The impact of back-to-back breaches of Accellion's File Transfer Appliance (FTA) software in December and January continues to reverberate, with supermajor Shell the latest to send shockwaves with the news that it suffered the loss of "personal data and... data from Shell companies and some of their stakeholders".
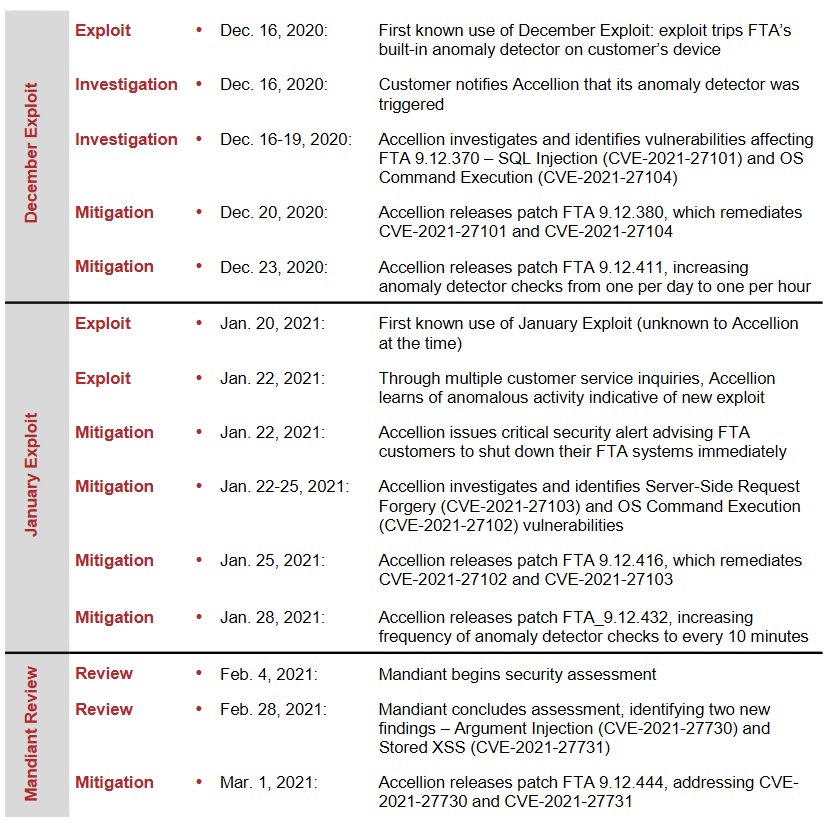
Palo Alto-based Accellion was compromised via two critical pre-authentication RCE zero days in December: a SQL injection and a command injection bug respectively. After patched them on December 20 and 23 it was promptly compromised again via two more zero days; on January 22 issuing a critical security alert advising FTA customers to shut down their FTA systems immediately after seeing anomalous activity indicative of a new exploit.
By then the horse had bolted: known victims include the the Australian Securities and Investments Commission; New Zealand's Central Bank; Singaporean telecom Singtel; and cybersecurity firm Qualys which saw sensitive contractual data and Red Team analysis posted to an onion site after the breach in an extortion campaign.
Accellion hack: Shell says no broader IT impact
Shell, like many, was using Accellion's FTA to "securely [sic] transfer large data files" and as a result -- like scores of other users -- has lost sensitive data to the hackers responsible for the breach.
"Shell addressed the vulnerabilities with its service provider and cyber security team, and started an investigation to better understand the nature and extent of the incident," the company said, adding "there is no evidence of any impact to Shell’s core IT systems as the file transfer service is isolated [from Shell’s digital infrastructure]."
See: 6 free cybersecurity tools CISOs need to know about
March 1 analysis by security firm Mandiant Accellion identified two zero-day vulnerabilities that were part of the December Exploit—CVE-2021-27101 and CVE-2021-27104 (a SQL injection and OS command execution bug respectively)—and two zero-day vulnerabilities that were part of the January Exploit—CVE-2021-27102 and CVE-2021-27103 (A server-side request forgery and another OS command execution bug.)
The attackers exhibited a "high level of sophistication and deep familiarity with the inner workings of the Accellion FTA software, likely obtained through extensive reverse engineering of the software" Mandiant noted.
"Among the things the attacker had to know were: How to call internal APIs to obtain keys to decrypt filenames; how to forge tokens for internal API calls; how to chain together the vulnerabilities involved to conduct unauthenticated remote code execution; how to navigate FTA’s internal database, requiring a detailed understanding of the database structure; how to bypass FTA’s built-in anomaly detector."
After abusing the initial vulnerabilities, the attackers were able to execute their own commands, resulting in the creation of a web shell written to /home/seos/courier/oauth.api. They then used this to upload a custom, more full-fledged web shell which included "highly customized tooling designed to facilitate exfiltration of data"
The incident once again puts the spotlight on the security risks associated with third-party vendors and software supply chains. "Cyber security and personal data privacy are important for Shell and we work continuously to improve our information risk management practices. We will continue to monitor our IT systems and improve our security. We regret the concern and inconvenience this may cause affected parties" the supermajor said.








