campaign but network defenders simply ignored alerts and anyhow, the Red Team bypassed EDR by “avoiding the use of basic ‘known-bad’ detections” and “inflated its file sizes above the upload threshold of the organization’s EDR” among other tricks.
The organisation also “did not implement sufficient network layer protections” and was running outdated versions of Windows Server 2012.
Some interesting encounters between the Red Team and network defenders occurred in the organisation’s Linux environment CISA noted.
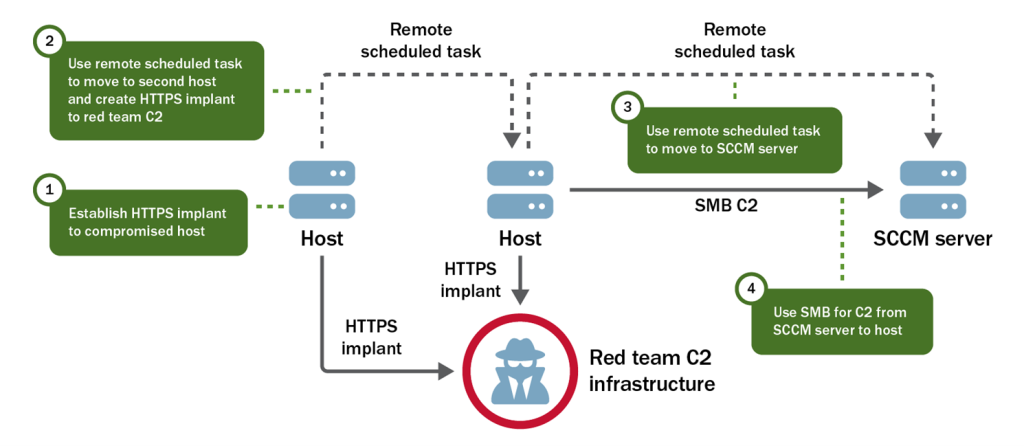
“Network defenders’ threat hunting activities identified some of the team’s presence in their Linux environment” it wrote of the campaign.
“To evade defenses, the red team reordered the process identifier (PID) of its executable processes to appear closer to the kernel and minimize the team’s likelihood of detection. The team also modified its processes by changing their names in memory and at execution. In addition, they used Python scripts run in memory to avoid on-disk detection…” Sneaky.
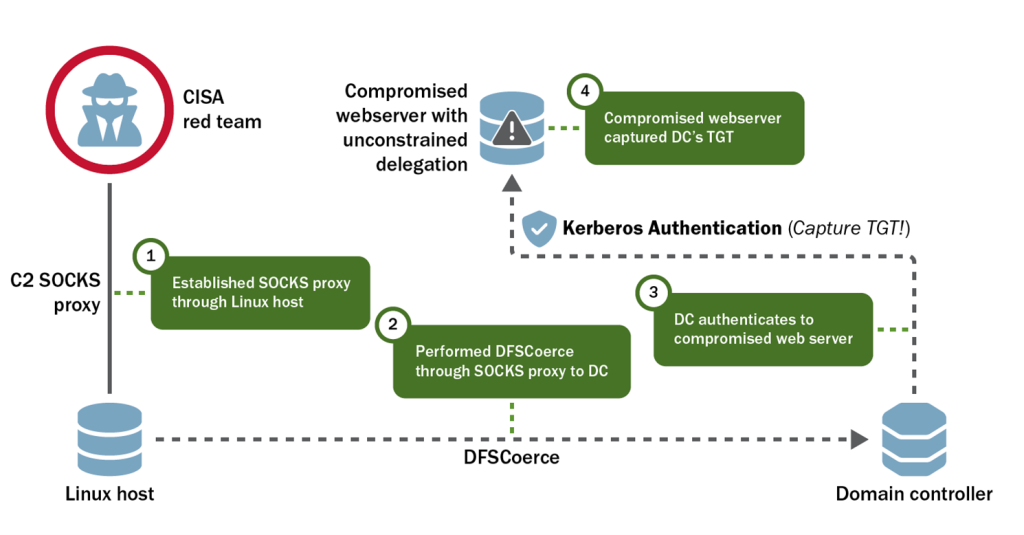
The CISA Red Team also “gained root access to an SBS-adjacent [sensitive business systems] infrastructure management server that ran Ansible Tower [that] provided easy access to multiple SBSs. The team discovered a root SSH private key on the host, which allowed the team to move to six SBSs across six different sensitive IP ranges [and which was] used to log into multiple hosts at times and for durations outside of pre-established baselines. In a real compromise, the organization would have had to shut down the server, significantly impacting business operations” it noted.
Read the full piece and useful advisory for defenders here.
For those like the business leaders of this CNI organisation, who minimised risk of known attack vectors, it may be worth revisiting the fact that a ransomware attack on Change Healthcare in February will cost its parent company up to $2.45 billion, according to CFO John F. Rex.
The incident saw attackers compromise a Citrix appliance (that entered the company’s network via an earlier acquisition) that did not have MFA set up, move laterally through the provider’s network, find and cripple its domain-joined backups, and then detonate ransomware nine days later.
"Direct response" cost alone hit $776 million.








