
In October 2023, the British Library was hit by a ransomware attack so severe that a former CEO of the National Cyber Security Centre described it as “one of the worst cyber incidents in British history”.
Now, almost one year after the incident, the world-famous library has revealed details of its £400,000 plan to move forward from the disaster - which left it with a website that still doesn't have a proper Content Management System (CMS) and forced the ongoing closure of both physical and virtual archives.
It has issued a £400,000 tender looking for contractors to take part in Phase 1 of its "Web Foundations" project, which involves rebuilding the website to ensure it is "robust, scalable, sustainable, and secure."
As well as giving users and editors "an excellent experience", the project will "allow for quick expansion of other content areas" and "provide a foundation for expansion and integration with backend systems" in future phases of development.
The tender also reveals details of the disastrous attack, setting out how the Library responded to the major cybersecurity incident.
"In 2022, we undertook a Web Discovery project, which identified the path for a world-leading, user-centred website," it wrote. "While laying the foundations for this, in October 2023 we experienced a catastrophic cyber-attack. It left us without a permanent website or access to many of the digital applications of the wider digital estate.
"In December 2023, we launched a small interim website to support users’ immediate needs. It does not have a CMS attached to it and is designed to be replaced by the outcomes of this brief."
The Library went on to set out details of its "journey of digital transformation and how it hopes to "transform the user experience and quality of our website and digital resources."
"Our aim is to deliver world-class digital experiences for a world-leading Library, building on modern, resilient, secure foundations," it added.
