
AWS has (finally) made it possible for security teams to centrally manage root access for member accounts in AWS Organizations.
It has also made it possible for new accounts to no longer get a root user by default – a move welcomed with giddy delight by platform engineers and cloud security leaders managing swathes of AWS accounts.
As AWS admitted frankly:
"For a long time, Amazon Web Services (AWS) accounts were provisioned with highly privileged root user credentials, which had unrestricted access to the account. This root access, while powerful, also posed significant security risks. Each AWS account’s root user had to be secured by adding layers of protection like multi-factor authentication (MFA). Security teams were required to manage and secure these root credentials manually. The process involved rotating credentials periodically, storing them securely, and making sure that the credentials complied with security policies.
The move comes amid an overhaul of Identity and Access Management (IAM) this week – with a newly refreshed “Access Analyzer” making it easier for security leaders to “identify and remediate unused access.”
What is AWS IAM Access Analyzer?
IAM Access Analyzer helps users identify and review unused access in their AWS organisation by continuously monitoring all IAM roles and users. It generates findings that highlight unused roles, unused access keys for IAM users, and unused passwords for IAM users, for example.
“AWS Root Access Management is here! Kiss that stupid compliance MFA on root-finding goodbye!!!” said one cloud security leader at a major bank with sheer relief this week. He was far from alone in that view.
“Wow. I honestly thought this day would never come 😭” commented Dakota Riley, a staff security engineer at a data collaboration platform, as the news broke via JPMorgan’s delighted Houston Hopkins on LinkedIn.
“Nice, been waiting for this forever!”; “Finallly”; and “Never thought this day would come. Fake news?” were among the responses from relieved customers; the latter from Head of DevSecOps at Adobe, Ammar Alim.
"It’s real! :) I tested before I posted to make sure :) Also awesome is that once enabled all new AWS account creations no longer get a root user by default!!" responded a delighted Hopkins; one of the industry's most respected cloud security engineer on the defense side.
(When operating at the tens-of-thousands-of-account-holders scale, identifying who has root access when it is spun up by default, then ensuring it is MFA-protected is no mean feat; this makes it a lot easier.)
“This has been such a burden for years, especially for those organizations that have 100s of accounts. It is very welcome by all Cloud Platform Engineering and Security folks” added SWIFT's Gilles Baillet.
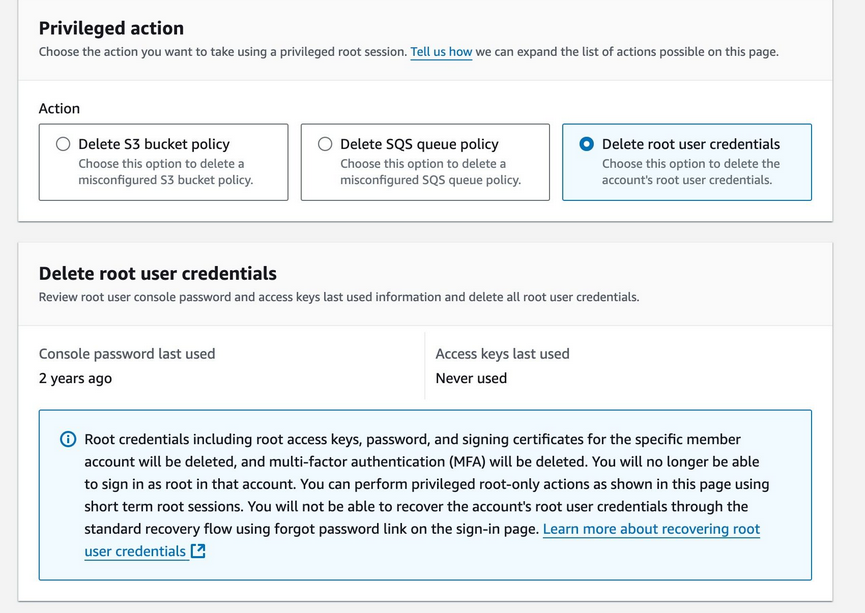
AWS root user default deletion
Updated AWS documentation shows that users can centrally secure access to root user credentials for member accounts in “AWS Organizations” (a central account management service) and combine all AWS accounts for central management. Deleting root users still requires a few steps.
"After carefully evaluating customer feedback we heard that customers would want to perform these delete actions with care" AWS IAM head of product Raymond Ma explained on Friday (November 15.)
"Therefore, they were not likely to utilize a one-click delete all root credentials from a group of accounts option. However, we will be releasing a blog shortly with an example script you can utilize to programmatically manage root credentials across the accounts in your organization."
(The Stack will update this piece with that link when we have it.)
"The capability to perform privileged tasks (such as unlocking an S3 bucket policy that denies all access) is [also now] available in GovCloud and China!" added Ma: "This is super exciting for us because customers can now self-service these actions without contacting Support. We hope you like it :)
"The root credential management capability is not available in GovCloud or China, but that's solely because there aren't any root credentials to manage in those two partitions" he added on November 14.
"When you enable AWS Organizations, you combine all your AWS accounts into an organization for central management. Each member account has its own root user with default permissions to perform any action in the member account... After you centralize root access, you can choose to delete root user credentials from member accounts in your organization. You can remove the root user password, access keys, signing certificates, and deactivate and delete multi-factor authentication (MFA).
New accounts you create in Organizations have no root user credentials by default. Member accounts can't sign in to their root user or perform password recovery for their root user - AWS Documentation.
See also: AWS adds cost controls, cross-region inference bursts to Bedrock, as enterprises mull best gateways
AWS said that well as the above, centralising root access lets you...
Perform privileged tasks that require root user credentials
Some tasks can only be performed when you sign in as the root user of an account. Some of these Tasks that require root user credentials can be performed by the management account or delegated administrator for IAM. To learn more about taking privileged actions on member accounts, see Perform a privileged task.
Enable account recovery of the root user
If you need to recover root user credentials for a member account, the Organizations management account or delegated administrator can perform the Allow password recovery privileged task. The person with access to the root user email inbox for the member account can reset the root user password to recover root user credentials. We recommend deleting root user credentials once you complete the task that requires access to the root user.
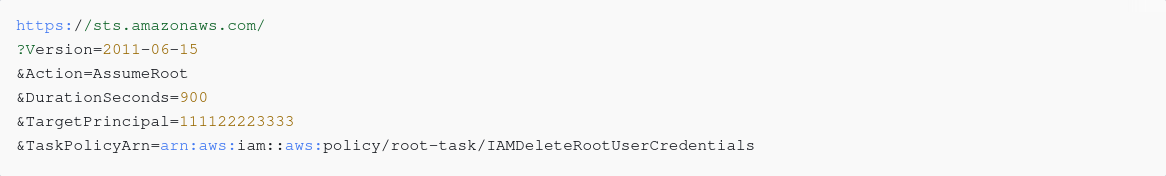
Red Teams may be taking note of the fact that sts:AssumeRoot is also here. This "returns a set of short term credentials you can use to perform privileged tasks in a member account" (for those organisations in which centralised root access is enabled.)
Additional comment and links to follow. Views? Pop us a line.
