
The US’s Cybersecurity and Infrastructure Security Agency (CISA) has told federal agencies that they have two weeks to patch 105 known exploited vulnerabilities reported this year alone -- and a maximum of six months to patch a sweeping raft of security vulnerabilities assigned a CVE (vulnerability code) before 2021, as the government demands federal agencies “aggressively remediate known exploited vulnerabilities.”
Government patience with woeful patching rates is clearly running thin after umpteen exhortations and advisories to agencies around the country. CISA said the order, made in Binding Operational Directive (BOD) 22-01, applies to "all software and hardware found on federal information systems managed on agency premises or hosted by third parties on an agency’s behalf", adding November 3 that "these required actions apply to any federal information system, including an information system used or operated by another entity on behalf of an agency, that collects, processes, stores, transmits, disseminates, or otherwise maintains agency information."
(A BOD is a compulsory directive to federal, executive branch, departments and agencies for purposes of safeguarding federal information and information systems. CISA has issued 10 since 2015.)
Who's enforcing Binding Operational Directives?
Its ability to enforce BODs remains in question however. Even three years after their introduction, the then-assistant secretary for cybersecurity and communications at the Department of Homeland Security (DHS), acknowledged at an early 2018 public event that BODs were "a relatively new authority", adding: "I'm not exactly sure what sort of enforcement mechanism I have in place to make it binding... We don't have the authority to slap some fine on, and we're not going to kick some federal agency off the Internet."
Two years later, a February 4, 2020 report into the enforcement of DHS directives (CISA is under DHS oversight) by the US Government Accountability Office suggested things had not improved significantly.
It pointed to the September 27, 2016, BOD 16-02, "Threat to Network Infrastructure Devices". This was issued to agencies to fix critical flaws in Cisco ASA devices. Agencies were told to fix them within 45 days. As the 2020 oversight report noted however, it took six months to fix 50% of impacted devices through patching, adding: "Agencies completed all requested actions by October 2018, which was 2 years past the deadline."
That report added bluntly and worryingly: "While we recognize that CISA does not have the automated tools or capacity to independently validate every self-reported action taken by agencies to meet binding operational directive requirements, CISA can take a risk-based approach to validation. Guidance from OMB and executive orders emphasize risk-based approaches to information security. However, CISA did not take a risk-based approach, and it also did not have a strategy in place to check selected agency-reported actions to validate their completion. Without taking such an approach or having a strategy in place, the likelihood for requirements to not be completely or correctly addressed is increased. This could leave computer networks and systems used by federal agencies riddled with security vulnerabilities—both known and unknown.."
In the years since, reporting is understood to have improved somewhat and as CISA noted on November 3, 2021, all federal agencies are now expected to "automate data exchange and report their respective [patch management] implementation status through the CDM [Continuous Diagnostics and Mitigation] Federal Dashboard.
CISA added: "Initially agencies may submit quarterly reports through CyberScope [a web-based application developmed by the Department of Homeland Security] submissions or report through the CDM Federal Dashboard. Starting on October 1, 2022, agencies that have not migrated reporting to the CDM Federal Dashboard will be required to update their status through CyberScope bi-weekly."
This patching, of course, is critical and not just for basic cyber hygiene reasons (nobody wants a ransomware attack or cryptominer on their machine), but for national security reasons too.
As a joint advisory from the UK’s NCSC, US’s CISA and Australia’s ACSC in July 28, 2021 emphasised, low hanging fruit are widely used by nation start adversaries too, noting that "focusing scarce cyber defense resources on patching those vulnerabilities that cyber actors most often use offers the potential of bolstering network security while impeding our adversaries’ operations... For example, nation-state APTs in 2020 extensively relied on a single RCE vulnerability discovered in the Atlassian Crow (CVE-2019-11580)."
| Citrix | CVE-2019-19781 | Arbitrary code execution | CVSS: 9.8 | Exploit |
| Pulse Secure | CVE 2019-11510 | Arbitrary file reading | CVSS: 10 | Exploit |
| Fortinet | CVE 2018-13379 | Path traversal | CVSS: 9.8 | Exploit |
| F5- Big IP | CVE 2020-5902 | RCE | CVSS: 9.8 | Exploit |
| MobileIron | CVE 2020-15505 | RCE | CVSS: 9.8 | Exploit |
| Microsoft | CVE-2017-11882 | RCE | CVSS: 9.3 | Exploit |
| Atlassian | CVE-2019-11580 | RCE | CVSS: 9.4 | Exploit |
| Drupal | CVE-2018-7600 | RCE | CVSS: 9.8 | Exploit |
| Telerik | CVE 2019-18935 | RCE | CVSS: 9.8 | Exploit |
| Microsoft | CVE-2019-0604 | RCE | CVSS: 9.8 | Exploit |
| Microsoft | CVE-2020-0787 | Elevation of privilege | CVSS: 7.8 | Exploit |
| Netlogon | CVE-2020-1472 | Elevation of privilege | CVSS: 10 | Exploit |
The 12 most-exploited vulnerabilities of 2020: Credit CISA/NCSC/FBI
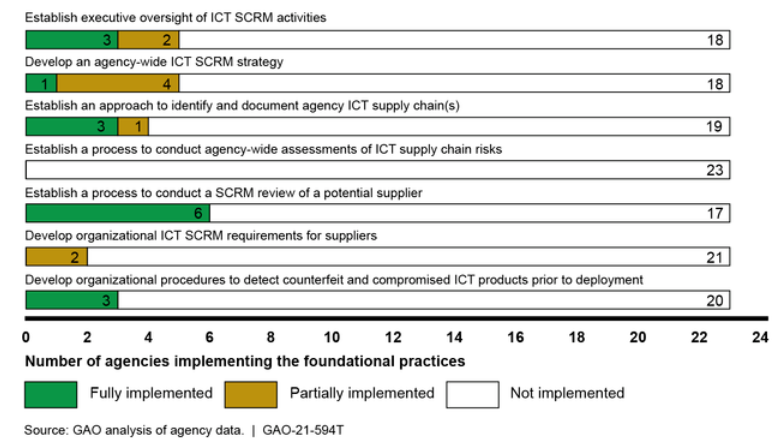
Another report by the Government Accountability Office (an independent agency that reports to Congress) published in May 2021 further emphasises auditors' concern at inadequate federal agency cybersecurity practices, noting wearily in the wake of the SolarWinds breach that "federal information security has been on our High Risk List since 1997" but that NONE of 23 civilian agencies it audited had "fully implemented selected foundational practices for managing information and communication technology (ICT) supply chain risks."
The agency's work deserves more credit. In June 2019, well before the Colonial Pipeline attack, GAO emphasised presciently that "more than 2.7 million miles of pipeline that transports and distributes the natural gas, oil, and other hazardous liquids that U.S. citizens and businesses depend on, increasingly rely on sophisticated networked computerized systems and electronic data, which may be vulnerable to cyberattack or intrusion."
The Stack has contacted CISA for comment on what it is doing to improve BOD compliance and will update this story with their comment when we receive it.
