Mandiant and Google's Threat Analysis Group (TAG) have warned that a China-linked threat group called ATP 41 is targeting and compromising "multiple organisations" in the media, entertainment, technology, automative and global industries.
ATP41, also known as "Double Dragon", is an established cyber threat group that carries out Chinese state-sponsored espionage activity. Security researchers suspect that it is also involved in financially motivated attacks and may operate outside of total state control.
In the recently observed intrusions, the malicious actor deployed a combination of ANTSWORD and BLUEBEAM web shells for persistence against organisations mainly operating out of Italy, Spain, Taiwan, Thailand, Turkey, and the United Kingdom.
The threat actors then deploy DUSTTRAP dropper which decrypts a malicious payload and executes it in memory, leaving minimal forensic traces.
"DUSTPAN is an in-memory dropper written in C/C++ that decrypts and executes an embedded payload. Different variations of DUSTPAN may also load an external payload off disk from a hard-coded file path encrypted in the Portable Executable (PE) file," the report explained.
DUSTPAN was previously deployed by ATP41 in several 2021 and 2022 breaches, while DUSSTRAP is its associated malware component.
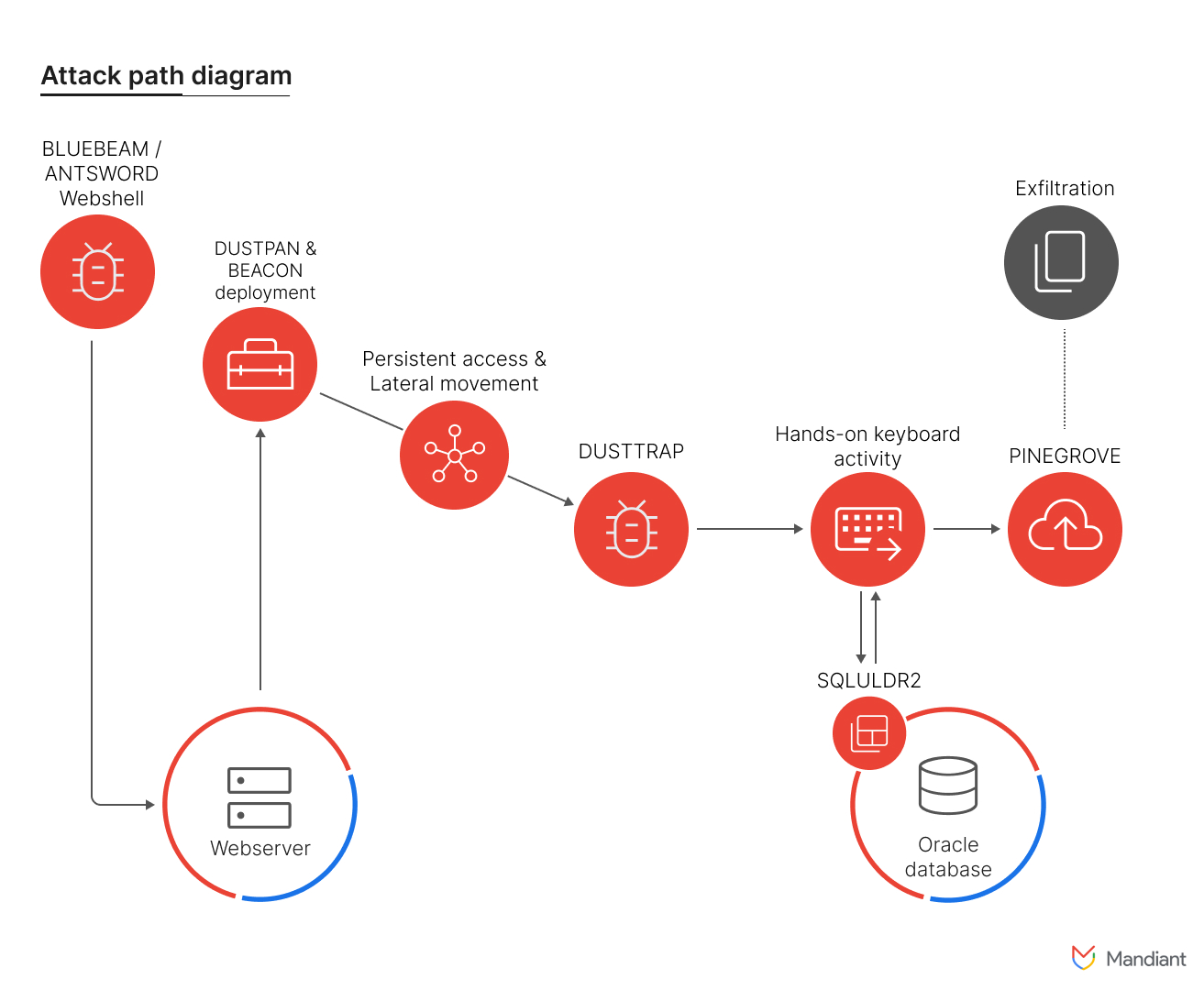
"The decrypted payload was designed to establish communication channels with either APT41-controlled infrastructure for command and control or, in some instances, with a compromised Google Workspace account, further blending its malicious activities with legitimate traffic," the report noted.
"The DUSTTRAP malware and its associated components that were observed during the intrusion were code signed with presumably stolen code signing certificates," it added.
The attacks have a wide geographic spread - with nearly all targeted organizations operating in the shipping and logistics sector located in Europe and the Middle East, and the media and entertainment sector in Asia.
Previously, APT41's financially motivated intrusions have "primarily targeted the video game industry, involving activities such as stealing source code and digital certificates, manipulating virtual currencies, and attempting to deploy ransomware," Mandiant wrote.
"APT41 is unique among tracked China-based actors in that it utilises non-public malware typically reserved for espionage operations in activities that appear to fall outside the scope of state-sponsored missions," reseachers explained.
A complete list of IOCs can be found here.








