
A Chinese hacking group called Volt Typhoon has allegedly exploited a zero-day vulnerability in servers used by ISPs and MSPs to steal credentials and break into customers’ networks downstream.
The Black Lotus Labs team at Lumen Technologies discovered an actively exploited zero-day vulnerability in Versa Director servers, which is being tracked as CVE-2024-39717 and was publicly announced on August 2, 2024.
CISA (the Cybersecurity and Infrastructure Security Agency) added the zero-day to its must-patch list over the weekend, warning that "these types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise."
You can find IOCs for the vuln here on the Black Lotus Labs Github page. The researchers also shared threat intelligence with US government agencies to warn them of "emerging risks that could impact our nation's strategic assets."
The flaw impacts the Versa Director GUI, which gives users the option of customising the look and feel of their user interface when they are logged in with either "Provider-Data-Center-Admin" or "Provider-Data-Center-System-Admin" privileges.
The "Change Favicon" option can be "misused to upload a malicious file ending with .png extension to masquerade as image file," NIST warned.
The vulnerability was found in Versa's software-defined wide area network (SD-WAN) applications and impacts Versa Director versions before 22.1.4.
"In essence, Versa Director servers are the centralized management for client SD-WAN network infrastructure and are predominately intended for ISP and MSP operations," Black Lotus Labs wrote. "This makes Versa Director a lucrative target for advanced persistent threat (APT) actors who would want to view or control network infrastructure at scale, or pivot into additional (or downstream) networks of interest."
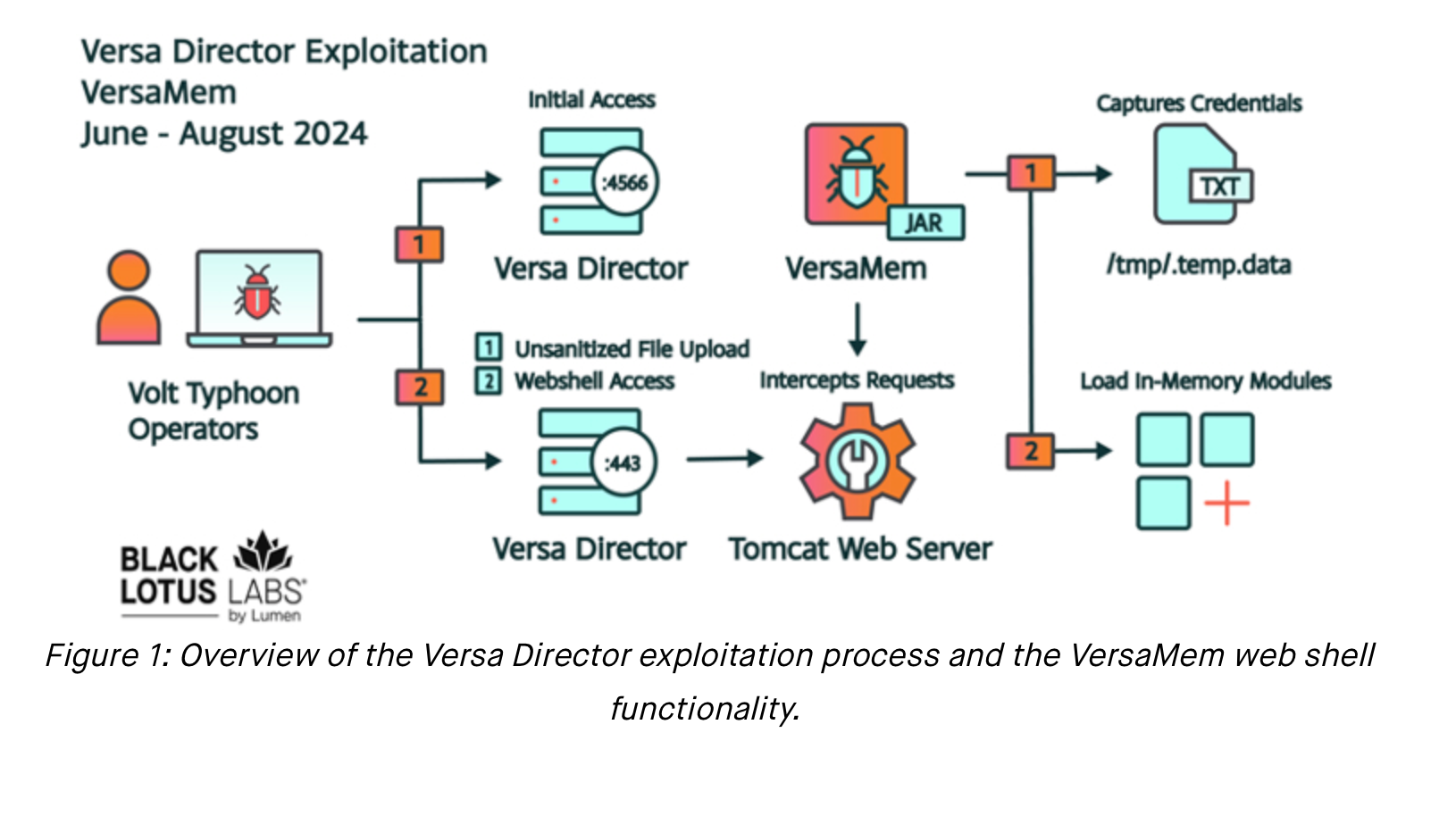
Researchers identified a "unique, custom-tailored web shell tied to this vulnerability" and dubbed it “VersaMem.” They claimed VersaMem's primary purpose is to "enable access into downstream customers' networks as an authenticated user".
It is a "sophisticated" modular JAR web shell that also lets threat actors load Java code to run in memory. The web shell was uploaded to VirusTotal on June 7, 2024, with the filename “VersaTest.png,” and currently has zero anti-virus (AV) detections.
Small-office/ home-office (SOHO) devices belonging to four victims in the US and one in an undisclosed nation were allegedly hit by the zero day. The businesses affected were ISPs, MSPs and IT companies, who were targeted from June 12 2024.
Threat actors gained initial administrative access through an exposed Versa management port intended for high-availability (HA) pairing of Director nodes, allowing them to deploy the VersaMem web shell.
In a security bulletin, Versa Labs wrote: "Impacted customers failed to implement system hardening and firewall guidelines... leaving a management port exposed on the internet that provided the threat actors with initial access.
"Versa has released a patch for the vulnerability, and we are actively working with all customers to ensure the patch and system hardening guidelines are applied."
It added: "This vulnerability has been exploited in at least one known instance by an Advanced Persistent Threat actor.
"Although the vulnerability is difficult to exploit, it’s rated “High” and affects all Versa SD-WAN customers using Versa Director, that have not implemented the system hardening and firewall guidelines."
Black Lotus advised Versa users to implement its recommended hardening techniques and firewall rules, block external/northbound access to ports 4566 and 4570, "ensuring these ports are only open between the active and standby Versa Director nodes for HA-pairing traffic".
Organisations can also search for interactions with port 4566 on Versa Director servers from non-Versa node IPs such as SOHO devices, search the Versa webroot directory (recursively) for files ending with a “.png” extension that are not valid PNG files and check for newly created user accounts or other abnormal files.
It advised Versa Director users to audit user accounts, review system/application/user logs, rotate credentials, analyse downstream customer accounts and "triage lateral movement attempts if any indications of compromise are identified, or the management ports 4566 or 4570 were exposed for any period of time."