
Zero trust is more a state of mind than a hard-and-fastened-down technical standard. You can’t simply buy a toolkit and roll it out.
BT, the world’s oldest telecoms company, is just 15 months into its zero trust journey and has already set its sights on achieving what Dave Harcourt, BT’s Chief Security Authority and Automation Director, regards as “level two” maturity. Read on to find out what that means.
Speaking at a recent Zcaler conference in The Hague, Amsterdam, Harcourt shared the challenges and lessons learned from rolling out zero trust across a complex data estate, legacy technology dating back decades and offices in 180 countries around the world. We were there to capture all his insights.
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
Life before Zero Trust
BT was founded in 1846 as the Electric Telegraph Company. Landmarks in its distinguished history include the laying of the world’s first submarine cable and the development of a process to produce glass pure enough to be used in fibre optics.
This legacy is impressive. However, its legacy tech is less so and creates major hurdles for the telecoms giant. For instance, BT still operates an analogue public switched telephone network, which is due to be replaced by a digital network in 2027.
“We run a phone network that was designed back in the 60s,” Harcourt said during the Zscaler event. “Most of our infrastructure is not designed for zero trust. Working out how we make sure that it is more zero trust-capable is a really important part of what we're doing.”
BT describes zero trust security as “a framework that requires all users, both inside and outside of an organisation’s network, to be identified and authorised before accessing the network”, which “trusts no one and nothing” and uses the mantra of “never trust, always verify”.
See also: BT's 'reverse flywheel' problem: CDIO inks fresh cloud deal, targets £600m/y legacy IT spend
In his three-stage conception of zero trust, Harcourt starts with Level Zero: assumed trust. This wretched state is based on the presumption that users, systems or devices are inherently secure and trustworthy without requiring additional verification or authentication measures. When this trust is misplaced, organisations have a problem.
Level One puts policy decision points (PDPs) and policy enforcement points (PEPs) in front of the network or applications, ensuring that all access requests are authenticated and authorised before the gates are flung open.
Finally comes the highest state of Zero Trust consciousness.
“The end goal is to get to what we call Level Two maturity in this space, which is a true zero trust approach that involves actually having that decision point right in the application,” Harcourt said.
“But for a long time, I suspect we'll be in a position where we've got policy decision and enforcement points sitting at the edge of the data centres, creating smaller and smaller domains of trust, as we migrate and move towards zero trust infrastructure.”
New security models for an old company
As BT transitions to a zero trust model, it is focused on reducing attack surfaces and managing legacy infrastructure.
"Zero trust brings simplicity and cleanliness,” Harcourt says. “It is also about putting security in one place to put blocks in place across our infrastructure to keep us safe when things go wrong."
For BT’s security innovator, a major initial obstacle to overcome is how to push organisations to adopt a new mindset.
“One of the biggest challenges we are going to face is not a technical issue,” he said. “It is a cultural shift. Having lived for so many years in the moat and castle, we’re now talking about perimeters, trusted domains and having zero trust ingrained into our policies, metrics, standards and way we work.”
BT is “hopefully - fingers crossed" going to run its first minimal viable product delivery at the end of this month” - which was June - by bringing 90 users on board.
In addition to Zcaler’s solutions, BT uses Microsoft's Entra ID as its identity provider (IdP) and is focused on securing endpoints, using tools from CrowdStrike, ServiceNow, and other Zscaler integration partners.
“I'm looking forward to a really nice journey, integrating all that together, and actually building out our ecosystem together,” Harcourt said.
Overcoming ARPANET
Although the BT security leader’s discussion focused on the future of secure access, it also flashed back to the beginning of the internet. The U.S. Advanced Research Projects Agency Network (ARPANET) was the first public packet-switched computer network and was switched on back in 1969. We’re still struggling with its legacy, Harcourt warned.
“ARPANET set out the foundational protocols the internet is built on,” he said. "It's hard to take that away because it's so fundamental [to keeping] the internet working. We are building on those foundations."
“When trying to build security on top of that, the important point is truly looking at how we protect traffic across our estate and between our users, devices, OT and IoT,” Harcourt continued. “That's the that's the goal and mission that we strive to achieve with Zero Trust.”
When ARPANET was built, availability was the priority to ensure continued operation, Harcourt pointed out. "There was no thought of security at the time it was built,” he said. “And ever since then, we've been looking at how we add security to the internet and make it a safe place."