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
Recovering from ransomware
At the end of July 2024, the Library revealed that it was still struggling with the aftershocks of the attack.
Sir Roly Keating, Chief Executive, wrote: "The time it is taking us to bring our services back is an exact measure of the destructiveness of the original attack, which directly targeted our core computing infrastructure.
"Alongside the comprehensive rebuild of those systems – a process that would normally be scheduled over years rather than months – we have also been scanning our vast array of datasets to ensure that no malware or viruses have been left by the attackers.
"To date we have scanned more than 6 billion files and have, thankfully, been able to give all of them a clean bill of health. This painstaking process takes time, but we are continuing to follow a “safety first” approach – as you might expect after the experience of such a devastating attack."
Keating admitted that access to Non-Print Legal Deposit content (which includes digital material such as online articles, books, and websites) would not be up and running until September 2024 in facilities such as the National Library of Wales, the National Library of Scotland, the Bodleian Libraries, Cambridge University Library and the library of Trinity College Dublin.
This "tranche of restored content" will not include the UK Web Archive, "for which a different technical solution is required". This archive aims to store a record of British websites, but it still "currently unavailable", according to its own website.
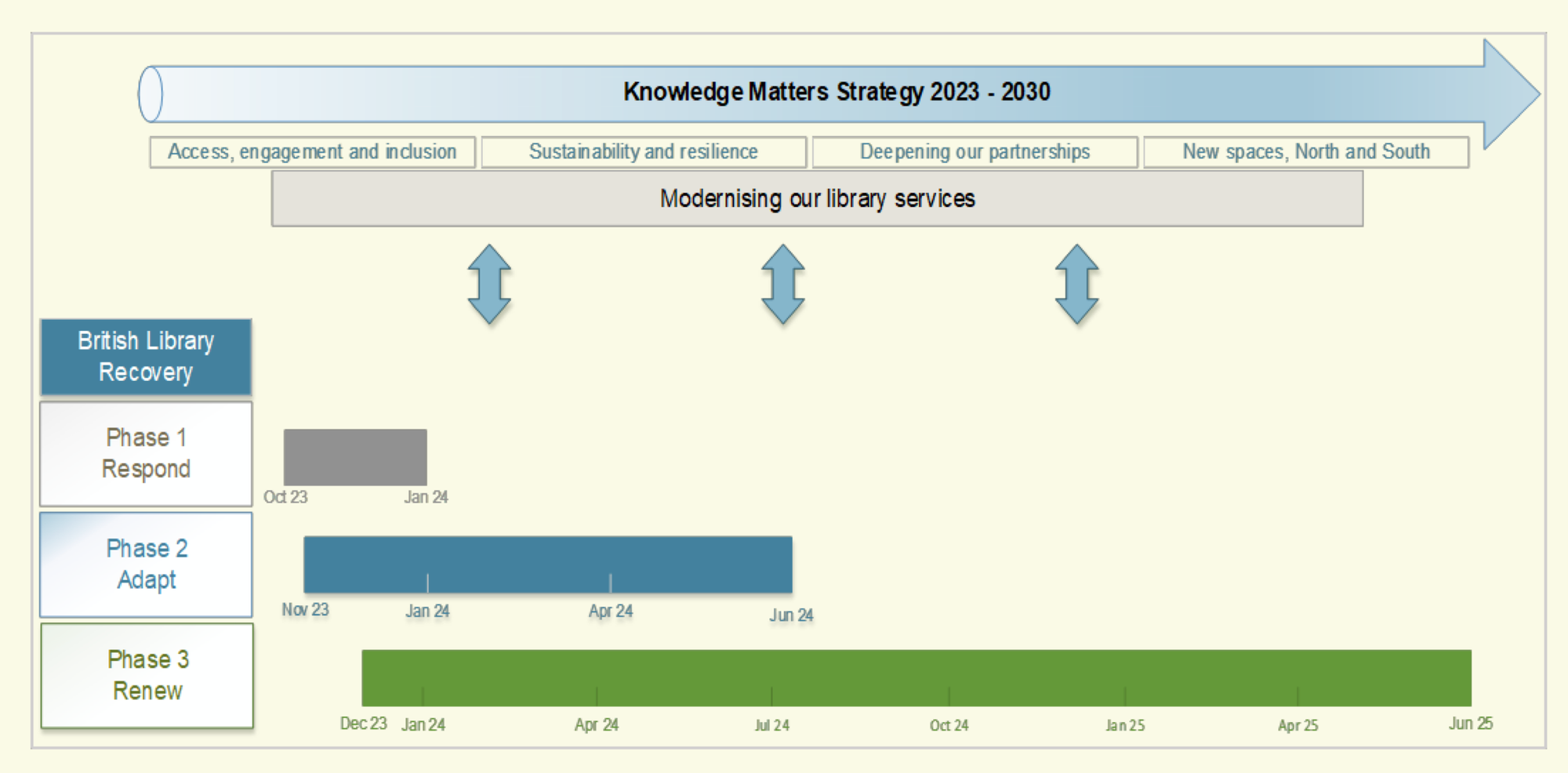
The Chief Executive also said that "two important parts of our physical collection at Boston Spa" have not yet "been restored to use" at the time at which he was writing - meaning that 262 kilometres of books held in its Automated Storage Building (ASB) and a physical newspaper collection housed in the National Newspaper Building remained inaccessible.
