
The US cybersecurity establishment has released new details on specific TTPs used in China telco attacks used to gain access to, and exfiltrate data from, network operators and telecoms providers worldwide.
The joint advisory by the NSA, CISA and FBI outlines specific ways PRC-based groups have infiltrated telecoms providers and other large organisations, complete with lists of the most common CVEs exploited, and details of the specific techniques and commands used.
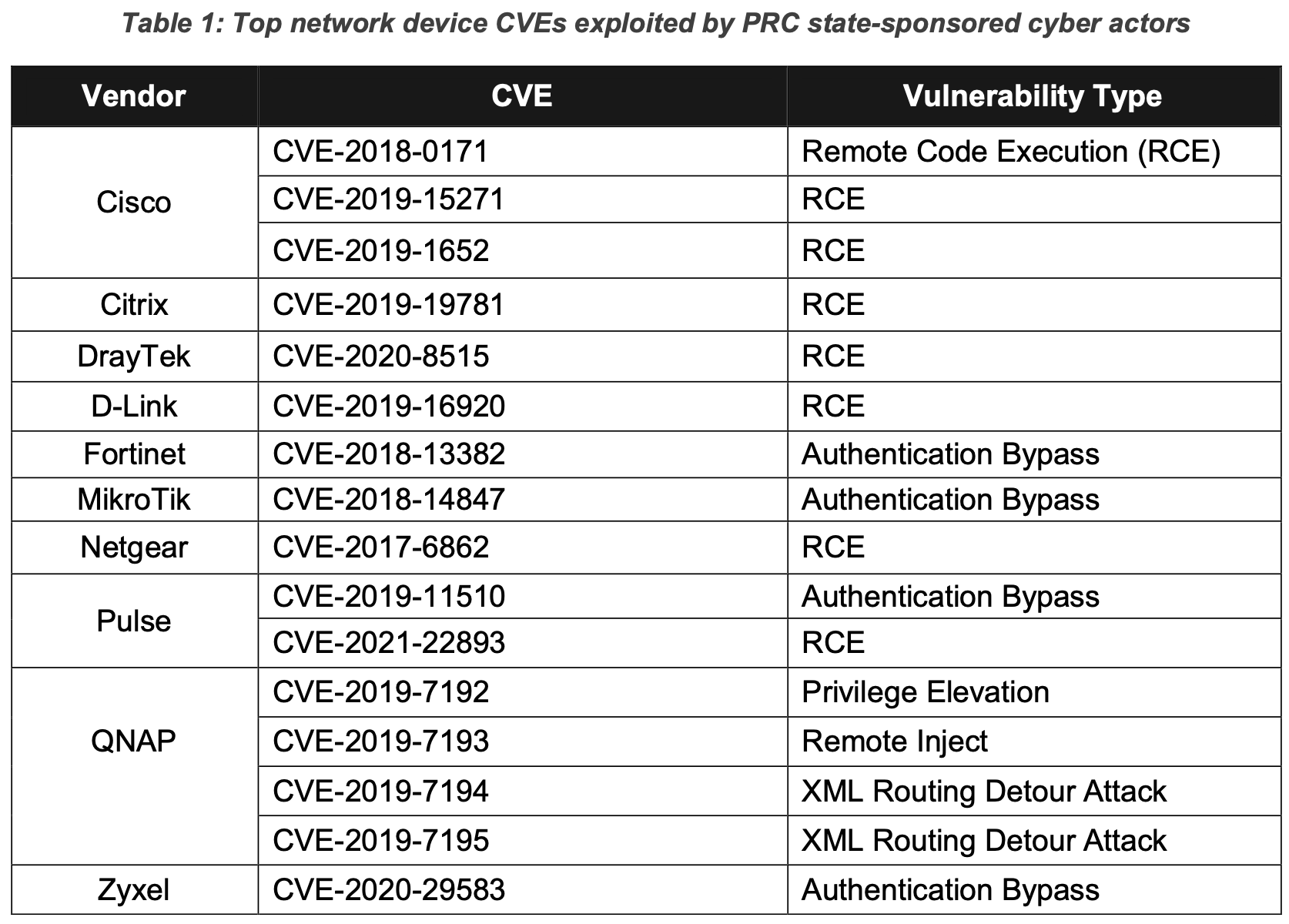
“The advisory highlights how People’s Republic of China (PRC) actors have targeted and compromised major telecommunications companies and network service providers primarily by exploiting publicly known vulnerabilities. Networks affected have ranged from small office/home office (SOHO) routers to medium and large enterprise networks,” said an NSA press release.
See also: China’s security researchers told to report all new bugs to gov’t
Open-source tools such as RouterSploit and RouterScan are commonly used to scan IP addresses for vulnerable SOHO network devices from vendors including Cisco, Fortinet and MikroTik. After this, attackers identify key users and systems, then gain access to a RADIUS server, then databases.
“Having gained credentials from the RADIUS server, PRC state-sponsored cyber actors used those credentials with custom automated scripts to authenticate to a router via Secure Shell (SSH), execute router commands, and save the output [T1119]. These scripts targeted Cisco and Juniper routers and saved the output of the executed commands, including the current configuration of each router,” said the CISA advisory.
“After successfully capturing the command output, these configurations were exfiltrated off network to the actor’s infrastructure [TA0010]. The cyber actors likely used additional scripting to further automate the exploitation of medium to large victim networks, where routers and switches are numerous, to gather massive numbers of router configurations that would be necessary to successfully manipulate traffic within the network.”
The advisory goes on to list specific details of commands and tools used in Chinal telco attacks on a Juniper router – noting other manufacturers are likely to have similar commands. These allowed the actors to configure port mirroring to copy traffic, then forward that traffic out of the target’s network.
See also: Kaspersky says Chinese APT demonstrating “seemingly impossible network behaviors”
CISA warned in the advisory that PRC actors are highly adaptable: “These cyber actors are also consistently evolving and adapting tactics to bypass defenses. NSA, CISA, and the FBI have observed state-sponsored cyber actors monitoring network defenders’ accounts and actions, and then modifying their ongoing campaign as needed to remain undetected.
“Cyber actors have modified their infrastructure and toolsets immediately following the release of information related to their ongoing campaigns.”
The advisory also goes through suggested mitigations to prevent such attacks – none of which will be surprising. They include: keeping products and systems patched and up to date, possibly by using a patch management solution; remove or isolate compromised (or suspect) devices from the network; network segmentation; disabling unused ports, and so on.
Notable for its absence in the advisory is any mention of Chinese vendor Huawei, whose equipment is now verboten from telco networks in the US and UK among other countries, and in the process of being removed.
Given the extent to which China-based attackers can gain access and exfiltrate data using non-Chinese devices, it suggests actual security concerns were once again not the most important consideration in removing Huawei from Western networks.
The full advisory is available as a PDF here.