
It may be time to add Castor canadensis to your threat model. The humble beaver triggered a sweeping internet outage in one corner of Canada on June 7 after chewing down a tree which fell on a fibre optic cable line in British Columbia. One local official told regional media this week that "it's unusual, but it does happen every once in a while. I wouldn't be a rich man if I had a nickel for every beaver outage, but they do happen.”
The Stack, whilst wanting to write more about beavers (we otter know better), could only realistically get 81 words out of the above incident, so we decided to use the opportunity to explore what causes most telco security incidents across Europe, which publishes this rarely reviewed data via its handy “CIRAS” tool.
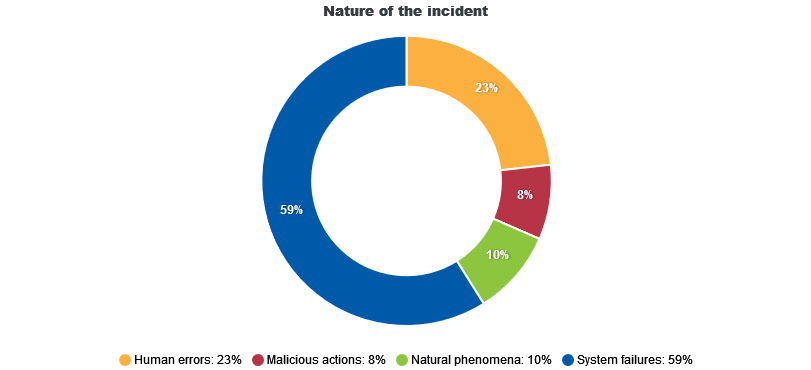
Strictly, CIRAS holds anonymised data on security incidents, but telcos take a broad view of this to include outages with a potential security impact.
Connect with the team and follow The Stack on LinkedIn
Data for 2021 shows that just two telecommunications security incidents were ascribed to "natural phenomena"; one due to flooding, the other not categorised, but conceivably a beaver.
"System failures" accounted for the vast majority (59%) of telco security incidents.
Of these many "system failures" it was hardware rather than something with soft fur that was primarily to blame -- taking out a massive 4,432 million user hours in 2021, per the CIRAS chart below.
These are not categorised in any meaningful depth; just one incident of a cable cut makes, well, the cut. (Although these are of course frequent, they have not made the reporting threshold here which spans "cybersecurity incidents with a significant impact to the national authorities in their country"...)
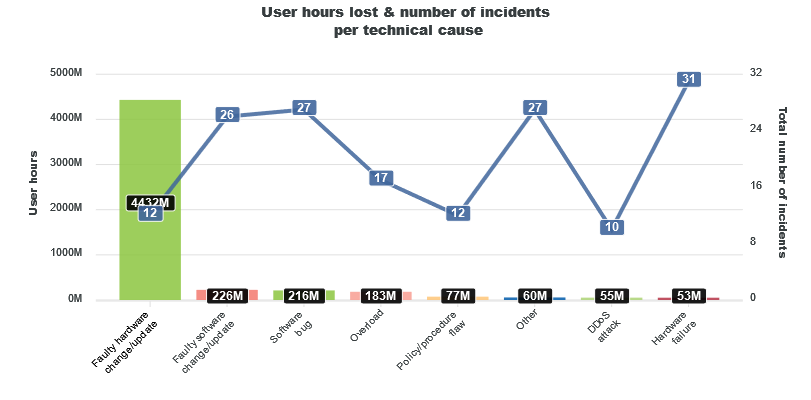
Incidents broadly categorised simply as "software bug" were also common, European data shows; the impact primarily hitting mobile telephony/mobile internet users rather than fixed broadband providers.
The data comes as telcos continue to be some of the region's biggest spenders on digital transformation.
That investment comes as consumers demand ever more bandwidth-heavy activities like remote learning, gaming, and video conferencing. Telcos meanwhile have been shifting from a world in which network functions are running on specialist dedicated hardware, to one in which virtualisation has rendered physical functions as software – which can be run as VMs or containers over general-purpose servers -- and indeed to more sophisticated "network slicing" which enables multiple virtual networks to be created on a single physical network infrastructure.
(This lets different service characteristics and quality parameters be assigned to each network ‘slice’, with full isolation between slices, enabling operators to develop new differentiated services and business models.)
Security in the sector meanwhile appears to continue to need investment: a group of teenage hackers earlier this year were able to easily buy VPN credentials for T-Mobile on the dark web and used their access to download over 30,000 source code repositories — even gaining access to Atlas, an internal T-Mobile tool for managing customer accounts. Reporter Brian Krebs noted at the time: "Anyone can access dark web bot shops like Russian Market and Genesis, which means larger companies probably should be paying someone to regularly scrape these criminal bot services, even buying back their own employee credentials to take those vulnerable systems off the market... That’s probably the simplest and cheapest incident response money can buy.”
Too serious? We leave you with a beaver joke.
Q: "Why did the beaver get into trouble?
A: Illegal streaming..."
