A record 26,448 software security flaws were reported in 2022, with the number of critical vulnerabilities up 59% on 2021 to 4,135, according to analysis by The Stack of Common Vulnerabilities and Exposures (CVEs) data.
CVEs are a catalogue of publicly disclosed cybersecurity vulnerabilities. They refer to a specific instance of a vulnerability within a given product or system: i.e. the primary Log4J vulnerability was CVE-2021-44228.
The soaring numbers – equivalent to a fresh CVE being created every 20 minutes – illustrate the pressure on those needing to risk-assess vulnerabilities and assess organisational exposure as part of cybersecurity efforts.
As the chart of attack vectors below shows, the vast majority do not require physical or local network access, but can potentially be exploited remotely (dependent on a concatenation of things coming together for an attacker.)
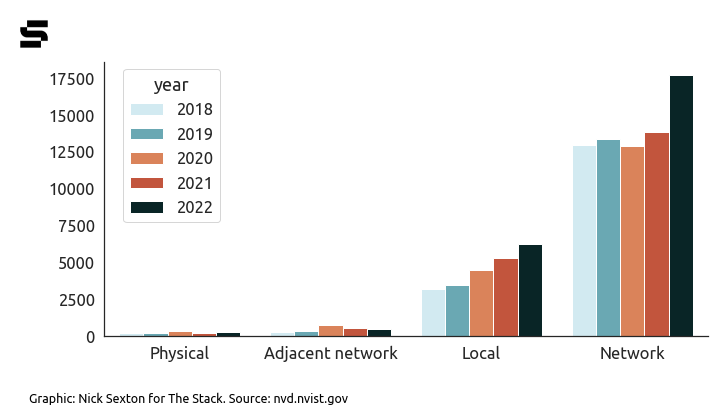
Unpatched software is a top three access route for hackers and patching, says the UK’s National Cyber Security Centre (NCSC) “remains the single most important thing you can do to secure your technology.”
(It acknowledges that “sometimes a patch breaks something vital, in a way you couldn't reasonably have foreseen [and] “it's hard to maintain accurate, up-to-date asset inventories [of things to patch] across larger IT estates.”)
Our analysis of the past five years worth of CVE data from NVD – a US government repository of vulnerability data – also shows that well-known application security categories remain rampant and continue to grow.
Don't miss out on our news and events: Follow The Stack on LinkedIn
This was reflected in the rise in frequency of many of the top 25 most dangerous Common Weakness Enumeration (CWE) types over the past five years, for example cross-site scripting (XSS) and SQL Injection weaknesses. (CWEs are potentially exploitable weaknesses that can occur in architecture, design, code, or implementation: The CWE open standard “dictionary” is maintained by The MITRE Corporation.)
nb: To create the "Top 25" list the CWE team assessed Common Vulnerability Scoring System (CVSS) scores associated with each CVE record and CWEs associated with CISA's Known Exploited Vulnerabilities (KEV) Catalog and applied a formula to score each weakness based on prevalence and severity. The Stack then ran a search for the prevalence of these top 25 most dangerous CWE types in NVD's CVE database by year from 2018-2022.
This reveals a notably sharp rise in cross-site scripting, memory corruption, and SQL injection bugs.
