Hackers masquerading convincingly as global financial institutions are using backdoored Windows applications to deliver malware as part of an ongoing spear-phishing campaign, new research from UK-based threat intelligence firm Cyjax reveals -- with the applications seeing very low detection ratings on VirusTotal.
Following up on a May 12 FBI private industry notification about the spear-phishing campaign, Cyjax identified "additional files and phishing pages connected to this ongoing campaign that has been running since at least 2017." (IOCs are here). These include domains masquerading as some of the world's highest profile banks.
The attackers send a targeted email to the target containing one such URL and login credentials for a fake website. When these credentials are used to enter the site, the victim downloads an installer which unpacks a ZIP file. This delivers the backdoored application (built using open source tool Squirrel) which, if executed by the user, provides access to the device via a legitimate remote access tool like TeamViewer.
Follow The Stack on LinkedIn
By way of example, FBI pointed in its advisory to one recent attack by the unknown group which saw them impersonate a US-based financial institution to target an American renewable energy company. The spear-phishing email referenced a fictitious loan and instructed the target organisation’s employees to download a Windows application so as to complete the loan process to receive $62 million.
Implausible though this may seem as a technique, given the financial scale, threat actors are becoming highly sophisticated at crafting such emails; often picking up on email chains from previously leaked tranches of emails (e.g. of a customer) to lend legitimacy to the correspondence.
In 2020 for example., one Premier League football club's Managing Director fell victim to a spear-phishing attack that led him to spoof Microsoft 365 login page, where he passed on his credentials to criminals -- who assumed the identity of the MD and communicated with another club to set up a £1 million player transfer. The subsequent financial transaction was only thwarted because the bank had a fraud marker against the account.
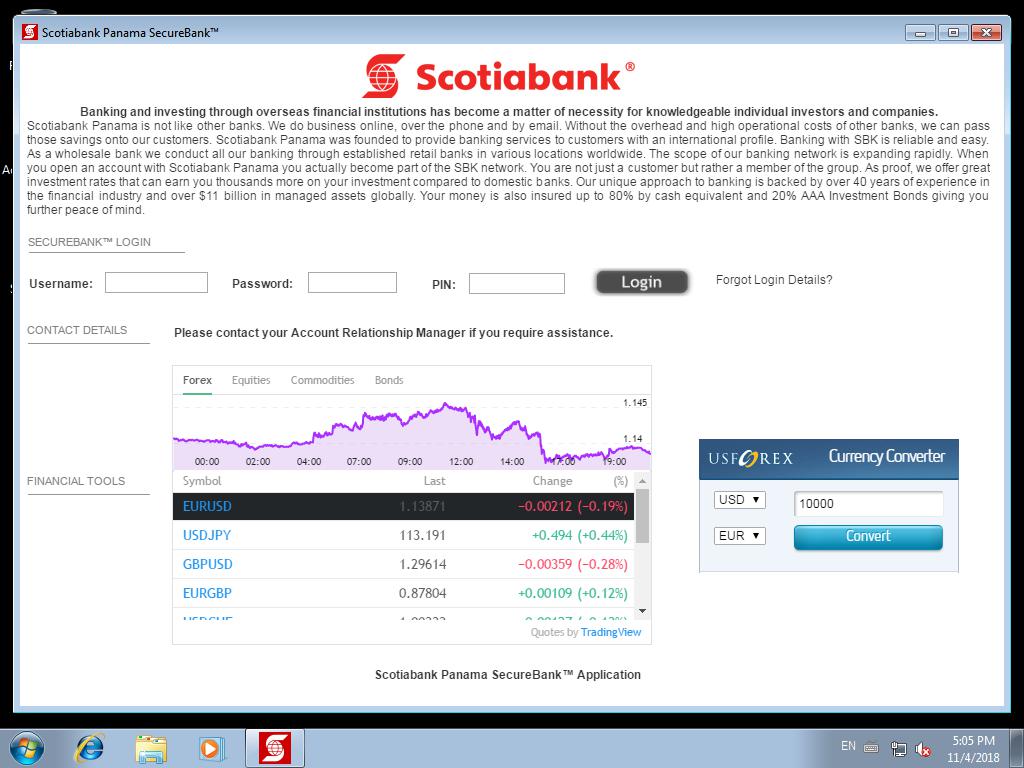
Investigating the FBI notice further, Cyjax also found that the same servers used by the attackers also hosted several domains impersonating the FBI, Europol, HM Revenue & Customs, the Bank of England, US Federal Reserve, US Treasury, and the World Bank. These had yet to be used.
Actively used in the campaign were domains and fake Windows applications dressed up as institutions like Cumberland Private Wealth, Truist, First National Bank of America, MayBank Private Malaysia, Central Bank of West African States (BCEAO), Chase Trust, and the Postal Savings Bank of China, BNY Mellon, Scotiabank Panama, Multibank Panama, BB&T, and MetroBank.
"This highly targeted campaign has yet to be attributed to a known APT or cybercriminal group" said Cyjax. "Its success rate is currently unknown, but the campaign combines multiple techniques corresponding to somewhat sophisticated cybercriminals, making it a serious threat. Using the information harvested from backdoored systems, the attackers can access their victims’ accounts and various other sensitive data to further compromise the target networks or steal more funds.
As Cyjax notes, using fake applications as part of a social engineering campaign is not new news in itself: North Korean APT the Lazarus Group, for example, used its backdoored AppleJeus application to target hundreds of organisations in over 30 countries during 2020.









