
America’s largest water company is “disconnecting or deactivating” some of its IT systems after detecting a cybersecurity breach, it has confirmed.
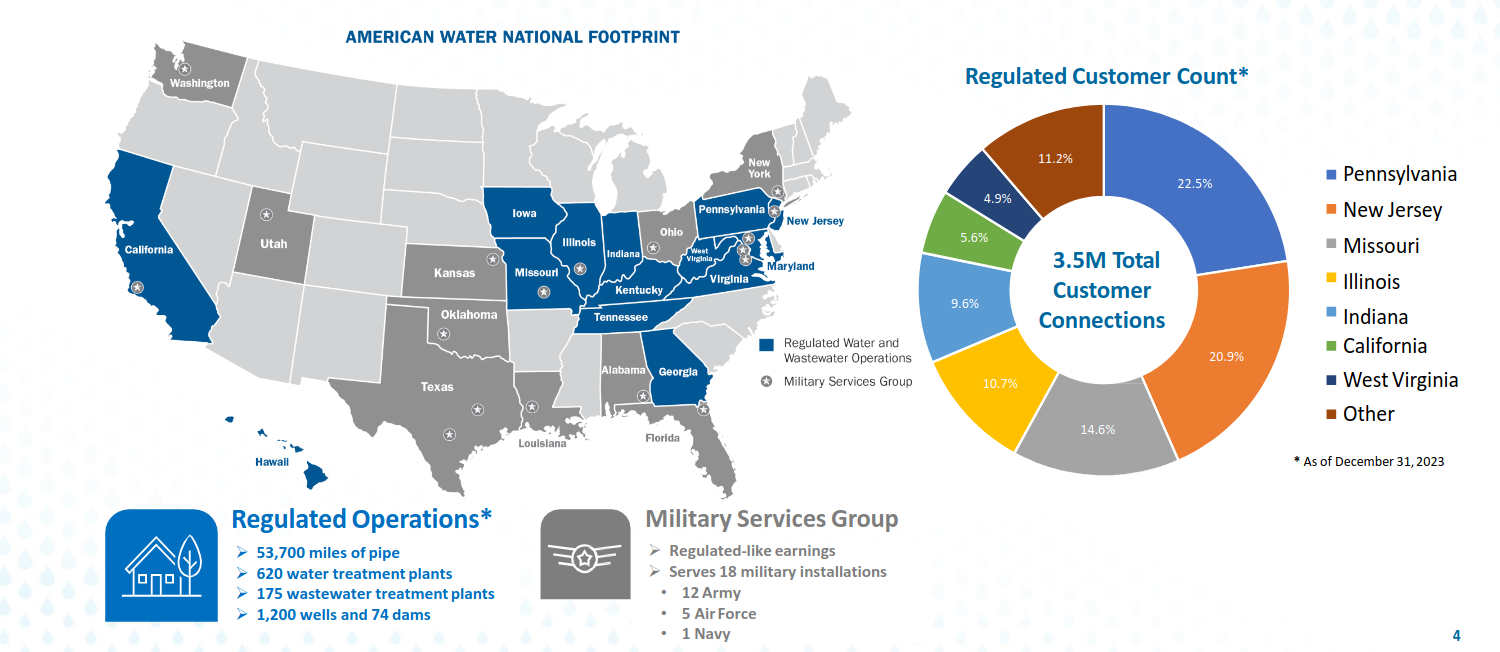
American Water operates 53,700 miles of pipe, 1,200 wells, 620 water treatment plants, 175 wastewater treatment plants and 74 dams.
It also serves 18 military installations with water services.
The attack has forced it to take down its billing services, it said in an FAQ page on its site – that returned a “403 Forbidden” as The Stack published.
An investor relations page on a subdomain remained accessible.
American Water said it has brought in incident response professionals and contacted law enforcement. None of its physical infrastructure is at risk it said.
American Water hacked: IR activated
The company said in an SEC filing that on October 3 it “learned of unauthorized activity within its computer networks and systems, which the Company determined to be the result of a cybersecurity incident.
The filing said: “Upon learning of this activity, the Company immediately activated its incident response protocols and third-party cybersecurity experts to assist with containment and mitigation activities… The Company currently believes that none of its water or wastewater facilities or operations have been negatively impacted by this incident”.
In its 2023 annual report, American Water noted that it has "obtained insurance to provide coverage for a portion of the losses and damages that may result from a physical attack, cyber attack or a security breach, but such insurance is subject to a number of exclusions
and may not cover the total loss or damage caused by an attack or a breach..."
Whether through effective network segmentation between IT and OT, or attacker incompetence/lack of familiarity with the latter, most recent attacks on utilities appear to have failed to bridge the gap to OT systems.
The NSA warned in May 2024 that Russian “hacktivists” however were expanding their targeting “to include vulnerable North American and European industrial control systems,” as the NSA’s new director of cybersecurity Dave Luber put it at the time.
The NSA/CISA advisory urged basic cyber-hygiene efforts like the hardening of human machine interfaces, “limiting exposure of OT systems to the internet, using strong and unique passwords, and implementing multi-factor authentication for all access to the OT network.”
The US's water sector, which is riddled with legacy technology and which does not always have well resourced IT functions, let alone cybersecurity ones, may soon face pressure to change its ways.
House Bill 7922, introduced in April 2024 with the aim of establishing a new governing body, the WRRO, is currently under deliberation in Congress. If passed, it mandate cyber-resilience requirements and implementation plans, to be approved by the Environmental Protection Agency (EPA).
The WRRO would be able to conduct monitoring and assessment of utilities and impose penalties for non-compliance.