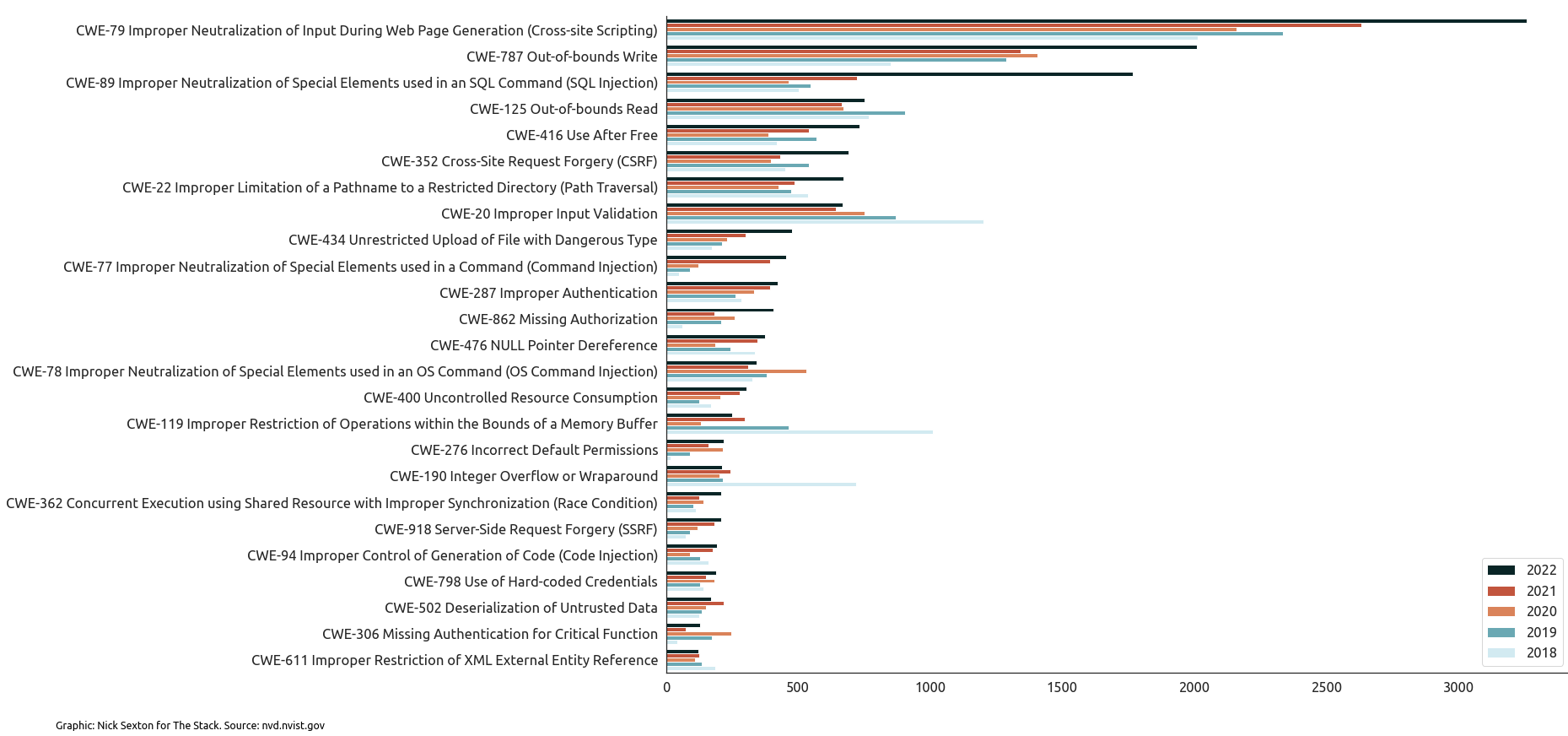
Amy Stokes-Waters, an offensive security specialist and co-founder of Capture the Talent said of The Stack's analysis: "The data is really interesting here and points to a number of trends I think we’re seeing in the market at the moment. The first is the rise of bug bounty platforms and programmes offered by either third party organisations like BugCrowd, HackerOne, Intigriti, etc and by tech companies themselves… Having more of these types of programmes around provides incentives for more people to try and find issues in the first place.
She added: "The second thing I think we can extrapolate from this is that we’re doing more security testing, which can only be a good thing. Companies and consumers are taking cyber security more seriously, protecting data is becoming a priority, and so organisations are having to invest in either more penetration testing services or set up bug bounty programmes to supplement their own security capabilities.
"However, I do think the fact that we’re seeing significant rises in things like XSS and SQL injection says to me that coding practices are not getting more secure, despite DevSecOps being a big talking point.
"So it potentially highlights that there is a training issue around secure coding... although without understanding each vulnerability in its own context, it’s difficult to say for sure."
CVEs in 2022: Which companies saw the most?