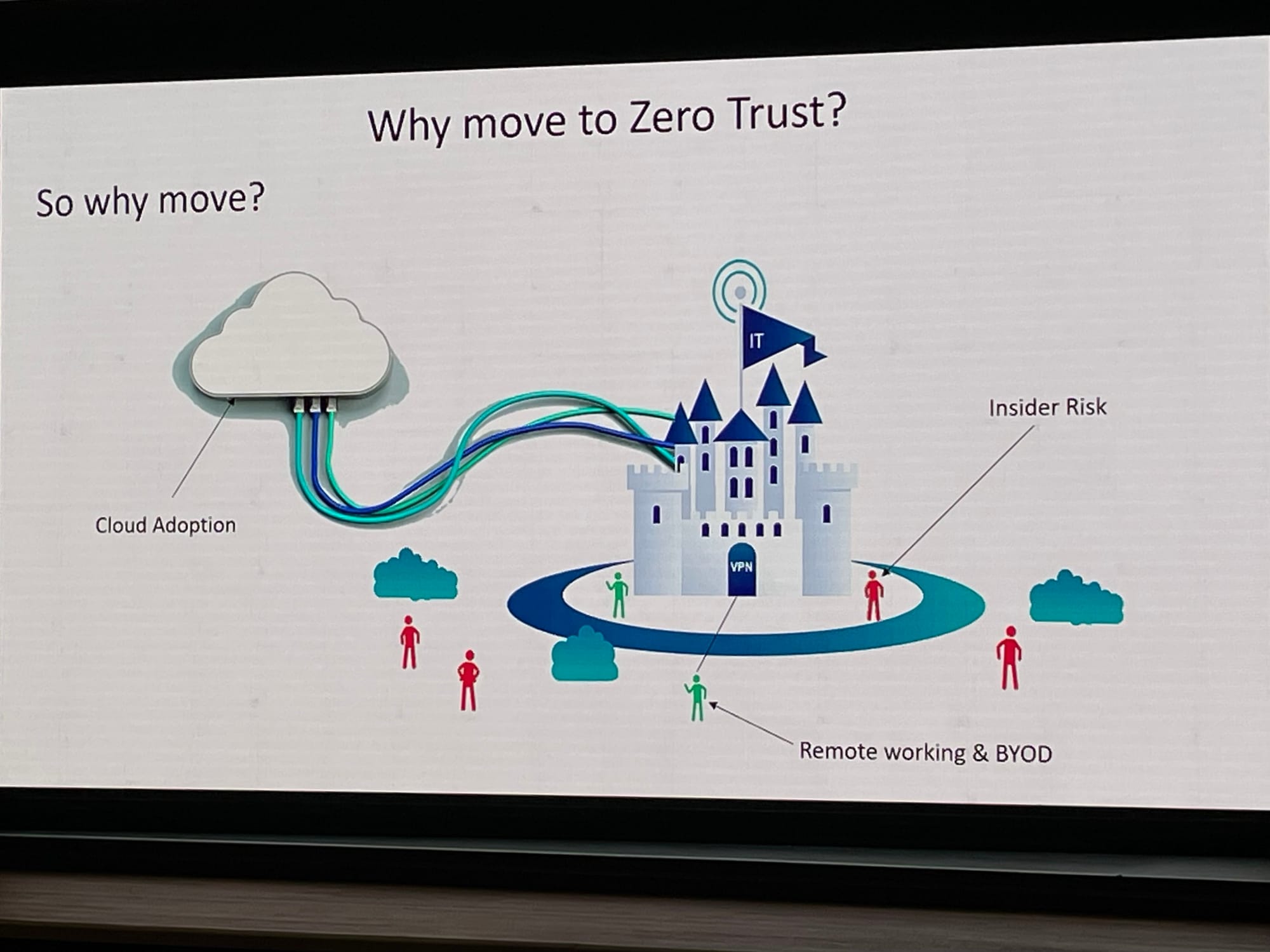
The threat landscape in 2024

Today's world is characterised by insider risk, BYOD, remote working, and “the biggest challenge of all - connecting to the cloud,” Harcourt advised.
Zero Trust principles (which you can see in the slide above) are created for this world, relying on policies such as explicit verification, applying a policy of least privilege, and assuming breach. It is being used to transform both BT employee and third-party access - which Harcourt calls “calming the chaos.”
“Reflecting on the proof of concepts we ran while choosing Zscaler as a partner, the biggest surprise was tackling the challenge of third-party access, which is probably the hardest issue we face today,” Harcourt revealed.
“It was surprisingly simple and easy to bring in a third party using federated identities, with much of our management infrastructure running clientless access for SSH onto our core infrastructure. It was a lot of work, but went so smoothly.”
It’s also replacing BT’s legacy and BWP web proxies and filters with a “one-stop block”. Access to BT resources was once delivered via layers of network controls and gateways, numerous manual application entitlement controls, and a process which assumes that an identity has been given to all users. This has now been replaced with a solution in which a zero trust access platform/ broker manages access across the network.
There are no inbound connections to BT applications, minimising attack surfaces. The solution also reduces the complexity of proxy architecture and accelerates cloud acceleration. Users connect to apps rather than networks, preventing lateral movement.
"Putting that risk on the outside and keeping it separate reduces the attack surface,” Harcourt said.