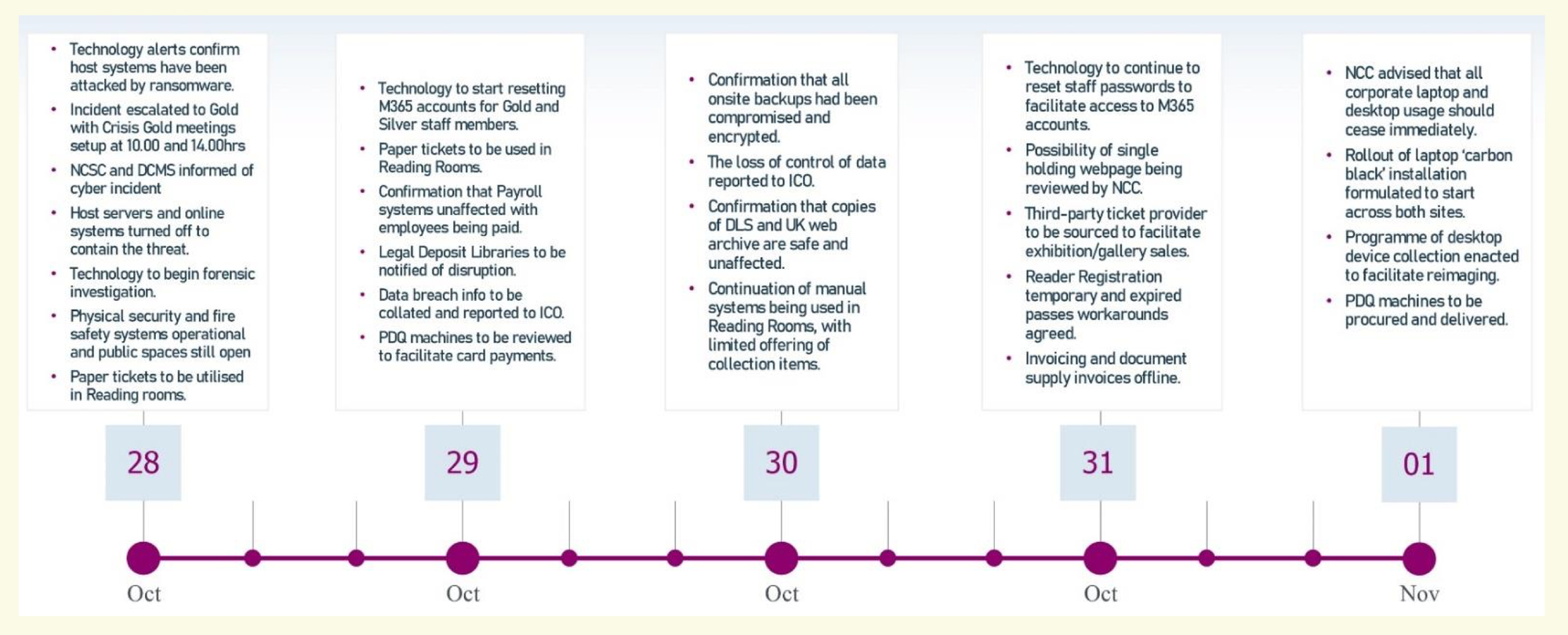
The incident unfolded on Saturday, October 28, 2023, when a group identifying itself as the Rhysida ransomware gang gained access through a vulnerable server.
The Library refused to pay a ransom of 20 bitcoins worth roughly £600,000 at the time after the attackers threatened to publish 500,000 files, including personal information and “exclusive, unique and impressive” data.
In a report on the incident, the British Library said "hostile reconnaissance" took place before the "major ransomware attack" and that its "security measures were not sufficient."
It wrote: "The criminal gang responsible for the attack copied and exfiltrated (illegally removed) some 600GB of files, including personal data of Library users and staff. When it became clear that no ransom would be paid, this data was put up for auction and subsequently dumped on the dark web.
"As well as the exfiltration of data for ransom, the attackers’ methods included the encryption of data and systems, and the destruction of some servers to inhibit system recovery and to cover their tracks. The latter has had the most damaging impact on the Library: while we have secure copies of all our digital collections – both born-digital and digitised content, and the metadata that describes it – we have been hampered by the lack of viable infrastructure on which to restore it."
The report also sets out Rhysida's attack methodology, which included defence evasion and anti-forensics to "clean up after themselves" by deleting log files, as well as "encryption for impact".
The nuking of servers had "the most damaging impact on the Library", which added: "Whilst we believe that we will eventually be able to restore all of our data, we are hampered temporarily by the lack of viable infrastructure on which to restore it.
"The Library’s vulnerability to this particular kind of attack has been exacerbated by our reliance on a significant number of ageing legacy applications which are now, in most cases, unable to be restored, due to a combination of factors including technical obsolescence, lack of vendor support, or the inability of the system to operate in a modern secure environment."
Investigators said the attack was likely to have involved the compromise of privileged account credentials via a phishing, spear-phishing, or brute force attack.