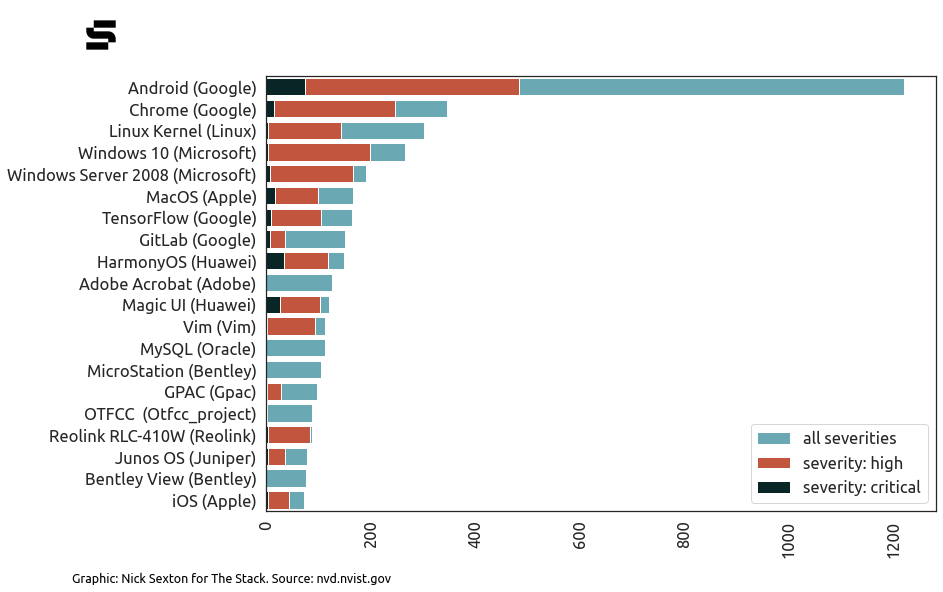
Google had the most software security issues reported and fixed in its products in 2022 according to analysis by The Stack – with Android and Chrome topping the list of products allocated CVE codes for their vulnerabilities.
This does not suggest that they were the least secure software products of 2022. Rather, simply that security researchers reported the most vulnerabilities in them. This may be due to mature bug bounty programmes. (The Chrome bug bounty programme, for example, launched in 2010 and has an expansive scope.)
For security researchers to find such vulnerabilities, of course, they do need to be there to start with...
It does emphasise how much Microsoft CVEs tend to dominant cybersecurity conversation however.
(Michael Clark, Director of Threat Research at Sysdig pointed out that "when it comes to vulnerabilities, 'quality' is more important than quantity. Quality, in terms of vulnerabilities, consists of how many targets are affected, how easy it is to exploit, and the resulting impact. While Android has had a large amount of vulnerabilities, and may have a large number of users, the ease of exploiting them and the impact isn’t as great...")

As Paul Baird, Chief Technical Security Officer UK at Qualys told us: “I would have lost my house betting on which platform / application generated the most CVEs during 2022. Most of the industry and I am guilty of this, always putting Microsoft up there as the worst offender, but the data clearly shows otherwise…
He added: “One of my 2023 predictions is a rise in attacks on mobile devices. Seeing that Android is carrying the most critical and high severity vulnerabilities in 2022, I would say this data puts an even bigger target on mobile devices. Although most of us would be lost if we did not have access to a mobile device due to it being lost or broken, we don’t put as much emphasis on it being compromised. Looking back at past experiences, we put less effort into securing mobile devices than we do for the rest of the estate (Servers, Laptops, Cloud). Sure, it is on the list of things to do, but it always tends to be towards the bottom of the list; this may need to change.
Data analysis by Nick Sexton (Twitter @nickjsexton; Mastodon @nicksexton@fosstodon) who used the NVD API to retrieve data from all logged vulnerabilities for the last five years and wrote a Python script to parse the raw json data to create human-readable fields for each vulnerability entry in the database and reconcile the entries using cvssV2 with cvssV3 reporting schemes. For the CWE data, the data was retabulated on a CWE level (each vulnerability may list multiple CWEs). The data was tabulated and graphed using the Pandas and Seaborn Python packages.)









